Using DelegConfig version 2.0 (beta) tool for troubleshooting Kerberos Delegation issues
In april 2009, I posted an article on using Brian Murphy Booth's DelegConfig tool for troubleshooting Kerberos delegation issues.
Today I'll talk a bit about the version 2.0 of the tool which brings some cool new features and also supports IIS 7.0.
A full list of new features and changes can be found here: https://blogs.iis.net/brian-murphy-booth/archive/2009/04/22/delegconfig-v2-beta.aspx .
However, I will concentrate on the coolest new feature - The Wizard.
The version 2 of the tool is set up in the same way the previous version was, which is basically configuring it as an ASP.NET Application in your IIS Server (Steps 1 - 5 from my previous post still apply).
The difference is that now, using the wizard, you can analyze a front-end other than the HTTP application which ran under the same application pool as DelegConfig. For the other nodes/hops, you can follow the wizard all the way to the backend, specifying for each step the type of service, port, identity to receive in the end a nice report displaying all the recommendations but also the option to fix a few of the detected issues - SPNs, Trust for Delegation.
So, on the main page you will have links to: Wizard, SetSPN page that allows you to add or remove SPNs, SetDelegation page that allows you to modify the Delegation parameters in AD for an account, Tests page which allows you to do a quick test of authentication in a double hop scenario to a SQL Server, File Server or Web Server.
Accessing the Wizard, will get you started with the wizard.
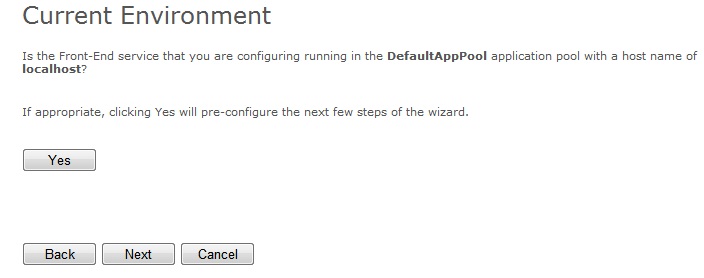
- 1. After clicking NEXT on the first page, you will be asked if the current application pool, the application pool under which we configured DelegConfig, represents our front-end. I will assume my front-end is actually on another machine, using a different account, so I will choose just Next without clicking the Yes Button (see below).
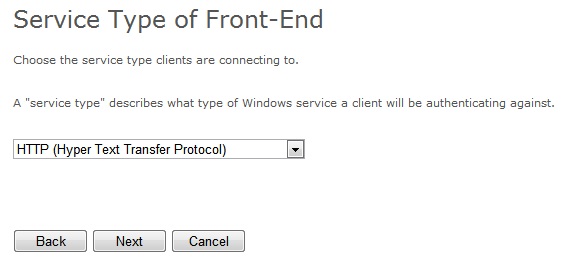
- 2. Service Type of Front-End page
This page allows me to configure the type of service for my front-end. I will assume for this example, an HTTP application.
- 3. Host Name
On this page we will configure the name used for accessing the service. If my http application would be configured with Host Headers so that the URL for the application would differ from the NetBIOS name, I would of course specify the HOST Header value. If my application would be published on https://contoso.internal.com/Front-End , the host name I would specify would be:Contoso.internal.com
- 4. Load Balanced.
This is a new feature allowing us check for configuration of Load Ballanced or Clustered services
- 5. Kernel Mode
If the service I'm adding currently is an HTTP class service, this page allows me to tell the wizard if I'm using the new IIS 7.0 feature called Kernel Mode Authentication (for more information: https://blogs.msdn.com/sudeepg/archive/2009/02/08/iis-7-kernel-mode-authentication.aspx ).
For this example I will assume I'm not using IIS 7 or Kernel Authentication.
- 6. Port Number or Instance Name
This page allows me to configure the port used by my service or the instance name.
- 7. Service Account Name
This is the identity of my service. The SPNs would have to exist under this account and if this service needs to delegate credentials further to another service, this account would also have to be trusted for delegation. If the identity is NETWORK SERVICE, LOCAL SYSTEM, LOCAL SERVICE, the wizard will check the host computer's machine account in Active Directory.
- 8. Trust for Delegation
This is the step where we tell the wizard if this is the last service in the chain or not. If this service needs to pass credentials further, we would respond "Yes" to the question: "Does the HTTP service running on emilianb07 need to delegate ("pass") credentials to another server?"

- 9. Delegation Type
If we use constrained delegation, we will select "Trust this account for delegation to specified services only", otherwise we select "Trust this account for delegation to any service (Kerberos only)"
What will happen now is that we will go through each step up to the 8th, to configure the 2-nd tier service. At the 8th Step we will be asked again if the service needs to delegate credentials further. If we answer yes, we will configure yet another service, with the same information - type, host, port, identity, etc. This repeats until we choose "No" at the step 8.
When this happens, the Next button will become "Finished" and when we click it, we will get our report.
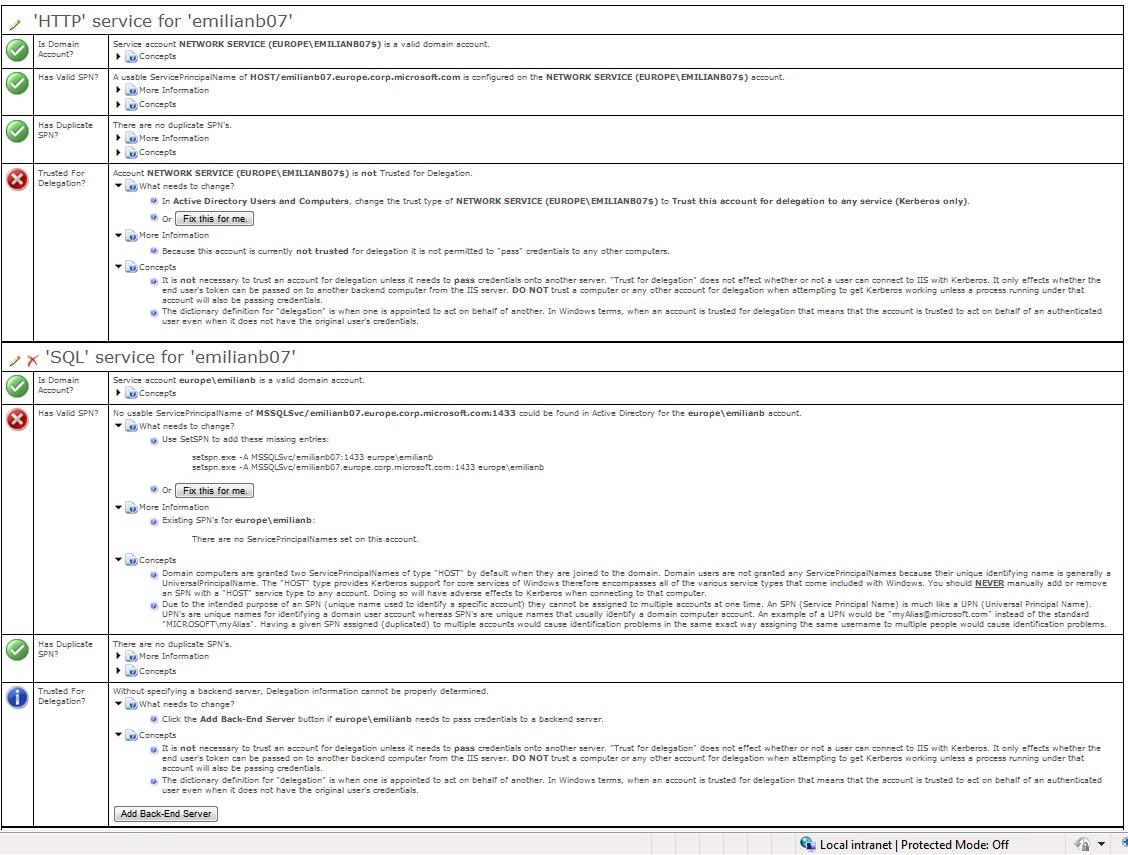
The report will have a section for each node/hop, where we will get answers to the following questions:
"Is Domain Account?", "Has valid SPN?", "Has duplicate SPN?", "Trusted for Delegation?". If duplicate or missing SPNs are found we have the possibility to fix this by clicking on the "Fix this for me." button which will take us to the SetSPN.aspx page. The page will already have filled the suggested SPNs to be added so all we need to have is an account with enough privileges on AD to do the change.

The Same thing applies to the "Trust for Delegation" part, which will take us to the Set/Delegation.aspx page.
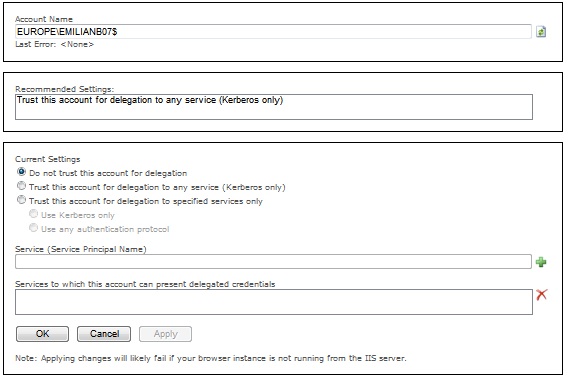
An "overall Status" paragraph contains answers to the questions: "Is Domain Account?" referring to the end user, "Authentication Method?", "Impersonation Level", "Will delegation Succeed".
However, if we run the delegconfig in an application pool other than the actual front-end and on a different machine, we can ignore this paragraph as it will actually check the Authentication method used for authenticating to the Tool itself rather than the actual front-end, and the impersonation level relative to the user accessing the DelegConfig tool. Therefore, the answer to the question "Will Delegation Succeed?" might not apply to the actual environment.
HTH,
Emi