Authenticating Exchange Mail Applications using UAG RC0
Technorati Tags: Authenticating Exchange,RC0,Exchange authentication,Authentication,Exchange
Secured messaging has just become easier with the recently announced RC0 version of Forefront UAG. Additional authentication methods are supported out of the box, simplifying the publishing process of back-end services, particularly Exchange mail.
Objective
Configure pre-authentication of Exchange mail applications, with no impact on the end-users, providing a seamless experience. Both the login process and the session itself are intact from an end-user perspective, having the extra layer of security with Exchange experience preserved.
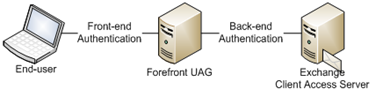
Here is an illustration of the authentication entities:
[Figure 1. Authentication entities]
We will illustrate how to accomplish the objective using the following authentication matrix (this is merely an example as the authentication alternatives/combinations are much greater).
Exchange mail application |
Front-end Authentication |
Back-end Authentication |
Outlook Web Access |
Form-based |
Basic (401) |
Outlook Anywhere and Web Services (excluding Autodiscover) |
NTLM |
KCD |
Autodiscover Service |
Basic |
Basic |
ActiveSync |
Basic |
Basic |
Outlook Web Access
The pre-authentication process is transparent to end-users, as they are being presented with a form-based login page (optionally identical to the OWA one), and using the client's approved credentials, standard basic authentication (HTTP 401) is used to authenticate with the Exchange Client Access Server (CAS).
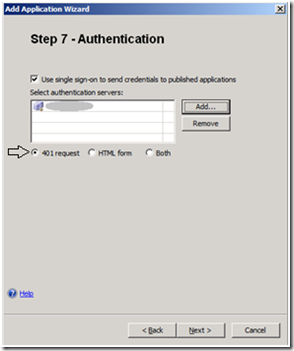
You can configure this by creating a new Portaltrunk, and selecting Publish Exchange applications , or by Adding an application to an existing trunk. When you reach the Authentication property page configure UAG to negotiate with the CAS by selecting 401 request . See Figure 2 below.
[Figure 2. Modify UAG back-end authentication method]
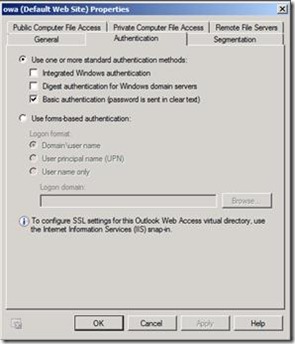
The above UAG configuration also requires you to configure the CAS to perform Basic authentication. From the Exchange Management Console, click on OWA properties, click the Authentication tab, and click Basic Authentication, See Figure 3 below.
[Figure 3. Modifying the CAS to accept Basic authentication for OWA]
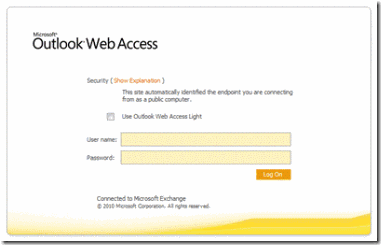
To perform Form-Based Authentication using the OWA look & feel (instead of the UAG one), see Figure 4, select Configure on the published trunk, click the Authentication tab, and click Apply an Outlook Web Access Look and Feel.
[Figure 4. OWA Look & Feel]
Outlook Anywhere
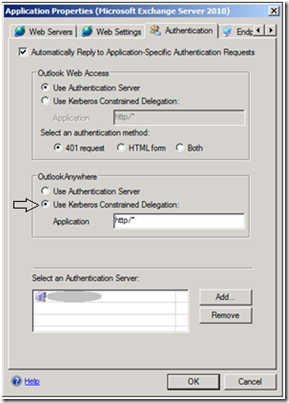
Outlook clients provide a seamless authentication experience when configured to authenticate using NTLM. In this scenario, NTLM is the chosen authentication method between the client and UAG. Afterwards UAG requests a Kerberos ticket on behalf of the client. To enable Kerberos Constraint Delegation (KCD) in UAG, you need to modify the default authentication method for Outlook Anywhere. Select the Exchange application, click Edit and navigate to the Authentication property page, as shown in figure 5:
[Figure 5. Select KCD for Outlook Anywhere]
An extra level of authentication granularity is provided by allowing administrators to modify the authentication method of Exchange Web Services. These services play an important role in providing a rich experience for Outlook clients (they can also be used for building custom applications against Exchange).
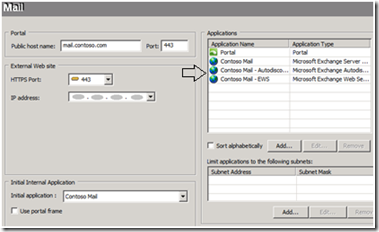
Web Services are published by UAG automatically when publishing Outlook Anywhere. In figure 6 you can see the different Exchange applications, two of which were auto-published by UAG.
[Figure 6. Auto-published Exchange Web Services application]
This step in the Add applications wizard (when Outlook Anywhere is published) lets you selectthe authentication method for Exchange Web Services. It is recommended that select either Use Authentication Server(Basic using the repository defined in step 7, see Figure 2), or Use Kerberos Constrained Delegation. See figure 7. Selecting Do not Reply, instructs UAG to work in a pass-through mode against the back-end (for a full pass-through you will also need to eliminate the front-end authentication).
[Figure 7. Configuring Web Services Authentication]
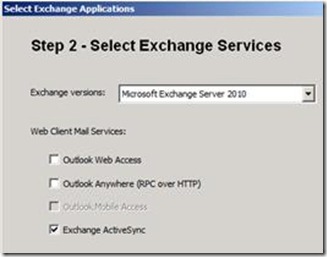
ActiveSync
By default Basic authentication is deployed simply by selecting to publish Exchange ActiveSync. (See Figure 8. Publish Activesync)
[Figure 8. Publish ActiveSync]
Publishing Prerequisites
Things to consider before you begin publishing any of the above mail applications:
· The CAS certificate must reside on the Forefront UAG server.
· Kerberos Constraint Delegation requires that the Forefront UAG server and Exchange CAS are members of the same domain, and enabling delegation for the UAG server in the domain controller
· If Exchange is your only published application in a trunk, you may choose to have it marked as the initial application (see Initial application combo-box in Figure 4).
More information
We have updated the Exchange publishing guide using Forefront UAG.
Michel Biton
Comments
Anonymous
October 12, 2009
Will UAG support certificate authentication through Active Sync?Anonymous
October 13, 2009
This will not be supported in UAGAnonymous
November 17, 2009
I am not too familiar with UAG, but after reading this article I feel comfortable with this process. Thanks for sharing, you definitely taught me a lesson today.Anonymous
February 21, 2014
We’ve gathered the top Microsoft Support solutions to the most common issues experienced usingAnonymous
May 16, 2014
We’ve gathered the top Microsoft Support solutions for the most common issues experienced whenAnonymous
May 16, 2014
We’ve gathered the top Microsoft Support solutions for the most common issues experienced whenAnonymous
July 21, 2014
We’ve gathered the top Microsoft Support solutions for the most common issues experienced whenAnonymous
July 21, 2014
We’ve gathered the top Microsoft Support solutions for the most common issues experienced when