Fun with the Kerberos Delegation Web Site
Hi, Rob here. First I want to thank you guys for reading and participating in our blogging efforts. I had one of you e-mail us and ask about the web site I used in the Kerberos Authentication Troubleshooting blogs and if they could get a copy of it.
The web site was created by our IIS support counterparts and it turns out it was released to the web as DelegConfig. Brian Murphy-Booth has a blog about the web site here. We at AskDS do not support the DelegConfig web site, so if you have questions or comments about it leave your feedback at that blog location.
With this web site you can test Kerberos double hop configurations and the newer delegation types of constrained delegation and constrained delegation with protocol transition from IIS to the following services: SQL, File Server, OLAP Server, or another web server. The reason why this documentation exists is to help customers configure Kerberos delegation to become familiar with all the tasks involved to configure the environment correctly.
Pre-Flight Check-List
- Active Directory Domain Functional Level must be Windows Server 2003 if you want to test constrained delegation.
- Name resolution (WINS or DNS) is properly working in the environment.
- All computers are within five minutes of time to each other.
- All service accounts and server computer accounts (IIS and backend) must exist in the same domain if you are going to configure constrained delegation. Note that the user accessing the resource can be in any domain where Kerberos functions to the domain where the IIS and backend servers exist.
- If you are going to test cross-forest Kerberos authentication or delegation then a working two-way forest trust must exist.
- The test user account that is going to be delegated must not have the account option Account is sensitive and cannot be delegated configured. You will find this in the Active Directory Users and Computers on the user’s Account tab under the Account options heading.
- The default web site in IIS allows Kerberos authentication to be used. If you are not sure review KB 215383.
- You are using IIS 6 with the ASP.NET component installed.
- You have installed the backend application or service that you want to test.
NOTE: Review Setup and Known issues.txt from the DelegConfig.zip file for proper ASP.NET version to be installed on the IIS Server.
Configuring the Web site and Web Application Pool Account
Extract the zip file to a directory on a server running IIS 6. You can specify any location you wish. According to the DelegConfig blog it can be used with IIS 7 however, we are only going to be showing how to configure it with IIS 6.
- When you extract the web site, you need to preserve the folder structure.
- The server running IIS and back-end service should be installed on separate boxes.
- You need to have the ASP.NET component checked in Application Server when you install IIS.
Open Active Directory Users and Computers to create the application pool account.
- We need to create a domain account that will be used for the application pool in IIS. You can name the account anything you wish, for this document we will use the account IISKerbSvc.
- You will need to configure a password for the service account. Also, you should configure the account’s password to never expire. This is configured under the Account tab.
Open IIS Manager to add a virtual directory.
- With the Default Web Site highlighted, right-click and select New, then select Virtual Directory.
- The Virtual Directory Creation Wizard will start, click Next and specify an Alias. For this demo I used KerbDeleg. Then click Next.
- Navigate to the path folder where you extracted the files for DelegConfig.zip, then click Next.
- Choose the defaults and click Next then click Finish.
Now that you have a Virtual Directory named KerbDeleg you need to create an application pool for the web site to use.
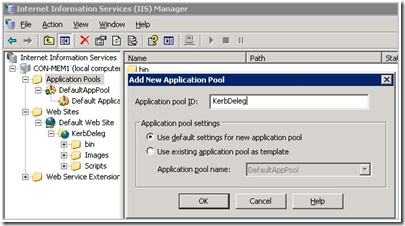
Figure 1 - Creating a new application pool for the web applicationRight-click Application Pools and select New then select Application Pool.
The Application Pool ID canbe anything and does not have to match the virtual directory name. For this demo I used KerbDeleg. Just name it something unique.
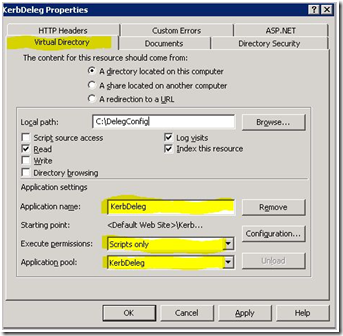
Once you have the virtual directory and the application pool created, you need to make modifications to the virtual directory that we created in Step 3.
Right-click the virtual directory you created in Step 4 (KerbDeleg).
Select Properties.
On the Virtual Directory tab click Create.
Change the Application Pool used via the drop-down menu to the one created in Step 4 (KerbDeleg). Note that by default it will be DefaultAppPool.
Make sure Execute permissions is set to Scripts only.
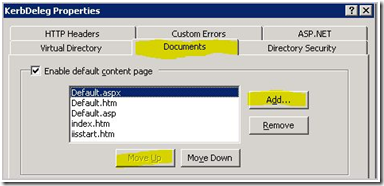
Click the Documents tab, and select Add.
Type Default.aspx in the dialog box and click OK.
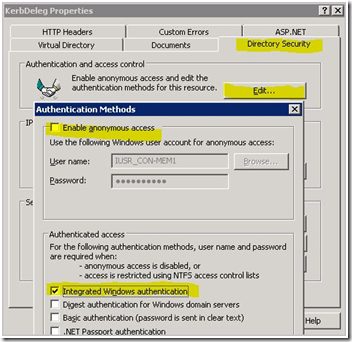
Select the Directory Security tab.
Under Authentication and access control click Edit button.
Uncheck Enable anonymous access, and check Integrated Windows authentication.
Click OK twice.
Now we need to change the Identity used by the application pool that we created in Step 4 (KerbDeleg).
Right click on the application Pool you created. In this documentation it is "KerbDeleg", and select "Properties"
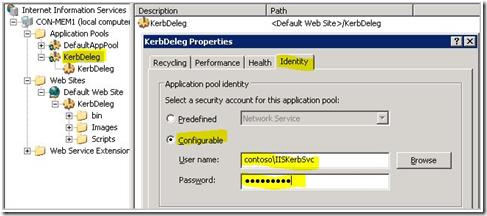 Figure5 - Changing the application pool identity to a service account
Figure5 - Changing the application pool identity to a service accountSelect the Identity tab.
Select Configurable and find the account we created in Step 3 (IISKerbSvc).
Once you have selected the user account and typed in the password for the account, click OK.
Now, we need to add the user account from Step 2 (IISKerbSvc) to the computer local group IIS_WPG.
If the server running IIS is a member server, use Compmgmt.msc (Computer Management).
If the server running IIS is a domain controller, use Dsa.msc (Active Directory Users and Computers) and this group is located in the Users container.
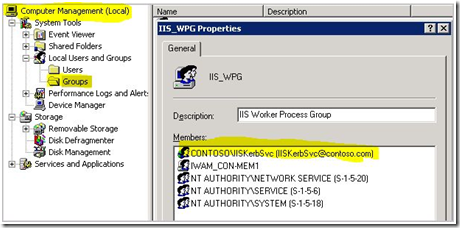
Figure 6 - Adding application pool account to the IIS_WPG group
Note
This step is done to allow the IISKerbSvc (application pool identity) the ability to impersonate the user on the web server. If you look at the computer’s user right assignments you will see Impersonate a client after authentication and the IIS_WPG group is added there by default.
We now need to configure the user account for delegation within the domain. So we need the Setspn tool in the Windows Support Tools, and access to Active Directory Users and Computers.
At a command prompt type the following to find out what Service Principal Names (SPNs) are already associated with your IIS application pool service account:
setspn -L <Domain Name>\<Account from Step 2>
What we want to see is similar to the following:
http/<IIS Web site Address>
http/<IIS Web site Address FQDN>Example:
http/webserver01
http/webserver01.contoso.comOr
http/www
http/www.contoso.comNote There is no colon (":") anywhere in here when we use HTTP. This is a common mistake that can happen when creating SPNs for web sites.
If you do not see any of the above listed for the application pool service account then we need to add them one at a time via the following command:
setspn -A http/<Web site Address > <Domain Name\<Account from Step 2>
setspn -A http/<Web site Address FQDN> <Domain Name\<Account from Step 2>Example:
setspn -A http/webserver01 Contoso\IISKerbSvc
setspn -A http/webserver01.contoso.com Contoso\IISKerbSvcOr
setspn –A http/www Contoso\IISKerbSvc
setspn –A http/www.contoso.com Contoso\IISKerbSvc
For more information on this topic as it relates to IIS you can review the below web site location:
Configuring Constrained Delegation for Kerberos (IIS 6.0)https://www.microsoft.com/technet/prodtechnol/WindowsServer2003/Library/IIS/df979570-81f6-4586-83c6-676bb005b13e.mspx?mfr=true
Configuring the SQL Backend
So that this blog is not too long (yeah, I know I am not known for short blogs) we are only going to show you how to configure the SQL server as the backend and how to test it since this is the most common situation where Kerberos delegation is configured. Keep in mind that for learning how Kerberos multi-hop works you do not need to install the full version of SQL. You can use SQL Express, and it can be installed on any operating system.
Registering a Service Principal Name
https://technet.microsoft.com/en-us/library/ms191153.aspx
Kerberos Authentication and SQL Server
https://technet.microsoft.com/en-us/library/cc280744.aspx
The SQL Server Service can run under basically two types of accounts.
- The Local System also known as the SYSTEM account.
- A domain user account configured as a service account that the customer creates.
The web site can verify either of these configurations, but there are different steps that need to be followed dependant on which configuration the SQL Server Service is running. Of course with all these configurations it is very important that we have the correct SPNs registered to the correct computer or user account.
User Account (Service Account) SPN Configuration
If the SQL Server Service is running as a user account, then we need to make sure that the MSSQLSvc SPN for the computer is not registered to the computer. You can run the following command to determine this:
setspn –L <SQL Server Computer Name>
If this does come back with a MSSQLSvc SPN registered then you will need to delete that SPN from the computer account, by typing the following command:
setspn –D MSSQLSvc/<Computer Name>:<Port> <Computer Name>
setspn –D MSSQLSvc/<Computer FQDN>:<Port> <Computer Name>Here is an example:
setspn –D MSSQLSvc/SQLSrv1:1433 SQLSrv1
setspn –D MSSQLSvc/SQLSrv1.contoso.com:1433 SQLSrv1Then you will want to verify that all SPNs are no longer registered by running SetSPN –L command again.
Once that has been verified, we will need to register the MSSQLSvc SPN to the SQL Server service account being used to run the SQL Server by typing the following:
setspn –A MSSQLSvc/<SQL Server Name>:<Port> <Domain Name>\<User Account>
setspn –A MSSQLSvc/<SQL Server Name FQDN>:<Port> <Domain Name>\<User Account>Here is an example:
setspn –A MSSQLSvc/SQLSrv1:1433 CONTOSO\MSSQLSvc
setspn –A MSSQLSvc/SQLSrv1.contoso.com:1433 CONTOSO\MSSQLSvc
Local System SPN Configuration
If the SQL Server service account is running as Local System (which is not common today), then we need to make sure that the MSSQLSvc SPN for the computer is registered. You can run the following command to determine this:
setspn –L <SQL Server Name>
If this does NOT come back with a MSSQLSvc SPN registered then you will need to add the SPN for the computer, by typing the following command:
setspn –A MSSQLSvc/<Computer Name>:<Port> <Computer Name>
setspn –A MSSQLSvc/<Computer FQDN>:<Port> <Computer Name>Here is an example:
setspn –A MSSQLSvc/SQLSrv1:1433 SQLSrv1
setspn –A MSSQLSvc/SQLSrv1.contoso.com:1433 SQLSrv1
Finishing the Configuration for Delegation to Work
Open Active Directory Users and Computers.
Find the user account that the IIS Web site is using for the web application pool and double-click it.
If you are in 2000 native mode for the domain, click on the Account tab and check the box Account is trusted for delegation.
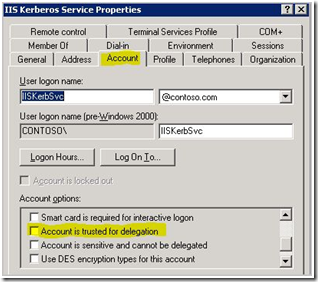
Figure 7 - Windows 2000 domain functional level delegation setupIf you are in 2003 domain functional mode, click on the Delegation tab.
NOTE This tab does not exist if you are not in Windows Server 2003 domain functional level or the user account does not have a SPN already defined on the account.
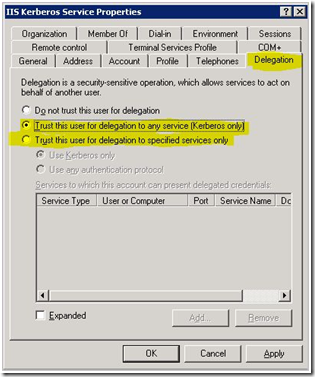
Figure 8 - Windows Server 2003 domain functional level delegation setupTo enable open delegation select: Trust this user for delegation to any service (Kerberos only) .
To enable constrained delegation by selecting: Trust this user for delegation to specified services only.
Click the Add button, and then click on the Users or Computers button.
If the SQL Service was configured to start as Local System then type in the SQL Servers computer name, and click Check Names. Click OK.
If the SQL Service was configured to start as a domain user account then type in the user account name, and then click Check Names. Click OK.
For this discussion remote computer name refers to the backend server that the IIS web site needs to hand the users Kerberos ticket to.
You will see all available SPNs on the remote system. Select the SPN associated with MSSQLSvc then click OK.
Click OK on the user properties dialog box.
Restart the IIS service.
How to Test the Web Site
Open Internet Explorer, and type in the address of the https://<web site name>/kerbdeleg
Example:
https://webserver01/kerbdeleg
https://webserver01.contoso.com/kerbdelegThen click on the Add Backend button. Then you will get the web page to configure the backend you want to talk to.
Remote address - this should be the SQL Server with which you want to test Kerberos delegation.
Example:
MEMBER1 or MEMBER1.contoso.com
Service type - this needs to be set to SQL Server.
Listening port - for SQL Server access this port needs to match where SQL Server is listening. By default this is port 1433.
Service account: If the SQL Server service was configured as Local System then this needs to be set to Preferred and Local System. If the SQL Server service was configured for a domain account then this needs to be set to Configured and type in the <domain>\<SQL service account> .
Click Submit.
Configuring for Protocol Transition
You will first need to make sure that constrained delegation is configured and working in your lab environment. Once this has been accomplished then you should be able to continue.
Bring up Active Directory Users and Computers.
- Find the user account that is being used for the IIS application pool and Edit the user.
- Click on the Delegation tab, which you can review in Figure 8.
- And select Use any authentication protocol.
- Click OK.
Restart the IIS service.
Common Problems When Configuring the Site
Prompted for user credentials over and over again – check to make sure that the application pool is correctly configured on the virtual directory. Review Step 5 from above.
Directory Listing Denied error – Check to make sure Execute permissions is to Scripts only under Virtual Directory tab. Review Step 5 from above.
403 error – check to make sure default.aspx has been added as a default content page. Review Step 5 from above.
404 error – check to make sure that you have installed support for ASP.NET. Look in Add/Remove Windows Components under Application Server and verify that ASP.NET is checked.
- Next in IIS Manager select Web Service Extensions and make sure that ASP.NET is allowed.
- Right-click the Virtual Directory and select Properties.
- Click on the ASP.NET tab, and select an ASP.NET version that is installed.
I hope that you have been able to learn some new things. All the steps outlined here need to be done when configuring Kerberos delegation and this site will definitely help engineers to understand how Kerberos delegation works.
Have fun learning and testing all the different configurations that are possible with this application!
- Rob Greene
Comments
Anonymous
January 23, 2009
Hi Craig, I have a question and it feels like i already know what the answer is, but would just like to get the confirmation from the experts. We have 2 Forests with a full 2 way transitive trust. The catch is that we have a 2000 DC in on the parent domain which meens that we need to keep the functional levels at 2000 Native. My question is : Is it possible to have kerberos working and credentials successfully delegated when I log in from the foreign domain on the parent domain where the WebApplication's AppPool is running as a user from the parent domain. This WebAppication connects to a 3rd party application where the user is being impersonated. Everything works fine from the parent domain when a user connects to the site, but as soon as a user is connecting from the foreign domain the credentials are not successfully delegated. Your help will be greatly appreciated. GertAnonymous
January 26, 2009
Hi All Rob here again. I thought I would take the time today and expand upon the Kerberos DelegationAnonymous
January 28, 2009
Hey Gert, So the answer is no. In order for you to leverage Kerberos delegation accross a Forest a Forest Trust MUST be created between the two forests. In order for you to create a forest trust both forests MUST be at Windows Server 2003 Forest Functional Level. So you woul need to upgrade / demote all of you Windows 2000 domain controllers before you attempt to change the forest functional level. Once that is done, you can disolve the current External Trust(s) and create a new forest trust and then you will be able to support Kerberos authentication accross the forest. Just as an FYI, I do plan on writing a blog about supported configurations with kerberos authentication accross different trust configurations. I hope this helps. FYI, this is typically a great opportunity for AD Admins to get those last 2000 domain controllers upgraded to 2003/2008 because of the need for the application functionality.Anonymous
March 06, 2009
Is it possible to have multiple IIS 6.0 pools with different custom identities and use Kerberos Authentication? If this requires setting up multiple web sites on the same web server, is there a way to register SPNs for each of these sites? Thanks!Anonymous
March 06, 2009
The comment has been removedAnonymous
April 30, 2009
The comment has been removedAnonymous
June 11, 2009
The comment has been removedAnonymous
June 12, 2009
Hey Milenko, Well, I would really have to say maybe. I say maybe because I am not that familar with .NET coding and what real DLL is being used to make a connection to web service when all the .net code is being invoked ( it could be WinInet or WinHTTP being used at the client side). I would say try it, and see if that does resolve the issue. I will tell you about something else that I have ran into with .net is that you may actually have to pass the server name with port number when you do your authentication call because when .NET passes the authentication call down to the OS it does not tack on the port number to the Kerberos Authentication request. Sorry I could not be of more help in this situation... But if neither of these resolve your issue, please feel free to open up a case with our Developer Support group. Rob GreeneAnonymous
January 15, 2010
The comment has been removedAnonymous
January 15, 2010
Hi Sadia, So the first thing is if you are using IIS7 I would recommend that you use this blog to play with the delegation website on IIS7. http://blogs.technet.com/askds/archive/2009/01/26/addendum-making-the-delegconfig-website-work-on-iis-7.aspx I have a feeling that the first set of problems / hurtles you are going to need to figure out is if Kernel mode authentication is causing your issue or not. Keep in mind that you might have to modify the web.config or applicationhost.config file for the application and add useAppPoolCredentials=”ture” setting under Windows Authentication if you want to use Kernel mode authentication. I see that you did not reference what type of Kerberos delegation you are using? Constrained or unconstrained. The best pointer I can give you when setting up delegation get it working with unconstrained delegation first. Since this is the easiest to troubleshoot. Once you know that the application works with unconstrained you can try to get it working with constrained delegation. To be honest with you, your delegation scenario is too complicated to attempt to help you via the comments section on this blog. I would strongly recommend that you create a case with us here at Microsoft to help get this resolved for you.Anonymous
January 17, 2010
The comment has been removedAnonymous
January 18, 2010
I am not sure what a premium subscription you are talking about. Are you saying Premier support contract? If you do not have a Premier support contract then you can use this website to get your local access number to open a case: http://support.microsoft.com/common/international.aspx?RDPATH=dm;en-us;select&target=assistance