Considerations for Exchange Publishing
UAG does a great job of streamlining secure messaging, with a publishing experience that is framed into a set of easy to follow steps. Nonetheless, before you start there are a couple of considerations to bear in mind:
- Choosing between a dedicated mail trunk or mail applications contained in a UAG portal
- Selecting Exchange mail applications available to end-users
- Deploying the authentication method that is right for your organization
Dedicated Mail Trunk or a UAG portal
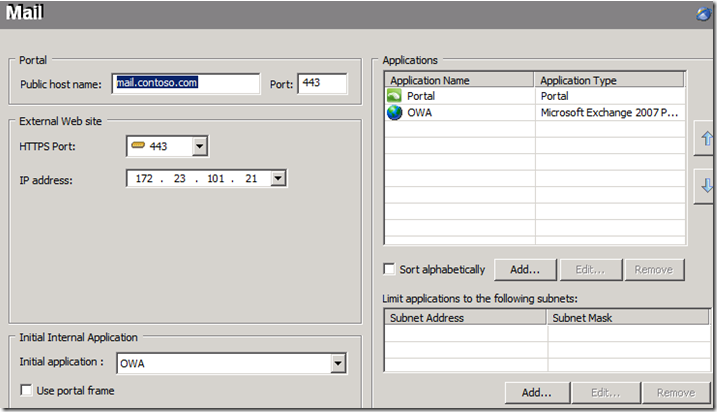
Having a dedicated mail trunk means a designated FQDN (e.g. https://mail.contoso.com/) that will serve mail applications, exclusively. This can be very convenient for end-users, regardless of their device or platform - ActiveSync on a mobile device, Outlook client or Outlook Web Access – mail is served using a single domain name. However, you will need a certificate for this FQDN that will reside on both UAG and the Exchange Client Access Server.
Figure 1. Dedicated Mail Trunk
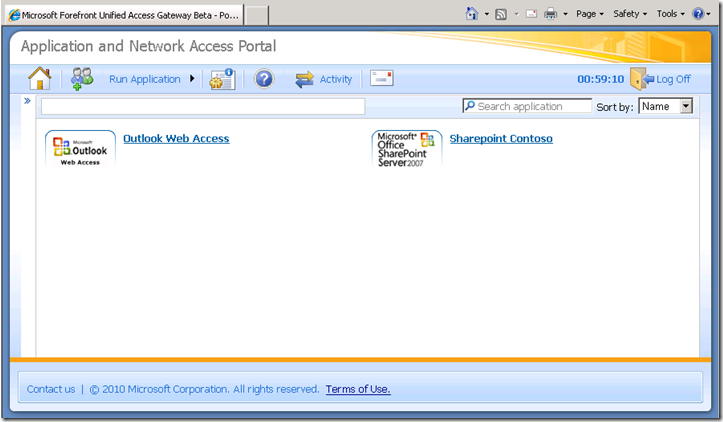
Instead of having a dedicated mail trunk, you may wish to go with a UAG portal (e.g. https://access.contoso.com/). Such a portal is used as a container, with Exchange as one of many other applications. In the following example, SharePoint is published alongside Exchange.
Figure 2. Portal Containing Outlook Web Access and SharePoint
What impact will a portal have on messaging user-experience? For one thing, Outlook Web Access will be contained inside a portal frame, with no need to re-login when SSO is used. For OutlookAnywhere and ActiveSync the experience is identical to a dedicated mail trunk, with the portal playing no role in their interactions.
Selecting Exchange Applications
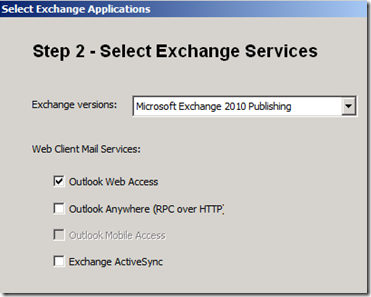
Ultimately, the published mail applications are a derived choice of end-points’ devices and company policies. UAG public beta covers Outlook Web Access, ActiveSync and OutlookAnywhere. What is missing? Exchange Web Services. We plan on adding full support to their out of the box publishing in the UAG release candidate.
Figure 3. Choose Exchange Applications on UAG Beta
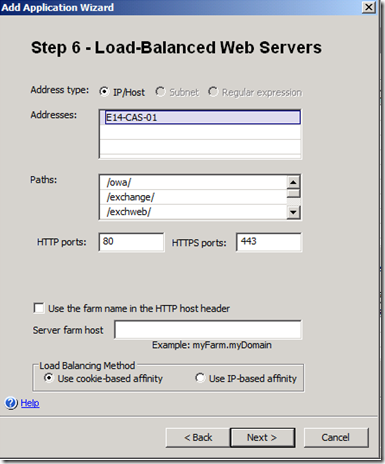
You can either select to publish all applications at once, or run the wizard multiple times, one per desired application. Why would you do the latter instead of the former? Well, since each time you publish an application you have the opportunity to specify back-end parameters, this gives you the flexibility to use a different back-end configuration per Exchange application. For example, use cookie-based affinity for Outlook Web Access and IP-based affinity for OutlookAnywhere.
Figure 4. Setting Back-end Affinity
Choosing an authentication method
Many factors influence selection of an authentication method, as on-top of the technological considerations, you have regulation, policies and end-users’ experience.
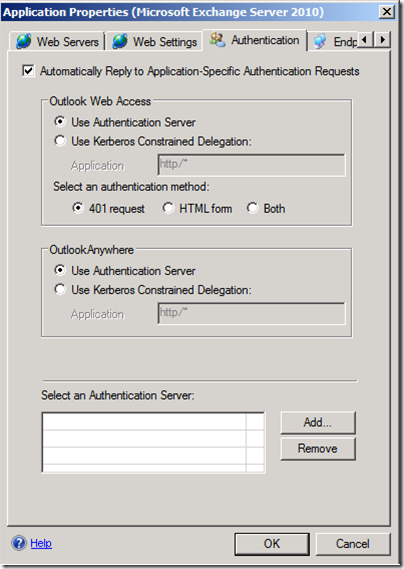
UAG does offer a wide variety of authentication methods. Using the public beta you can deploy basic pre-authentication or 2 factor authentication, while the release candidate is planned to extend that with NTLM authentication against the gateway (and Kerberos constraint delegation against the Exchange Client Access Server).
Figure 5. Exchange Applications Authentication on UAG Release Candidate (RC)
Conclusions
Forefront UAG represents a step forward in satisfying inbound access needs of organizations. Particularly, we have invested heavily in Exchange publishing scenarios, providing a wide range of ways to accomplish secure messaging. However, you do need to share the action with us, making the choices that are right for your enterprise prior to engaging the deployment.
Michel Biton
Comments
- Anonymous
May 16, 2014
We’ve gathered the top Microsoft Support solutions for the most common issues experienced when - Anonymous
July 21, 2014
We’ve gathered the top Microsoft Support solutions for the most common issues experienced when