Using ConfigMgr Co-Management to offload Windows Updates to Intune
This post walks through moving Windows Update workloads to Intune. Co-Management for Windows 10 devices introduced in ConfigMgr 1710 release which enables you to move various workloads from traditional on-premise management to newer modern management capabilities hosted in cloud like Intune.
One of the most sought-after requirement by enterprises is patch compliance and keep devices secure no matter where they are. For machines outside the corporate network, this typically requires hosting SUP in DMZ with IBCM or implementing CMG. However, in this case we will use Intune to deploy Windows 10 Quality and Feature updates.
Requirements –
Hybrid Azure AD joined (joined to AD and Azure AD)
Intune Subscription
Windows 10 version 1709
Co-Management Setup –
From a ConfigMgr 1710 console click Administration > Cloud Services > Co-management to launch the wizard. Sign In with your Intune account.
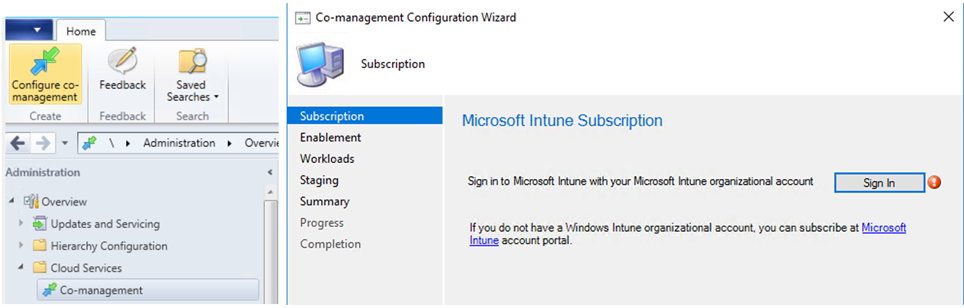
Note – If its failing to connect, check the account has license for Intune/EMS.
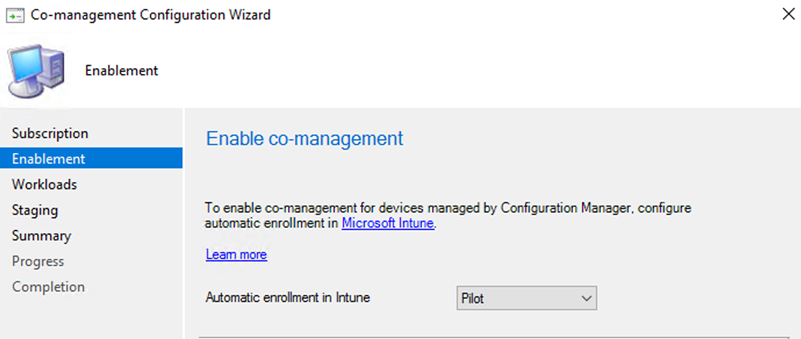
Now as we are ready to setup co-management, you want to decide if you'd like to Pilot the setting or apply for all clients. I am going with Pilot for testing.
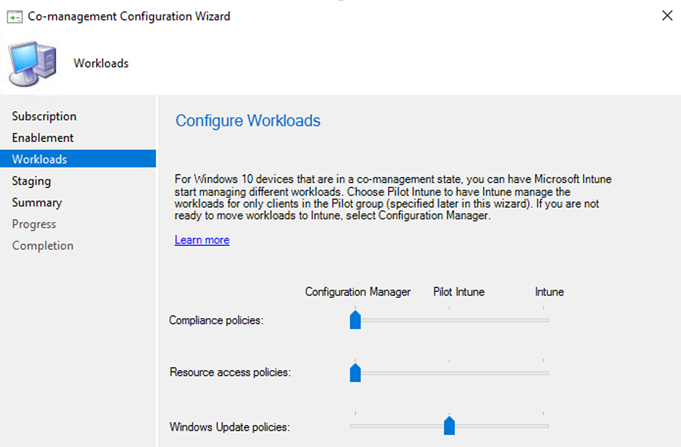
Now its time to move the workloads. In this case, we are moving the Windows Update policies to Intune.
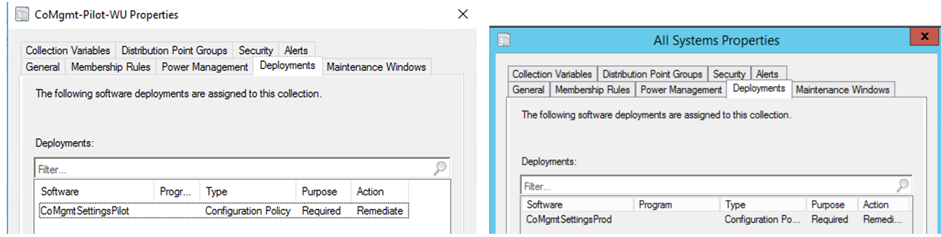
Choose a collection for the pilot group of computers.

Click Next to finish the wizard.
You will notice a configuration policy deployment is created and targeted against the collection you chose. A corresponding Production policy is also created and targeted against All System collection.
Intune Software Updates Configuration –
Next, we need to configure Software Updates policies in Intune.
From the Intune console, click on Software Updates > Windows 10 Updates Rings.
Create policy as desired settings and Assign to a Group of devices. (sample screenshots). For guidance on these settings refer this link - /en-us/intune/windows-update-for-business-configure 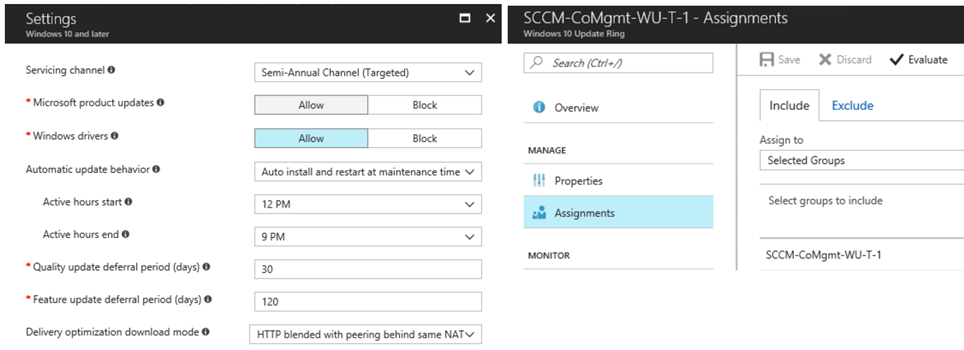
The client will receive new MDM policies for deployment. MDM Registry settings are stored in - HKLM\Software\Microsoft\PolicyManager\current\device\Update 
If you notice above screenshot has a policy named "Do not connect to any Windows Update Internet locations" This is in fact the Dual Scan Policy Enabled by ConfigMgr which blocks the client's ability to scan against Internet (Microsoft Update)
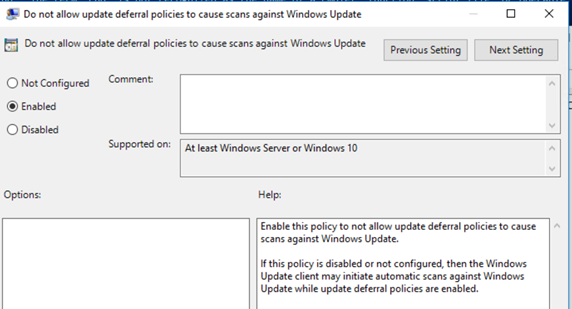
ConfigMgr Windows Update for Business Policy –
From the ConfigMgr console, create a Windows Update for Business Policy (matching the Intune policy) and target against the same collection of machines. This will disable the dual scan deferral policy.
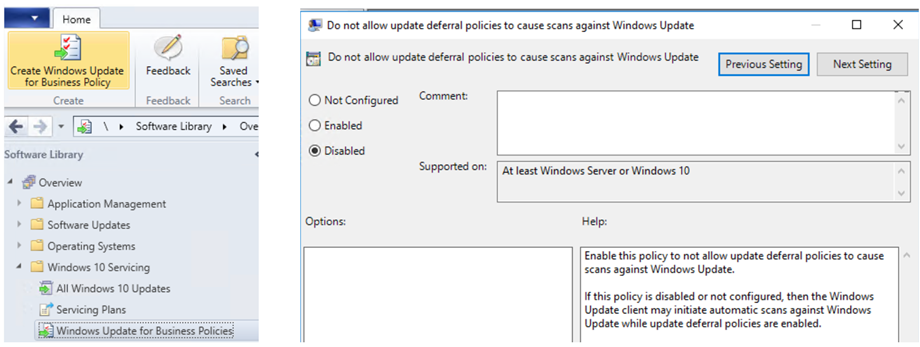
Now the client is ready to receive updates as per Intune defined settings for Software Updates.
I have a 30-day deferral for Quality Updates, below is a screenshot of device after only applying the October updates. Checking for new updates don't offer November updates.

Reporting –
The ConfigMgr compliance reports will stop reporting the compliance for Quality & Feature Updates. You will have to rely on Intune dashboard > Software Updates Overview which isn't very detailed and I highly recommend implementing Windows Analytics Updates Compliance feature in OMS.
Managing Office 365 Updates –
You can continue using ConfigMgr to deploy Office 365 updates and report its compliance
Troubleshooting –
Verify Azure AD Hybrid Join Status – Use the command dsregcmd /status If the machine isn't Hybrid Azure AD joined, implementing Co-Management features will not help. You will see the device listed in Azure AD > All Devices 
Verify Intune Management – You should see the device listed in Intune > All Devices. If you don't see your device, make sure its member of CoMgmt collection and Intune device group which has targeted Software Updates Policies.
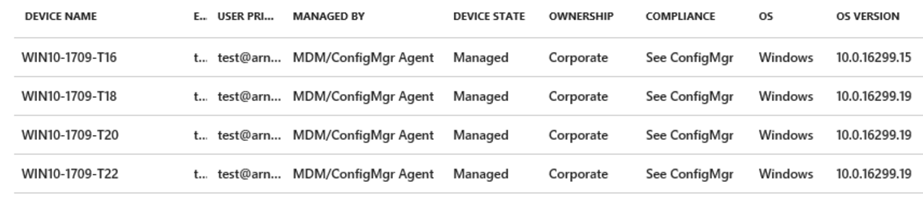
For troubleshooting you can refer CoManagementHandler.log on client PC.
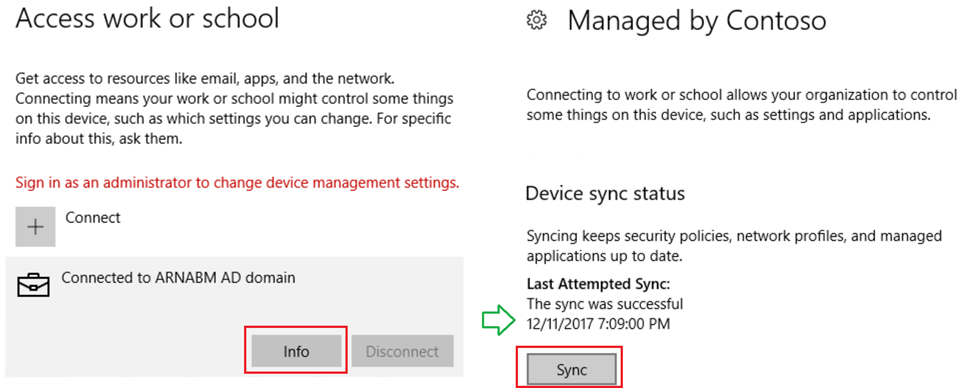
Sync device to receive Intune MDM Policies. If you don't see Info button, its an indication machine isn't registered in Intune yet.
Thanks
Arnab Mitra