Convincing phishing message and how ATP helped the remediation
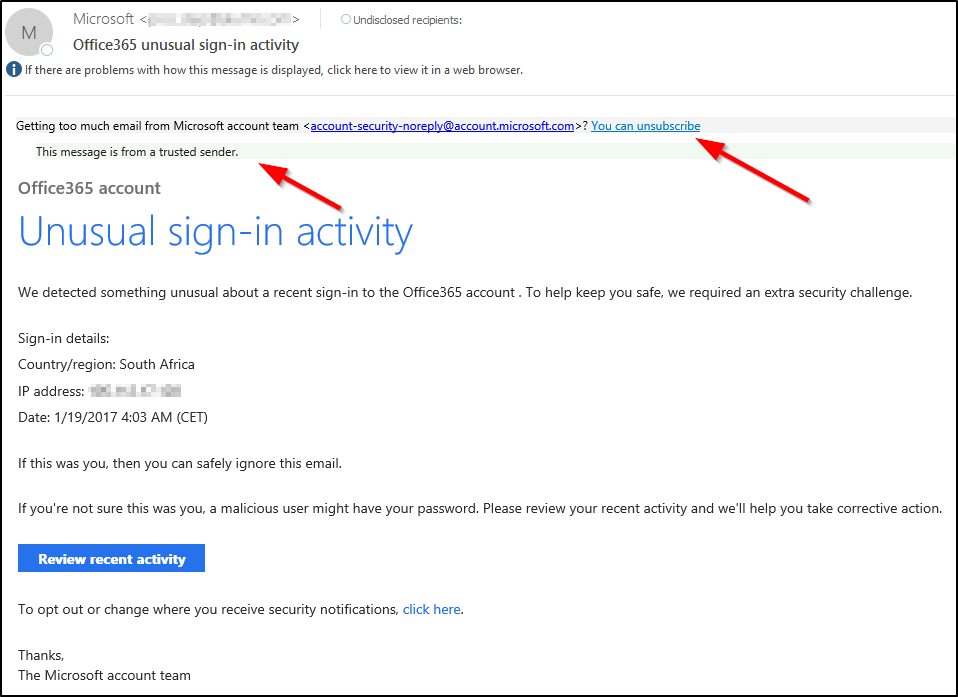
Phishing messages are continuing to evolve and look ever more convincing. It’s scary to see just how legitimate some of these messages can look. Last week I was working with an organization that received a phishing message that looked incredibly legitimate. What stood out for me the most, was that this message included fake Safety tips.
I have blurred the sending email address above but will tell you that the sending domain was comprised of random characters. The sending domain is controlled by the attacker and so SPF checks all pass. The display name, however, is Microsoft, and this is where the attacker is hoping to fool the recipient.
This attack was specifically targeted at the organization I worked with. Clicking the link in the message brought you to a sign-on page which included the organization's logo, and resembled a typical ADSF sign on page. There were a few hints that the site was malicious, one of them being that any text entered in the password field showed in the clear. Submitting your credentials through this site would give the attackers immediate access to your account.
White this attack was blocked quickly, the messages did reach end users at this organization and a hand full of them had their accounts compromised by entering their credentials on the malicious site. This organization uses Advanced Threat Protection, ATP, and was able to quickly look up how many users clicked the malicious link, and who they were.
Safety Tips
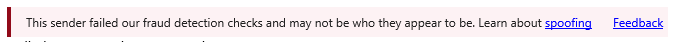
As of today, the only safety tip that we actually insert directly into a message is the Fraud warning.
Our other information tips will only appear in OWA and will appear outside of the message (above the subject). In the above phishing message, while you and I would know that a Trusted Sender banner won’t appear legitimately directly in a message, most end users will have no idea.
As end users are the last line of defense, user education becomes critical. While no amount of education will stop all users from clicking links in messages like the above, it can certainly decrease the number. With attacks ever evolving, the education piece needs to evolve with it and end users need to continually be reminded to be careful. Accomplishing this is no easy task, and so I will leave this up to you, the reader.
For more information on safety tips, see Email Safety Tips in Office 365.
Advanced Threat Protection Safe Links
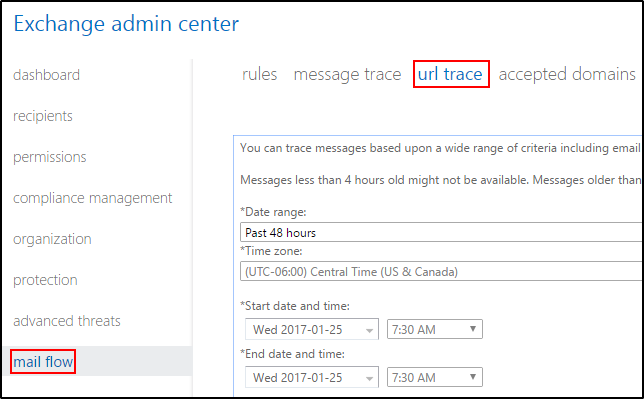
If you have Advanced Threat Protection in Exchange Online Protection and have configured a Safe Links policy that does not have the option, Do not track user clicks enabled, then you can track which users have clicked what links. To do so, run a URL Trace in the Exchange Online portal.
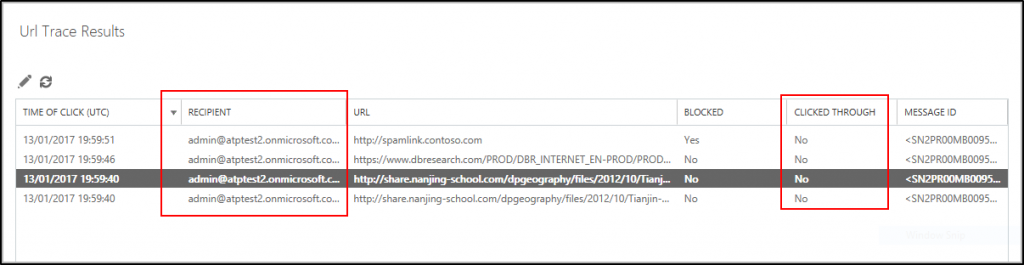
For this attack, we ran a URL trace scoped to the malicious URL and quickly found all users that clicked the link. Those users were immediately contacted to begin a remediation process. The results provided by the URL Trace will look something like this.
Straight up URL blocking isn’t very efficient with how easily an attacker can change the URL placed in a message. Protection technology is ever evolving, and yesterday we announced two new ATP features, URL Detonation, and Dynamic Delivery. You can find the announcement over on our Office Blog, Evolving Office 365 Advanced Threat Protection with URL Detonation and Dynamic Delivery.
Cheers,
Andrew
Other resources
Comments
- Anonymous
January 28, 2017
Thanks