How to configure Forefront TMG to block AD users from accessing internal resources
The secure socket tunneling protocol (SSTP) allows Web users authenticated by the Forefront UAG portal to access the published remote network. You can use Forefront TMG on UAG to configure who has access to what over SSTP VPN. In this example, we’ll block a specific user/group from accessing the entire Internal network on all protocols. You can also select specific protocols to block.
Note: You have to have a working AD with the previously defined users/groups to who you want to deny SSTP services connection.
Procedure:
1. Open the Forefront TMG Management console:
2. Right-click the Firewall Policy mode, select New, select Access Rule.
3. Give the rule a name, such as SSTP Block, and click Next.
4. On the Rule Action page, select Deny, and click Next. When rule conditions are met, access will be denied.
5. On the Protocols page, select All Outbound traffic, and click Next.
Note: This is the point in the procedure where you can choose a more granular approach – specify protocols you want to block.
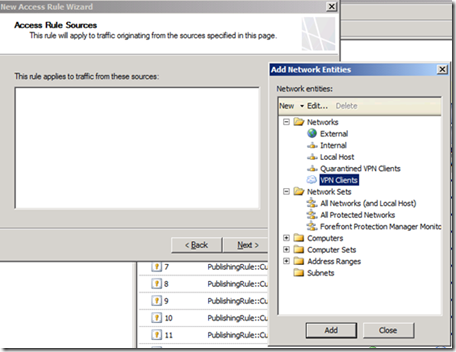
6. On the Access Rule Sources page, click Add, and from Networks, select VPN Clients.
7. Click Next.
8. On the Access Rule Destinations page, click Add, and select Internal from the list of Networks, and click Next.
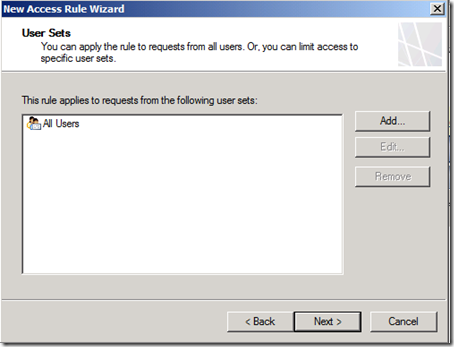
9. On the User Sets page shown below we’ll actually configure what we’ve set out to do – block specific users. Select All Users and click Remove.
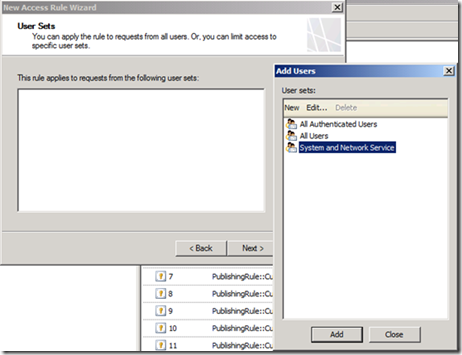
10. Click Add, and on the Add Users dialog box shown below, select New. This kicks off the New User Set wizard. Name the new user set SSTP Deny.
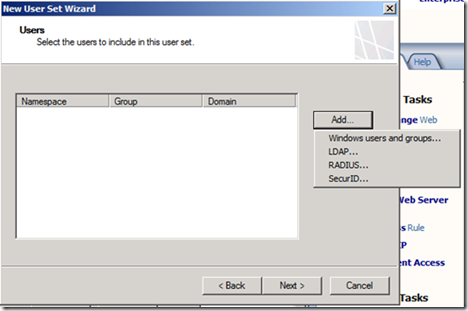
11. On the Users page, click Add, and select Windows users and groups.
12. Browse to the right user/group, confirm it with the picker dialog, and close all of the dialogs. Click Next and complete the New User Set wizard.
13. Back in the New Access Rule wizard User Sets page, you can select the new user set, click Next and Finish to finalize the rule. You’ll also have to click Apply in the Forefront TMG console.
Remember, Forefront TMG rules are ordered, so if this rule is not near the top and another rule has these conditions and allows access, the request won’t even get to this rule denying access. So make sure this rule is at or near the top. You can read more about Forefront TMG access rules on TechNet.
You're done!
Daniel Slabodar, Automation and performance test engineer
Nathan Bigman, Content Publishing Manager, Anywhere Access Team
Comments
- Anonymous
June 19, 2010
Well, i am surprised that how UAG team has neglected an important point in this article that UAG rearranges the TMG rules when activating the configuration. This will cause any TMG custom rule written at top to come to bottom which will make the rule ineffective if their is already another rule created for the same within the UAG Anchor rules. This has not been fixed in UP1 and i am not sure if MS has any plans fixing this in SP1 .. Please confirm if possible,