Hinweis
Für den Zugriff auf diese Seite ist eine Autorisierung erforderlich. Sie können versuchen, sich anzumelden oder das Verzeichnis zu wechseln.
Für den Zugriff auf diese Seite ist eine Autorisierung erforderlich. Sie können versuchen, das Verzeichnis zu wechseln.
[Today's post comes to us courtesy of John Bay]
Summary
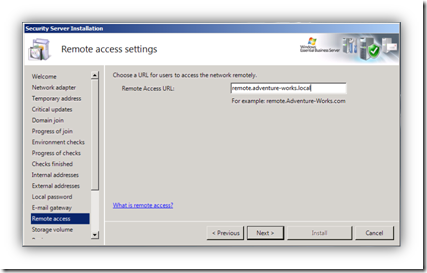
When Windows Essential Business Server installs, setup will generate a self-signed certificate name based on the name of you specify during installation. The certificate name will always be the name you selected for your remote access URL during setup. This URL is used for Remote Web Workplace (RWW), TS Gateway, /OWA, etc:
It may be desirable to change the name of this certificate or to replace this certificate with a certificate from a trusted authority. For instance, you may have installed EBS with a remote access URL of "remote.contoso.com" but later decide that you want to change the URL to "rww.contoso.com" or "mail.contoso.com". The other common scenario is that you may want to replace the self-signed certificate on the external interface with a public certificate, but retain the same FQDN. Both scenarios are covered in this document.
The remote access URL is used to publish the following virtual directories by default:
- Remote Web Workplace - /Remote/*
- Remote Web Workplace Robots.txt - /Remote/Robots.txt
- ActiveSync - /Microsoft-Server-ActiveSync/*
- Microsoft Exchange Outlook Anywhere and Terminal Services Gateway (RPC over HTTPS) - /rpc/*
- Microsoft Exchange Server Publishing: Outlook Web Access - /public/*, /OWA/*, /Exchweb/*, /Exchange/*
- If the SharePoint Add-in is installed, the default web listener will also publish its virtual directories
If you are replacing the certificate with a certificate from a trusted authority and already have the trusted certificate in a PFX formatted file, you can skip to step 1 in the section labeled “The following steps are accomplished on the Security server.”
More Information
The first step is to create the certificate with the desired name. This step is performed on the Management Server.
The following steps are accomplished on the Management Server.
1. On the Management Server, open Internet Information Services (IIS) Manager.
2. In IIS Manager Click on the Management server in tree in the left pane.
3. In the Features pane, double click on Server Certificates.
4. In the action pane, click Create Domain Certificate.
5. The create certificate wizard will appear. Fill out the certificate form with the appropriate information. When you are prompted to specify the Online Certificate Authority choose select and choose your internal certificate authority. In the Friendly Name field type the new name for the external certificate (i.e. www.contoso.com)
6. Once the wizard completes, the new certificate should be displayed in the list of certificates in IIS Manager. We need to export the certificate and import it into the store of the Security server. To export the certificate, right click on the certificate and choose export. Enter a filename and a password and choose OK to complete the export.
7. The certificate should now be exported to a file on Management server. We need to copy this file to a location that is accessible by the Security server.
The following steps are accomplished on the Security Server.
1. On the Security server, we need to open the certificate store for the local computer and import the certificate that we exported from the Management server. Run mmc.exe and select “ file” then “add/remove snap-in.”
2. Choose certificates and click add. When prompted, choose computer account.
3. Choose OK to return to the MMC.
4. Double click Certificates and Personal and then Certificates.
5. Right click on Certificates and choose All Tasks/Import
6. Browse to the file that you exported in Step 7 above or the PFX file that contains your public certificate.
7. Enter in the password for the file when prompted and finish out the wizard leaving all the settings as default.
8. At this point, the certificate is imported into the store on the Security server. Now we have to assign the certificate to the Web Listener in Forefront TMG. We need to open the Forefront TMG Management console.
9. Go to Firewall Policy and click on the Toolbox.
10. In the Toolbox go to Network Objects and expand Web Listeners.
11. Open the properties of the External Web Listener.
12. Go to the certificates tab
13. Choose select and pick the desired certificate.
Once the certificate is installed you should also change the public name on the web publishing rules to match the name of the public certificate.
1. Open the Forefront Threat Management Gateway console.
2. In the console tree, expand the name of your Security Server, and then click Firewall Policy.
3. In the results pane, double-click Remote Web Workplace Publishing Rule.
4. In Remote Web Workplace Publishing Rule Properties, click the Public Name tab.
5. Under Web sites and IP addresses, click your present remote name (for example, remote.contoso.com) and then click Edit.
6. In the Public Name dialog box, type a new public domain name and then click OK twice.
7. To save changes and update the configuration, in the results pane, click Apply.
The same change must be made on the following web publishing rules:
- Microsoft Exchange Server Publishing: Outlook Web Access
- Microsoft Exchange Outlook Anywhere and Terminal Services Gateway publishing Rule (RPC over HTTPS)
- Microsoft Exchange Active Sync Web Publishing Rule
- Server publishing rule to redirect to Remote Web Workplace
- Remote Web Workplace Robots.txt Publishing Rule
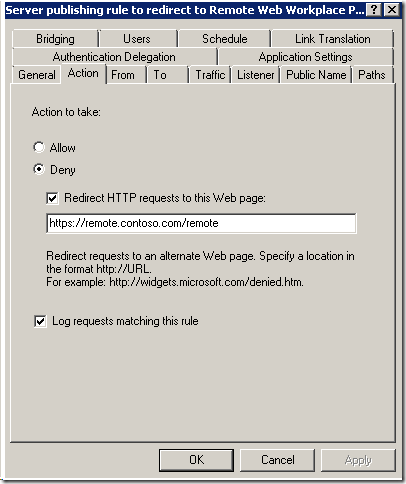
8. On the Server publishing rule to redirect to Remote Web Workplace deny rule, click on the Action tab and update the redirect URL:
Once the proper certificate is installed on the Security Server edit the MMS Configuration store in Active Directory to match the new certificate name.
1. On the Management Server, run adsiedit.msc
2. Right click on ADSI Edit in the left side of the console and choose Connect To.
3. Select a well known Naming Context and choose Configuration.
4. Double click Configuration
5. Double click CN=Configuration,DC=<localdomain> where “<localdomain>” is the entry for your EBS domain name.
6. Double-click Services
7. Double-click CN=MMSCONFIGURATION
8. Right-click on the object CN=ISASetupTask and choose properties
9. Double-click the keywords attribute
10. Highlight the Value RemoteAccess URL and choose Remove. Note: This will place the value in the editor. Do not exit or close the dialog at this point.
11. Edit the value for RemoteAccessURL to make it the new public name and click Add.
12. Click OK to exit the Multi-valued String Editor.
13. Choose OK and close out the MMC
Note: There is also a certificate installed in Exchange on the Security Server to enable secure SMTP communication (issued by the CA on Management Server). These steps do not update that certificate. Under normal circumstances, there is no need to modify the internal certificate.
Updated: 3/13/2009. Thanks to David Fabritius for his suggestion.
Comments
Anonymous
January 01, 2003
PingBack from http://www.safewordfordforcitrix.com/the-essential-business-server-team-blog-how-to-change-the-publicAnonymous
January 01, 2003
Sergio - any certificate you put in the same folder as CertificateInstaller.com will be published to the client's trusted root certificates container. The only requirement is that it is a root cert (i.e. not a leaf cert. ---MarkAnonymous
July 07, 2009
Hi, I need to know how to modified the CertificateInstaller to install the new modified certificate to use it en the client PC
![clip_image002[6]](https://msdntnarchive.z22.web.core.windows.net/media/TNBlogsFS/BlogFileStorage/blogs_technet/essentialbusinessserver/WindowsLiveWriter/HowToChangethePublicCertificateusedbyWin_B27/clip_image002%5B6%5D_thumb.jpg)
![clip_image004[4]](https://msdntnarchive.z22.web.core.windows.net/media/TNBlogsFS/BlogFileStorage/blogs_technet/essentialbusinessserver/WindowsLiveWriter/HowToChangethePublicCertificateusedbyWin_B27/clip_image004%5B4%5D_thumb.jpg)
![clip_image006[4]](https://msdntnarchive.z22.web.core.windows.net/media/TNBlogsFS/BlogFileStorage/blogs_technet/essentialbusinessserver/WindowsLiveWriter/HowToChangethePublicCertificateusedbyWin_B27/clip_image006%5B4%5D_thumb.jpg)
![clip_image008[4]](https://msdntnarchive.z22.web.core.windows.net/media/TNBlogsFS/BlogFileStorage/blogs_technet/essentialbusinessserver/WindowsLiveWriter/HowToChangethePublicCertificateusedbyWin_B27/clip_image008%5B4%5D_thumb.jpg)
![clip_image010[4]](https://msdntnarchive.z22.web.core.windows.net/media/TNBlogsFS/BlogFileStorage/blogs_technet/essentialbusinessserver/WindowsLiveWriter/HowToChangethePublicCertificateusedbyWin_B27/clip_image010%5B4%5D_thumb.jpg)
![clip_image012[4]](https://msdntnarchive.z22.web.core.windows.net/media/TNBlogsFS/BlogFileStorage/blogs_technet/essentialbusinessserver/WindowsLiveWriter/HowToChangethePublicCertificateusedbyWin_B27/clip_image012%5B4%5D_thumb.jpg)
![clip_image014[4]](https://msdntnarchive.z22.web.core.windows.net/media/TNBlogsFS/BlogFileStorage/blogs_technet/essentialbusinessserver/WindowsLiveWriter/HowToChangethePublicCertificateusedbyWin_B27/clip_image014%5B4%5D_thumb.jpg)
![clip_image016[4]](https://msdntnarchive.z22.web.core.windows.net/media/TNBlogsFS/BlogFileStorage/blogs_technet/essentialbusinessserver/WindowsLiveWriter/HowToChangethePublicCertificateusedbyWin_B27/clip_image016%5B4%5D_thumb.jpg)
![clip_image018[4]](https://msdntnarchive.z22.web.core.windows.net/media/TNBlogsFS/BlogFileStorage/blogs_technet/essentialbusinessserver/WindowsLiveWriter/HowToChangethePublicCertificateusedbyWin_B27/clip_image018%5B4%5D_thumb.jpg)
![clip_image020[4]](https://msdntnarchive.z22.web.core.windows.net/media/TNBlogsFS/BlogFileStorage/blogs_technet/essentialbusinessserver/WindowsLiveWriter/HowToChangethePublicCertificateusedbyWin_B27/clip_image020%5B4%5D_thumb.jpg)
![clip_image022[4]](https://msdntnarchive.z22.web.core.windows.net/media/TNBlogsFS/BlogFileStorage/blogs_technet/essentialbusinessserver/WindowsLiveWriter/HowToChangethePublicCertificateusedbyWin_B27/clip_image022%5B4%5D_thumb.jpg)
![clip_image024[4]](https://msdntnarchive.z22.web.core.windows.net/media/TNBlogsFS/BlogFileStorage/blogs_technet/essentialbusinessserver/WindowsLiveWriter/HowToChangethePublicCertificateusedbyWin_B27/clip_image024%5B4%5D_thumb.jpg)
![clip_image026[4]](https://msdntnarchive.z22.web.core.windows.net/media/TNBlogsFS/BlogFileStorage/blogs_technet/essentialbusinessserver/WindowsLiveWriter/HowToChangethePublicCertificateusedbyWin_B27/clip_image026%5B4%5D_thumb.jpg)
![clip_image028[4]](https://msdntnarchive.z22.web.core.windows.net/media/TNBlogsFS/BlogFileStorage/blogs_technet/essentialbusinessserver/WindowsLiveWriter/HowToChangethePublicCertificateusedbyWin_B27/clip_image028%5B4%5D_thumb.jpg)
![clip_image030[4]](https://msdntnarchive.z22.web.core.windows.net/media/TNBlogsFS/BlogFileStorage/blogs_technet/essentialbusinessserver/WindowsLiveWriter/HowToChangethePublicCertificateusedbyWin_B27/clip_image030%5B4%5D_thumb.jpg)
![clip_image032[4]](https://msdntnarchive.z22.web.core.windows.net/media/TNBlogsFS/BlogFileStorage/blogs_technet/essentialbusinessserver/WindowsLiveWriter/HowToChangethePublicCertificateusedbyWin_B27/clip_image032%5B4%5D_thumb.jpg)
![clip_image034[4]](https://msdntnarchive.z22.web.core.windows.net/media/TNBlogsFS/BlogFileStorage/blogs_technet/essentialbusinessserver/WindowsLiveWriter/HowToChangethePublicCertificateusedbyWin_B27/clip_image034%5B4%5D_thumb.jpg)