Creating an Active Directory Trust With APS
It is my assumption that almost all companies with an APS will want to connect it to their Active Directory so that they can use integrated authentication. What I will detail in this article is hopefully everything you need to know or consider when creating this trust. I highly recommend involving your Active Directory, DNS, and Network Administrators in this process from the beginning.
Recommended Ports
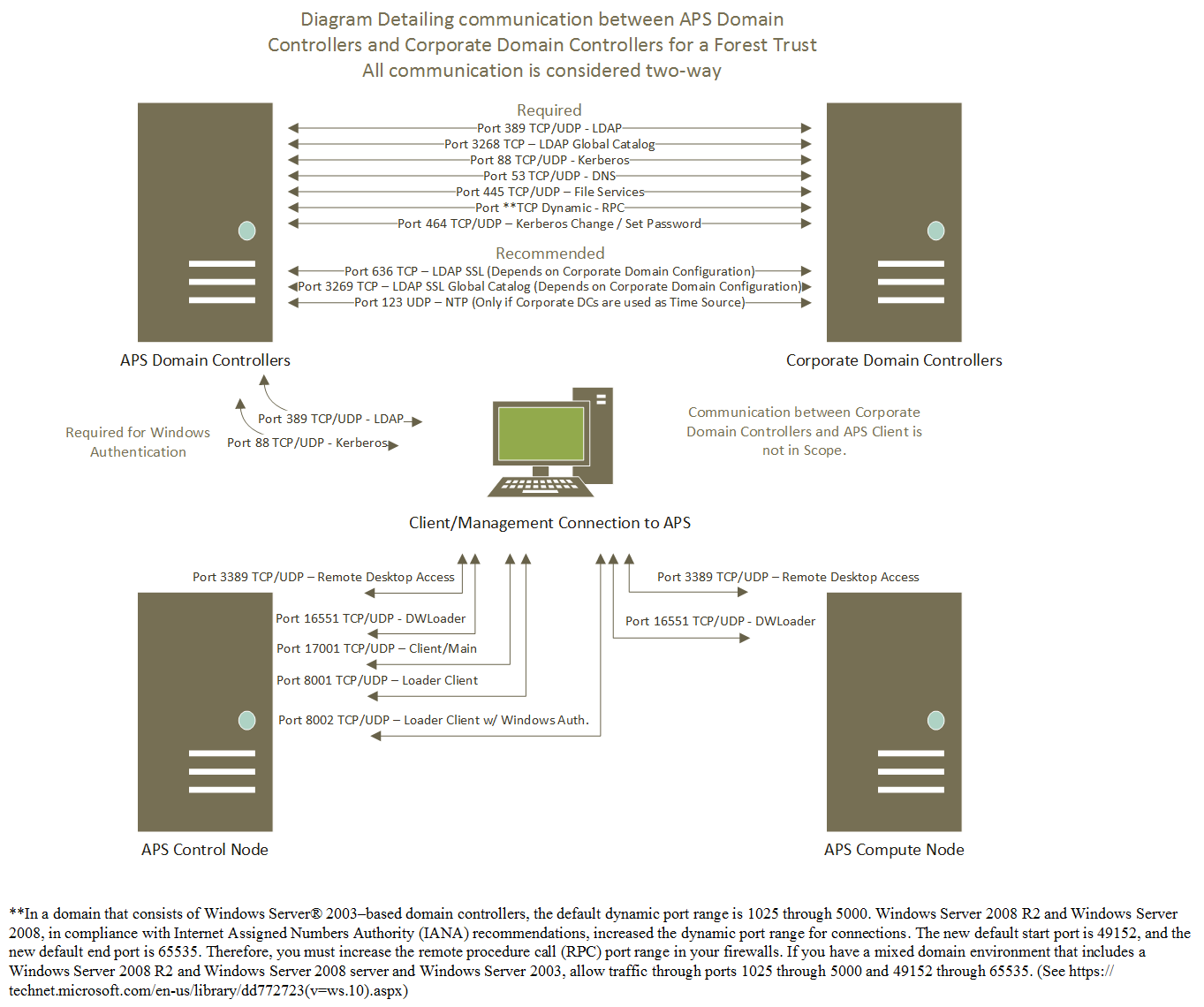
First things first, let’s talk port requirements. Luckily Microsoft has a good article that explains the ports required here -> https://technet.microsoft.com/en-us/library/dd772723(v=ws.10).aspx – which contains the following table and dynamic port information.
Protocol and Port |
AD and AD DS Usage |
Type of traffic |
| TCP and UDP 389 | Directory, Replication, User and Computer Authentication, Group Policy, Trusts | LDAP |
| TCP 636 | Directory, Replication, User and Computer Authentication, Group Policy, Trusts | LDAP SSL |
| TCP 3268 | Directory, Replication, User and Computer Authentication, Group Policy, Trusts | LDAP GC |
| TCP 3269 | Directory, Replication, User and Computer Authentication, Group Policy, Trusts | LDAP GC SSL |
| TCP and UDP 88 | User and Computer Authentication, Forest Level Trusts | Kerberos |
| TCP and UDP 53 | User and Computer Authentication, Name Resolution, Trusts | DNS |
| TCP and UDP 445 | Replication, User and Computer Authentication, Group Policy, Trusts | SMB,CIFS,SMB2, DFSN, LSARPC, NbtSS, NetLogonR, SamR, SrvSvc |
| TCP 25 | Replication | SMTP |
| TCP 135 | Replication | RPC, EPM |
| **TCP Dynamic | Replication, User and Computer Authentication, Group Policy, Trusts | RPC, DCOM, EPM, DRSUAPI, NetLogonR, SamR, FRS |
| TCP 5722 | File Replication | RPC, DFSR (SYSVOL) |
| UDP 123 | Windows Time, Trusts | Windows Time |
| TCP and UDP 464 | Replication, User and Computer Authentication, Trusts | Kerberos change/set password |
** In a domain that consists of Windows Server® 2003–based domain controllers, the default dynamic port range is 1025 through 5000. Windows Server 2008 R2 and Windows Server 2008, in compliance with Internet Assigned Numbers Authority (IANA) recommendations, increased the dynamic port range for connections. The new default start port is 49152, and the new default end port is 65535. Therefore, you must increase the remote procedure call (RPC) port range in your firewalls. If you have a mixed domain environment that includes a Windows Server 2008 R2 and Windows Server 2008 server and Windows Server 2003, allow traffic through ports 1025 through 5000 and 49152 through 65535.
Though you may not always require all of these ports, it is highly recommended that you open all of them for full functionality, all of them will be used at one point or another. The scope of this information is for the link between APS Domain controllers to and from your Corporate Domain Controllers.
Here is a simple diagram that shows the different communication and ports used.
Requirements of the Trust
The APS uses a .local subdomain. If your APS is named FABDOM, its Active Directory will be FABDOM.local. This brings up red flags for some administrators, please make sure your DNS and Domain Admins know that this is required as part of the trust. At the time of writing this article, current version of the APS is V2 AU4. The most recent versions are AU3 and AU4 and this document focuses on them. All of this information is in the APS Documentation contained in the APS.AU4.chm file that you can download from https://www.microsoft.com/en-us/download/details.aspx?id=48241 .
Time is Important
While your team is submitting request in to open ports for the domain trust, it is a good idea to look at time on the appliance. It is often the case that the appliance has a time zone set for a specific reason and this can be set to what ever you need it to be set. The clock on the other hand, must be set to the true time and match what the time is on your corporate domain controllers. Let's say you are trying to create a trust with your corporate domain controllers and the time on them is 3:00 PM Central Standard Time. If you have the appliance set to Pacific Standard Time, then the clock will need to read 1:00 PM. Adjusting the time in APS can be a complex process.
Setting up DNS Forwarders Inside the Appliance
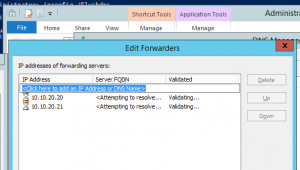
You need to get inside the appliance to do this; the best thing to do is get into your HST01 node which will be hosting the AD01 virtual machine. Using the Hyper-V Manager, connect to AD01, login as the APS domain admin and open the DNS Manager. In the properties of the AD01 DNS server, you will see a tab labeled Forwarders in which you want to add some or all of your corporate DNS servers that contains the DNS zone for your corporate Active Directory. From AD02 repeat adding the corporate DNS server to the forwarders list. This step allows the APS to find your corporate Active Directory. These steps are documented well in the APS Product documentation noted above. It is recommended that you remove any pre-existing forwarders after adding these corporate DNS servers to the list on both servers.
Lets assume your corporate DNS servers are: 10.10.20.20 and 10.10.20.21
Once you get to the forwarders Tab, you can make edits by clicking Edit. Remove all entries other than your corporate DNS servers. In the example above, the test numbers are not resolvable so they show a red X. In your environment you will want them to turn to green checks. Then click OK to accept your changes and then OK on the DNS server properties dialog to commit your changes.
Add the DNS Zone and Entries in your Corporate DNS for Trust and Authentication
For each appliance there are 13 entries/items that most people are concerned about for each APS in their environment. The following steps assume that you have a APS domain named FABDOM.local and a control node named PDWDOM-CTL01.FABDOM.local. These steps are performed on your corporate DNS servers, not on the APS DNS servers.
- Creating the APS domain zone. – FABDOM.local.
- A record for AD01 (FABDOM-AD01.FABDOM.local.)
- A record for AD02 (FABDOM-AD02.FABDOM.local.)
- A record for CTL01 (PDWDOM-CTL01.FABDOM.local.)
- Subdomain to hold LDAP and Kerberos service records – dc._msdcs.FABDOM.local.
- Subdomain to hold LDAP PDC service record – pdc._msdcs.FABDOM.local.
- LDAP SRV entry for AD01 in dc._ msdcs.FABDOM.local.
- LDAP SRV entry for AD02 in dc._ msdcs.FABDOM.local.
- Kerberos SRV entry for AD01 in dc._ msdcs.FABDOM.local.
- Kerberos SRV entry for AD02 in dc._ msdcs.FABDOM.local.
- LDAP SRV entry for AD01 in pdc._msdcs.FABDOM.local.
- POINTER (Reverse Lookup Zone entry) record for the IP of CTL01 pointing to the FQDN in step 4
- CNAME/Alias record for the friendly name of the APS in their corporate/work DNS zone that points to the FQDN in step 4
Creating the Trust Between your Corporate Active Directory and the APS Active Directory
Before you do this step, make sure that you have completed the sections noted above as “Setting up DNS Forwarders Inside the Appliance” which as stated is an edit on the DNS servers inside the appliances that also serve as Active Directory servers and “Add the DNS Zone and Entries in your Corporate DNS for Trust and Authentication” that is an edit on the servers hosting DNS to your environment or those serving the clients that will be connecting to the APS.
In the APS product documentation, there are full instructions on creating the One-Way Incoming trust from the APS Active Directory to your corporate Active Directory. This documentation gives our recommended practice to create the trust from your corporate Active Directory Domains and Trust management console.
Important setting about the trust are the following:
- The trust can be a Forest or Domain trust
- Collaborate with your corporate Active Directory Administrator to understand the users that will be connecting to the APS to make the decision to make the trust transitive or non-transitive. If your corporate domain is a single domain forest, a transitive trust will work just fine.
- A transitive trust means recursive or that all child domains will also be trusted.
- A non-transitive trust will only trust the domain that the trust is created with. It will not trust child domains.
- If there are other domains in the environment that will have users that connect to the APS and you only want to create non-transitive trust, there is no problem creating an additional trust to support those users.
- The trust is One-Way. I do not know of any reason that you would create a Two-Way trust with the APS domain.
- Inside the appliance you will see an outgoing one-way trust from the APS to your domain.
- In your corporate domain you will see am incoming one-way trust from your domain to the APS.
- As our documentation states, Forest-wide authentication is recommended and works in most cases. If your Active Directory Administrators want to use Selective Authentication and know the additional steps required to configure these restrictions, it is supported.
Conclusion
That is it for now, look forward to another post soon going over client authentication across the trust.