Step-By-Step: Cloud Management Gateway on ARM
Introduction
Starting ConfigMgr 1802 Cloud Management Gateway is NO longer a Pre-release feature and introduced the option of Azure Resource Manager [ARM] deployment.
This removes the requirement of the traditional Azure Management Certificate and relies on Azure AD auth. to create the modern resources.
Note – The CMG deployment with ARM continues to use the classic cloud service, which the Cloud Service Provider [CSP] doesn't support.
This blog post intents to give you a step by step instructions of implementing CMG on ARM.
Environment
Here's a snapshot of the lab environment I used to implement this feature.
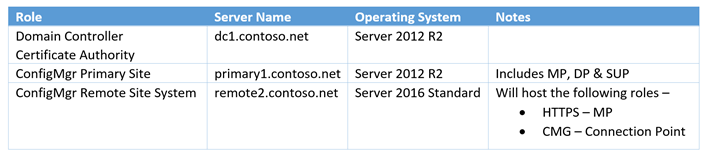
Note - Starting 1802 you can no longer host an HTTP MP to listen to CMG traffic. The change is introduced to provide better support for Azure AD token-based auth.
1 Certificates
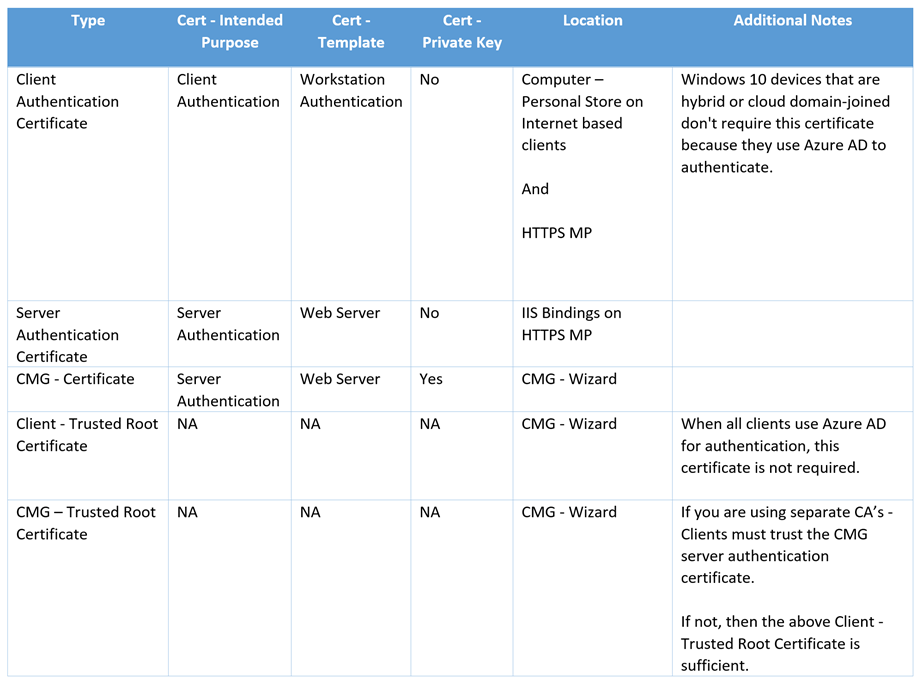
The following certificates are required -
- Client Authentication Certificate – For Clients and MP
- Server Authentication Certificate – For HTTPS - MP
- Cloud Management Gateway Certificate – For CMG
- Trusted Root Certificate – For CMG
Here's a table for additional clarification –
1.1 Instructions
Refer this table for instructions to generate the required certificates.
Type |
Instructions to create |
| Client Authentication Certificate | https://technet.microsoft.com/en-us/library/gg682023.aspx#Deploying%20the%20Client%20Certificate%20for%20Windows%20Computers |
| Client – Trusted Root Certificate | On a client PC, follow the instructions –
|
| CMG – Trusted Root Certificate | The above certificate will work if you are using the same CA, else get the Trusted Root CA cert from the Certificate authority. Not needed for public CA's |
| Server Authentication Certificate | https://technet.microsoft.com/en-us/library/gg682023.aspx#Deploying%20the%20Web%20Server%20Certificate%20for%20Site%20Systems%20that%20Run%20IIS |
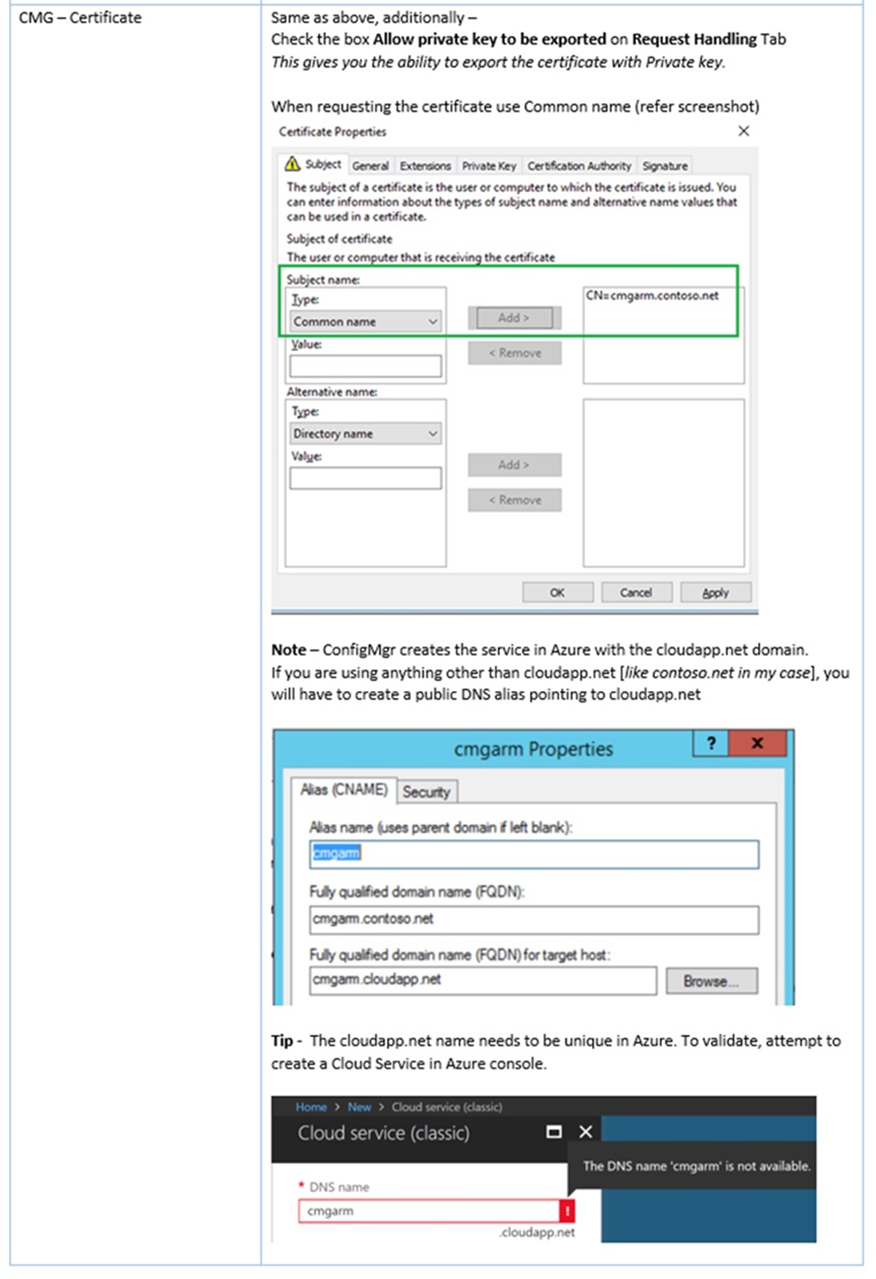
I have generated the following certificates from my CA (Trusted Root cert was copied from client cert) -
| Type | Name | Notes |
| CMG Certificate | cmgarm.contoso.net | For Cloud Management Gateway |
| Server Authentication Certificate | remote2.contoso.net | For HTTPS Management Point |
| Client Authentication Certificate | win102.contoso.net | For the test client running Windows 10 |
2 HTTPS Configuration
We need to configure the Primary Site & Management Point for certificate authentication.
2.1 Primary Site -
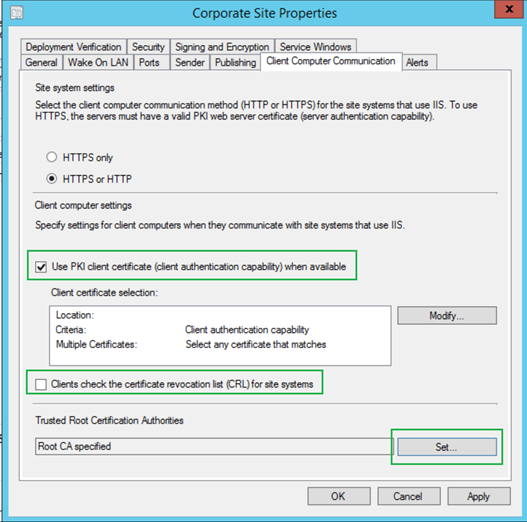
- Go to Administration > Site Configuration > Sites
- Properties of Primary site > Client Computer Communication Tab
- Check the box – Use PKI client certificate (client authentication capability) when available.
- Clear the box – Clients check the certificate revocation list (CRL) for site systems. [Clear this only if you haven't published the CRL on internet. ]
- Under Trusted Root Certification Authorities click Set to specify the Client Root Certificate from section 1.1
- Click OK to commit the changes.
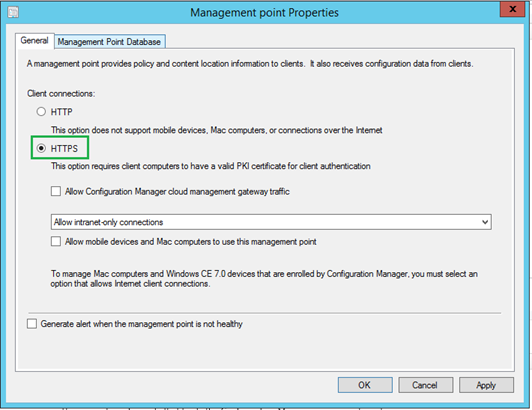
2.2 Management Point –
Before proceeding, make sure that you have already associated the Server Auth. Certificate (remote2.contoso.net in my case) in the IIS website Bindings as per instructions (Configuring IIS to Use the Web Server Certificate) in step 1.1
Next Steps -
Go to Administration > Site Configuration > Servers and Site System Roles
Select the Site Server holding the MP role which you plan to change to HTTPS. [Remote2.contoso.net in my case]
Under Site System Roles, select Management point and go to it properties
Change the Client connections to HTTPS and click OK
Monitor the mpsetup.log for a successful install and mpcontrol.log to validate the health
3 Configure – Azure Services
For the new CMG-ARM model, we first need to configure Azure Services by creating a Web and Client applications which will be leveraged by CMG to create Azure resources.
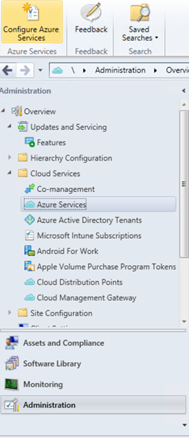
- On the ConfigMgr Console, go to Administration > Cloud Services > Azure Services.
- Click Configure Azure Services on the ribbon menu.
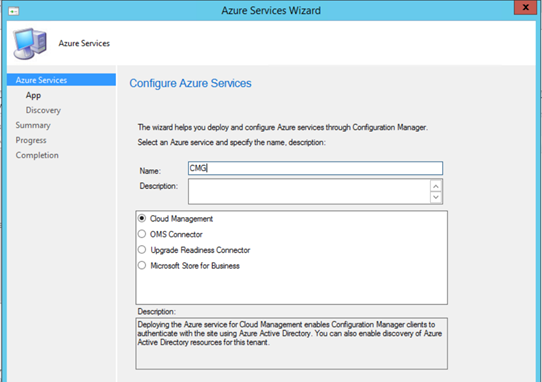
- Select Cloud Management in the Wizard.
- Provide a Name and click Next to proceed.
- Click on Browse to either Import an existing App or click Create to start with a fresh App.
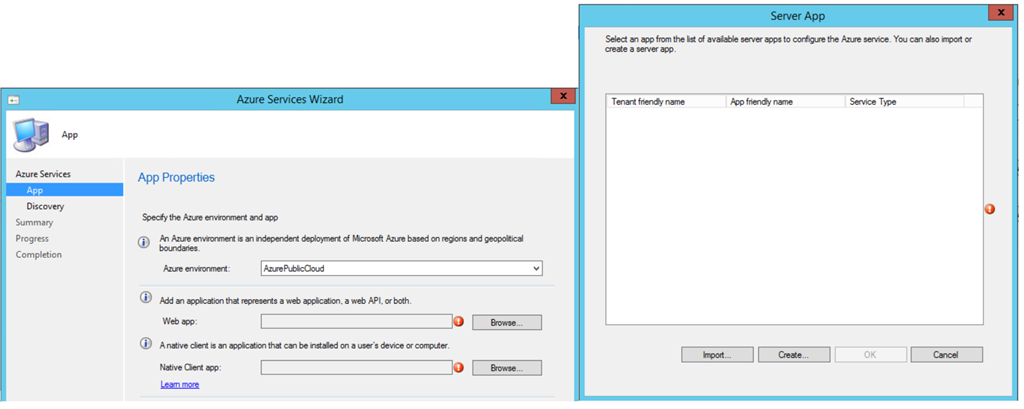
- You need to Sign in with a Subscription Admin.
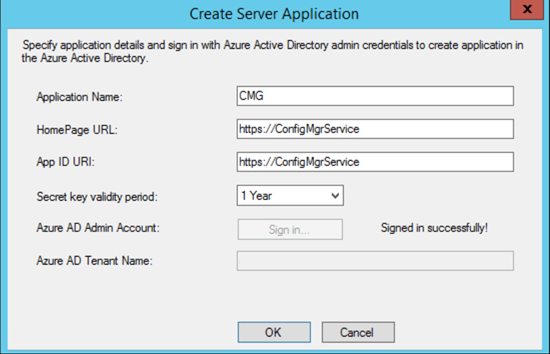
Follow the steps for both Web and Client App to proceed with the wizard.
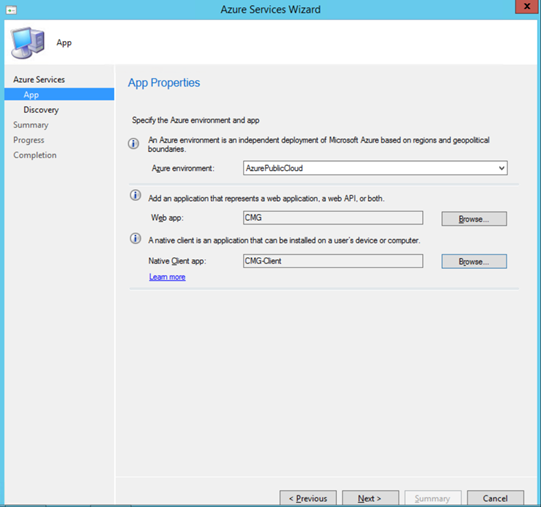
Click Next, Enable Azure AD User discovery is not required for CMG and is optional if you'd like to check it and finish the wizard.
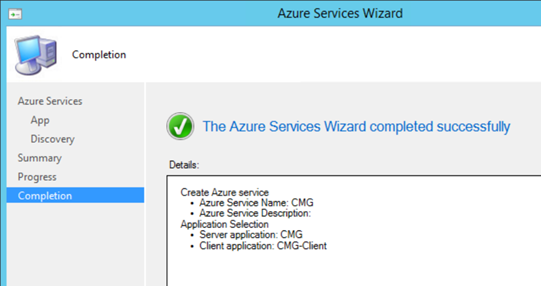
4 Setup CMG
Now we are all set to configure CMG.
- On the ConfigMgr Console, go to Administration > Cloud Services > Cloud Management Gateway
- Click Create Cloud Management Gateway on the ribbon menu.
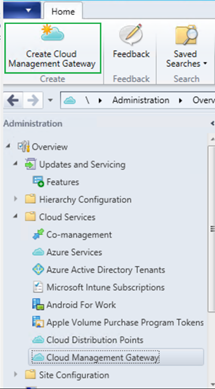
- Choose Azure Resource Manager deployment
- Sign In with Azure Subscription Admin account
- The subscription info and the Web App created in Section 3 will auto populate. Click Next to proceed.
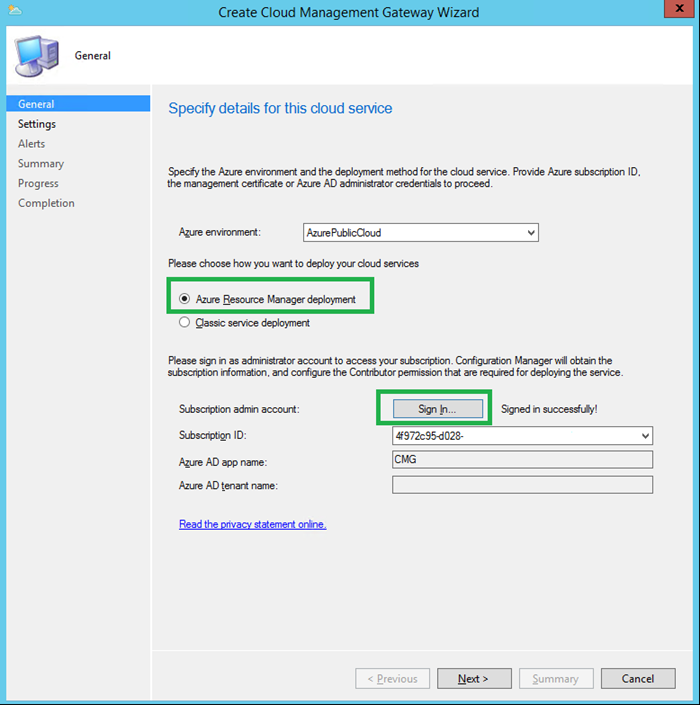
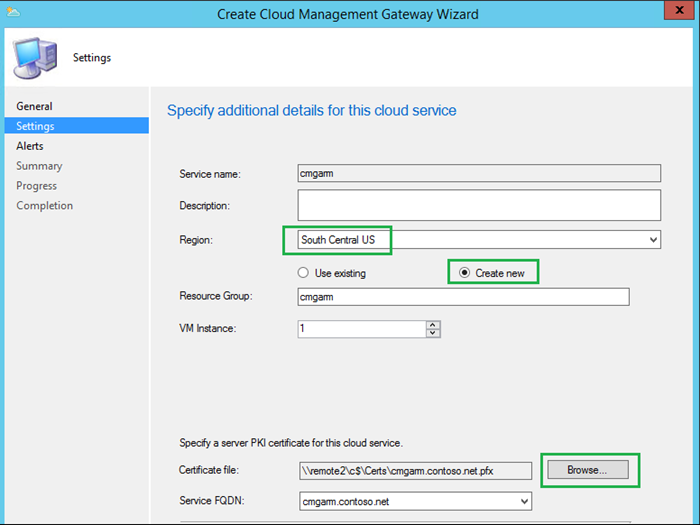
Click Browse to specify the CMG Certificate generated by following instructions from Step 1.1 in my lab I used cmgarm.contoso.net
This will auto populate the Service name.
Choose your Azure Region
Choose Create new under Resource Group.
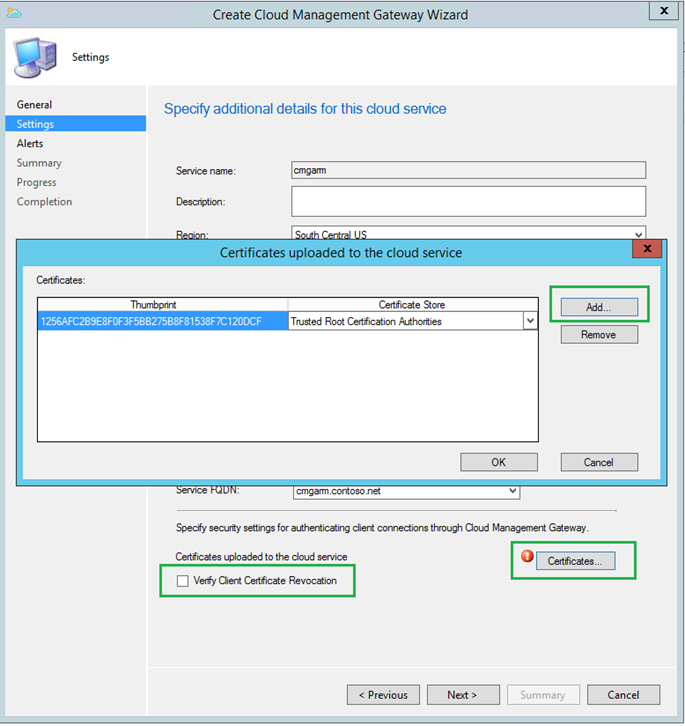
- Add the Client Trusted Root Certificate from section 1.1
- Verify Client Certificate Revocation checkbox [Clear this only if you haven't published the CRL on internet. ]
- Click Next to finish the Wizard.
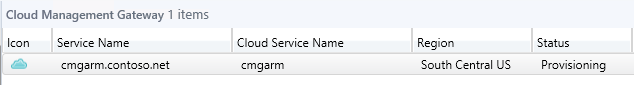
The deployment in azure begins -
CloudMgr.log will show the details of the CMG deployment. Sample snippet below –
Resource Manager - Creating resource group cmgarm with location South Central US SMS_CLOUD_SERVICES_MANAGER 3/27/2018 6:02:27 PM 3140 (0x0C44)
Resource Manager - Resource group cmgarm created SMS_CLOUD_SERVICES_MANAGER 3/27/2018 6:02:28 PM 3140 (0x0C44)
Resource Manager - Creating cloud service cmgarm with deployment CreateCloudServiceba0f51cf-SMS_CLOUD_SERVICES_MANAGER 3/27/2018 6:02:28 PM 3140 (0x0C44)
Resource Manager - Creating storage service cmgarm with deployment CreateStorageService7cabb6ec-SMS_CLOUD_SERVICES_MANAGER 3/27/2018 6:02:45 PM 3140 (0x0C44)
Uploading file C:\Program Files\Microsoft Configuration Manager\inboxes\cloudmgr.box\CloudProxyService.cspkg to container deploymentcontainer with blob name cmgarm.cspkg in storage account cmgarm SMS_CLOUD_SERVICES_MANAGER 3/27/2018 6:08:44 PM 3140 (0x0C44)
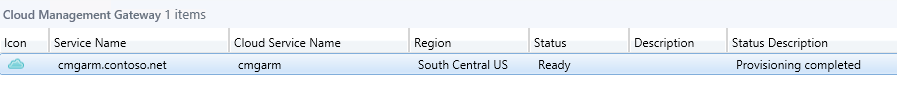
Log in to the Azure Console to view the resources
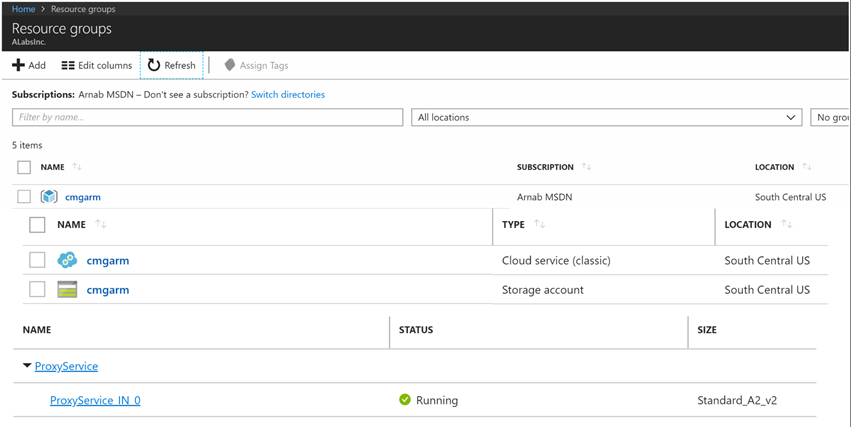
Validate the status Ready from ConfigMgr console.
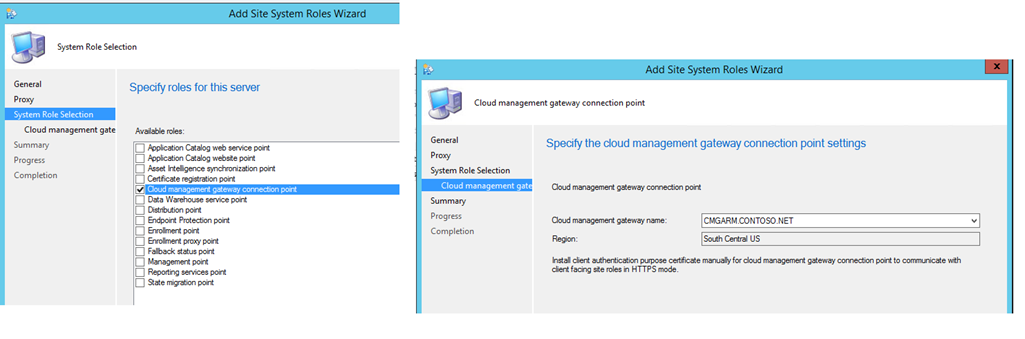
4.1 CMG – Connection Point
This is the on-premise site system role dedicated for communication with CMG in Azure.
- Add new site system role and choose Cloud Management Gateway connection point
- Validate the Gateway name we just created and the Region to finish the wizard.
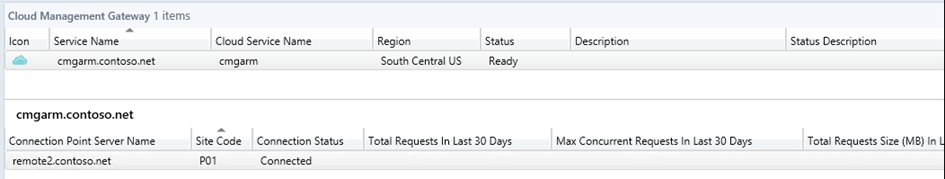
The Connection Point server will show as associated in the console. For troubleshooting this component, you can check SMS_Cloud_ProxyConnector.log.
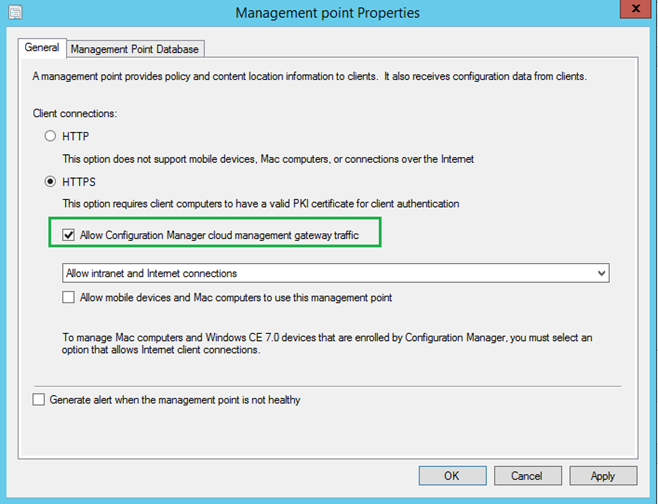
4.2 Allow Gateway Traffic
We need to configure the Management Points and Software Update Points to listen to CMG traffic from Internet clients.
- On the Management Point Properties, check the box Allow Configuration Manager cloud management gateway traffic
- Follow the same steps for Software Update Point.
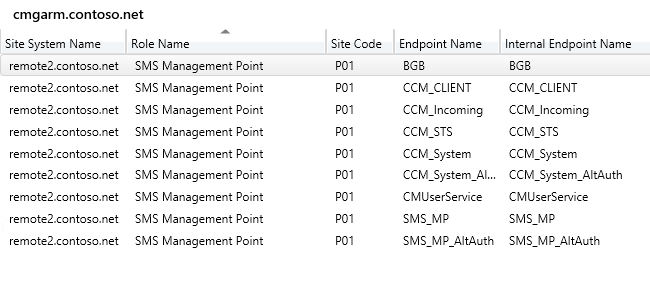
Once associated, the server endpoints will be listed under CMG – Connection Point
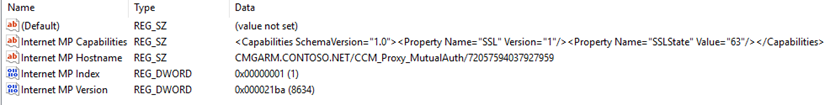
5 Client Validation
The client machines will receive CMG connection info which can be verified by the following registry key – HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SMS\Client\Internet Facing
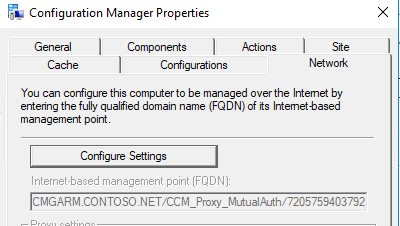
On a test client outside corporate network, check CCMMessaging.log to validate a successful communication with CMG
Raising event:
instance of CCM_CcmHttp_Status
{
ClientID = "GUID:12EF623B-2210-4C6B-A718-5CB7EB768BF7";
DateTime = "20180328050333.897000+000";
HostName = "CMGARM.CONTOSO.NET";
HRESULT = "0x00000000";
ProcessID = 2100;
StatusCode = 0;
ThreadID = 5228;
};
CcmMessaging 3/27/2018 10:03:33 PM 5228 (0x146C)
Initiate a Machine Policy Cycle and verify a successful download from PolicyAgent.log
Initializing download of policy 'CCM_Policy_Policy5.PolicyID="{bbeea4ad-d0bf-4d64-b0a3-fabe72e99c56}",PolicySource="SMS:P01",PolicyVersion="33.00"' from 'https://CMGARM.CONTOSO.NET/CCM_Proxy_MutualAuth/72057594037927959/SMS_MP/.sms_pol?{bbeea4ad-d0bf-4d64-b0a3-fabe72e99c56}.33_00' PolicyAgent_ReplyAssignments 3/27/2018 10:05:04 PM 7588 (0x1DA4)
Thanks,
Arnab Mitra
Comments
- Anonymous
May 03, 2018
Can we enable anti-malware feature of cloud services using cloud management gateway / cloud distribution point?- Anonymous
May 21, 2018
Are you referring to Co-Management here? Then its definitely possible starting 1802 of ConfigMgr we introduced EndPoint protection workloads to be moved to Intune.
- Anonymous
- Anonymous
May 20, 2018
(The content was deleted per user request)- Anonymous
May 21, 2018
The comment has been removed- Anonymous
May 21, 2018
(The content was deleted per user request)- Anonymous
May 21, 2018
(The content was deleted per user request)- Anonymous
May 21, 2018
(The content was deleted per user request)- Anonymous
May 21, 2018
The comment has been removed
- Anonymous
- Anonymous
- Anonymous
- Anonymous
- Anonymous