Powerful but not-so-obvious benefits of DirectAccess “manage-out” capabilities
Over the past nine months, we have been working with early adopters of UAG DirectAccess as they discover, test, and deploy DirectAccess. One of the things that we are noticing more and more is that there are several aspects of DirectAccess that are not immediately obvious but that turn out to make a real difference to IT Pros and Information Security professionals. I thought I would describe some of these not-so-obvious aspects, and you will be able to see why they can be so attractive.
Normally, Information Security people view remote access technologies like VPNs as an annoyance – something that needs to be secured but without much security benefit. But DirectAccess can be different; although it will definitely be a little bit scary because there is a lot of technology that may be unfamiliar, it also offers a lot of additional potential to improve overall security. Here’s why:
DirectAccess is always on, and this means you can manage your roaming laptops whenever they connect to the internet, not just when their users decide to bring up a VPN connection
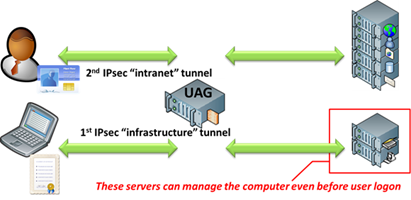
This is the whole “manage out” value of DirectAccess. There are two IPSec tunnels involved in DirectAccess. The first infrastructure tunnel is active right from when the lid of the laptop is lifted and an internet connection is available. It requires a computer certificate issued by you to be present on the laptop and the laptop must be a valid domain member of your Active Directory. This connectivity is narrow in scope and only allows connectivity to key infrastructure and management servers. The second, wider-scope tunnel opens once the user logs on. This requires the computer certificate, the user’s Kerberos logon, and optionally smartcard use or NAP health certificate. This intranet tunnel allows access to the data and resource servers on the intranet that a user may want to access.
So even before a user logs onto a laptop, the DirectAccess infrastructure tunnel springs into life and by default allows visibility of your internal DNS servers and some Active Directory domain controllers. You can also place additional management servers into this tunnel to suit your manage-out needs.
The early availability of this connectivity to internal resources means:
- Your computers can get GPOs right when they first boot, including things like computer startup scripts
- You can include your software distribution solution, like System Center Configuration Manager, into that first tunnel so the laptop can be patched and inventoried even when it is remote
- Your roaming laptops can pull patches from an internal Windows Software Update Services deployment, and can contact internal antivirus services for critical updates.
- Tools that reach out to the users’ computers, like vulnerability scanners, can get vastly improved chances of success in scanning roaming laptops
Activities that need users to be connected to the intranet work seamlessly: these will work even when the user does not know how to bring up a VPN connection
There are several activities that would work nicely if the user had brought up a VPN beforehand. These things will all work without any user procedures under DirectAccess. Examples of these types of activity are:
- Windows 7 and Office activation processes will be able to communicate with internal activation servers
- Bitlocker and Bitlocker-to-go key archival can work directly against Active Directory, so users’ Bitlocker keys can be safely stored away even when they trigger the encryption while they are remote
Password changes and resets can now work with roaming laptops
There are two common problems with password changes that really affect remote users.
The first is password resets for remote users. Users that forget their password or get locked out while remote will call the helpdesk, but if the user has no visibility of a Domain Controller, performing a password reset in Active Directory will not help the user unless he comes in and connects to the internal network. A user that cannot bring up a VPN because he cannot log in will not be able to use the VPN to get connected. But with DirectAccess, the user has visibility of a Domain Controller right from the CTRL-ALT-DEL prompt, so a password reset made by the helpdesk will be instantly visible to the end user. You should even be able to expose the Forefront Identity Manager self-service password reset portal through the DirectAccess infrastructure tunnel so that users can even reset their own passwords while roaming the internet.
The second is password changes by remote users. A roaming laptop user that changes a password in OWA will have this password change sent to Active Directory. But it will not affect the cached credentials on their laptop. The next time the user logs on, and tries to use his or her “new password”, the logon against the laptop cached credentials will fail unless the laptop is now attached directly to the intranet. With DirectAccess, a user can always change a password right from the CTRL-ALT-DEL prompt.
Additionally, computer account password changes, which happen every 30 days by default, would work correctly on a DirectAccess-enabled laptop, even for users that would almost never bring up their VPN. This can prevent legitimate computer accounts from being cleaned up by any AD cleanup activities that internal IT Pros may run.
Summary
If you think about all of the items above, you can see that always-on, seamless connectivity, available right from the CTRL-ALT-DEL prompt, can result in a more secure overall environment and can address several password handling scenarios that are not possible with a traditional VPN. Some of our customers are now deploying DirectAccess in a “manage-out-only” configuration where they are not even exposing the remote connectivity capabilities to their users – the manage-out capabilities are so powerful on their own, the other half of DirectAccess is not even needed to justify its deployment.
With DirectAccess, you will be able to answer the question, “how many of our laptops have received the antivirus update that covers ‘malware X’” with confidence, and you will not have to worry about your CIO forgetting her password while she is visiting Tuktoyaktuk.
Author:
Pat Telford, Principal Consultant, Microsoft