Public Edge Server Certificates Show As Invalid
Ran into an interesting issue while at a customer site, their Lync Edge servers started reporting LS Protocol Stack Warnings 14397 and LS Protocol Stack Errors 14361 as shown below:
Proceeded to validate that the certificates were present in the correct store as well as that there were still valid certificates with their respective chain.
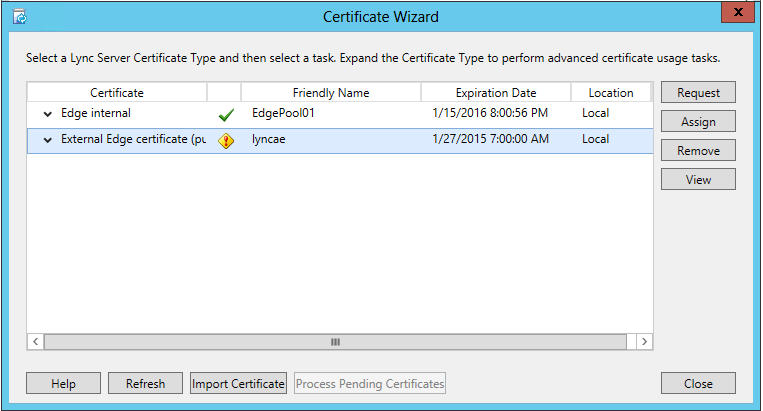
In running the Lync Deployment Wizard and proceeding to Step 3: Request, Install or Assign Certificates - the certificate status for the External appeared to be having issues or invalid.
In attempting to assign the certificate via the wizard notice that the Certificate Store does not recognize the external certificate.
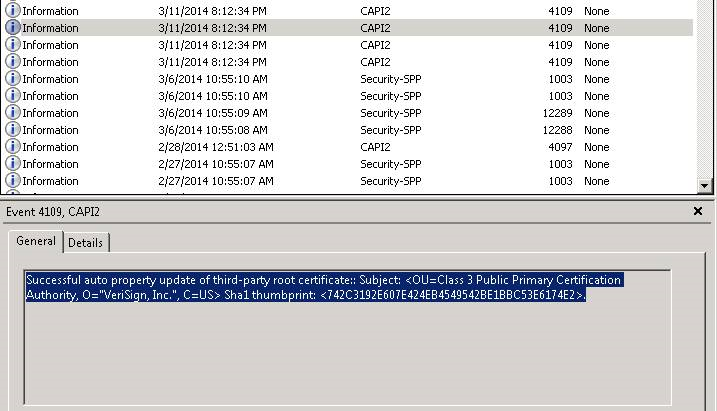
Proceeding to the Event Viewer the Application Logs contain the Informational Message with the Event ID 4109 from CAPI2 as the Source. In looking at the details of the entry it was evident that there was a change in a few of the of the root certificates. In this particular case, the concentration was on the Verisign Certificate that was updated as this was the issuer of the certificate. Using the thumbprint in the details of the Information entry we located the certificate in the Trusted Root Certificate store.
Using the name of the certificates in the log, I looked at the root chain and I noticed that this particular the Intended Purpose for the Root Certificate had Code Signing selected only.
Select the Root Certificate from the Trusted Root Certificate, Go to the Details tab to verify the Thumbprint with the value in the Informational entry in the Event Viewer. Once verified, click the Edit Properties button. Add the Certificate purposes required Server Authentication and Client Authentication, Hit Apply then OK.
After making the necessary changes to the Root Certificate to support Server Authentication and Client Authentication the Deployment Wizard recognizes the certificate and allows for assignment. The Edge Servers no longer report the errors in the Lync Server logs -- Edge Services are working properly.
A special Thanks to Bryon Castillo for providing the screen captures.