Windows Update for Business explained
* UPDATE * For more details, please visit the official Technet page about Windows Update for Business.
Hi Windows lovers and IT pros!
Today I want to make a quick jump of what a lot of us was waiting for: Windows Update for Business (WUfB).
To be clear, WUfB is not a WSUS in the cloud. And some of you were maybe expecting something like a SaaS version of WSUS but WUfB is still a cloud service which leverages the power of Windows Update services.
What WUfB brings is, is a way to control how to deliver security updates and features upgrades within your infrastructure while connecting directly to Windows Update. WUfB helps you create rings (see computer groups) by delaying delivery of updates/upgrades. Last but not least, you have an option to pause the deployment of updates and upgrades!
And for the bandwidth management (since you're connecting to a cloud service and not your local WSUS server), you have the peer to peer update feature introduced in RTM version of Windows 10 to limit Internet access for downloading updates and upgrades.
So if WUfB is not a WSUS in the cloud, how can we do what I explained above? The response is: it’s all done on the client side and controlled by 2 ways: GPO or MDM.
The GPO way
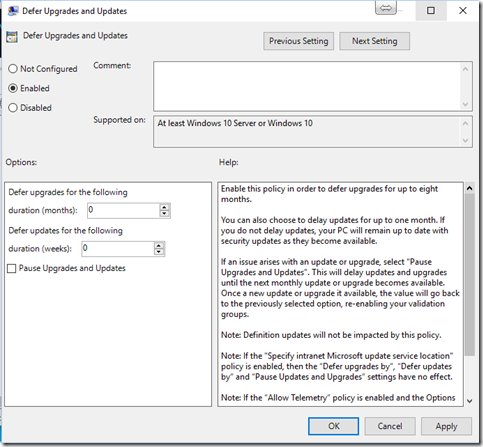
Windows 10 November Update has been recently released on November 12 and with that recent update, we have introduced a new GPO settings call “Defer Upgrades and Updates”.
To see what that setting looks like, open “Local Group Policy Editor” (Run –>gpedit.msc) and browse to “Computer Configuration” –> “Administrative Templates” –> “Windows Components” –> “Windows Update” and you will find the below screen.
The new “Defer Upgrades and Updates” introduces 3 new options:
- Defer upgrades up to 8 months (1 month increment)
- Defer updates up to 4 weeks (1 week increment)
- Pause Upgrades and Updates until the next update/upgrade release (around 30 days)
Important note: You can’t use those settings in conjunction with WSUS. if you specify an internal update service location, above settings will be ignored.
Additional note: By just enabling this GPO setting and not delaying anything (leaving both durations to 0), it will turn the target computers to CBB (Like the old GPO setting “Defer Upgrade” was doing in the Windows 10 RTM build).
The MDM way
What we could configure through GPO above, we can do it as well with MDM style (Mobile Device Management). As you might know, MDM solutions (in my example, I used Microsoft Intune) will modify values of Windows CSP. Windows CSP are some kind of a management interface for Windows.
You can find a complete list of Windows 10 CSP on the following site.
Here’s the detail about the new 3 settings introduced by WUfB:
In Intune, I created a new Windows 10 Custom Configuration Policy and add the below OMA-URI settings to defer upgrades by 2 months:
The same goes for the other 2 settings.
Don’t use those new settings with WSUS/SCCM
The last important thing I want to remind is that, if you’re already using an on-prem solution to manage Windows updates/upgrades, do not use the new WUfB settings. To manage updates, you have 2 solutions then:
- Use WSUS (or SCCM) and manage how and when you want to deploy updates and upgrades to Windows 10 computers in your environment (in your intranet).
- Use the new WUfB settings to manage how and when you want to deploy updates and upgrades to Windows 10 computers in your environment directly connecting to Windows Update.
Comments
Anonymous
November 16, 2015
Finally! A technical article that describes what Windows Update for Business is all about! We appreciate this information. From an enterprise point of view, we want to take advantage of WSUS as much as possible but are having problems with distributing the Win10 Feature Upgrade (1511). Most of our WSUS Servers are 2008 R2, which does not have a patch available for distributing Win10 Feature Upgrades. Also, the large size of the 1511 Feature Upgrade will take a toll on the disk space of our WSUS servers and also our networks. You mention not mixing WSUS and WUfB settings. However, we would have a use for distributing Security Updates via WSUS and Feature Upgrades via WUfB. Could this be possible, if not now, in a future version of Win10?Anonymous
November 16, 2015
Any plans to support this in 2012r2?Anonymous
November 16, 2015
As John stated this technical article about Windows Update for Business is really appreciated. Finally some real information we can distribute and share with clients and customers :)Anonymous
November 16, 2015
Thanks for the info, again. Seriously appreciated!!!Anonymous
November 16, 2015
this is disappointing , windows update for businesses turned to be just smoe GPO settingsAnonymous
November 16, 2015
Well, I would disagree with the comment that it's not a cloud service - because it uses the Windows Update service, which is the "original" and probably still one of the biggest cloud services anywhere.Anonymous
November 16, 2015
I agree Michael that it uses Windows Updates which is a cloud service. What i wanted to point out is that it's not a WSUS in the cloud but a way to manage updates and upgrades deployment from client side while using WU :) gonna correct the terms I used.Anonymous
November 16, 2015
will this also fix the issue, that if a patch is set to have a deadline on wsus, Widows 10 (10240) will immeadiatly install this patch and force reboot in 10min only ? Even if deadline is still in future and also if patch is e.g for office.Anonymous
November 16, 2015
Hi Samir, this is progress - but for enterprise, we need more granularity. In an ideal world, I would like to see a distinction made for drivers - IE different polices for updates, drivers and upgrades. I would also like the ability to block known bad updates/drivers/upgrades by entering the unique ID into some new GPO. Anyone from Microsoft reading this take note. Enterprise customers require a little more control - not WSUS levels - but a little more.Anonymous
November 18, 2015
The comment has been removedAnonymous
November 20, 2015
Windows 10 does not respect the following group policy: "No auto-restart with logged on users for scheduled automatic updates installations". Without this option, there is no way to prevent Windows from automatically rebooting when users have files/applications open. This is a serious data loss bug that should be fixed. See the following thread for more information: community.spiceworks.com/.../1156819-windows-10-ignoring-no-auto-restart-with-logged-on-usersAnonymous
November 23, 2015
Regarding the last thing about SCCM. This "(in your intranet)." What will happen if a client is not connected to the intranet? Will update just install ?Anonymous
November 24, 2015
There is a hotfix for WSUS available now to deploy Windows 10 "features". Here's a link... support.microsoft.com/.../3095113Anonymous
November 24, 2015
Can you confirm three things: 1: When a beta of WUfB will be available? 2: If we shut down WSUS and start using WUfB will the DEFER UPDATES option apply to ONLY Win10 machines or will it apply to Win7 & 8 as well? (Because we apparently can not use both together) 3: Is there ANY way in WUfB to avoid AUTOMATIC updates? Our users run complex scientific jobs that can take weeks of 24 hour processing at the desktop to complete so we only patch 3 times per year and provide lots of notice to staff. We just cannot allow Windows to cycle or even require a log out everyone month. ThanksAnonymous
November 25, 2015
use WUfB instead of WSUS is not a real option
- no controll / feedback if e.g patch failed and never was installed.
- bandwidht usage (cause leach from WWW instead locall lan)
Anonymous
November 25, 2015
bandwitdh issue should be solved by the "delivery optimization" set to LAN but "no feedback if patch failed" issue is a showstopperAnonymous
January 08, 2016
Tried to enable this feature using the GPO way. As a result I expected to see the "defer upgrades" checked and grayed out (as it happens with others GPO settings) but it's not. It's just me?Anonymous
January 25, 2016
@ciapame - if you deployed the GPO setting correctly, it will be grayed outAnonymous
July 14, 2016
Thank you Samir for this article, quite resourcefulAnonymous
September 12, 2016
IMPORTANT INFORMATION: WUfB is not compatible with the Intune client software.You can go arround by setting the registry entry UseWUServer to 0 with a GPO but it isn't clean, the value will change every time the intune client tries to update windows.