Microsoft and the AS 7799/ISO 17799 Standards for Information Security Management
What is Information Security?
Information and the systems and processes supporting it are key organisational assets. Information Security is about ensuring the confidentiality, availability and integrity of that information and ensuring that privacy issues are addressed as required to support the achievement of the organisation’s objectives.
Why is Information Security important to me?
The Information Systems that have brought so many improvements and efficiencies have also brought us new risks. Dependence on information systems increases the impact of successful attacks or other security incidents. At the same time, the interconnection of public and private networks and the trend to distributed computing is makes it more challenging to secure systems from unauthorised access and attack. Effective protection requires a comprehensive system – incorporating appropriate management and procedures as well as a robust risk management regime.
What are the AS 7799 and ISO 17799 standards?
Australian Standard, AS/NZS 7799.2:2003, details a risk based Information Security Management System, which can be used by organisations of all sizes, in both the public and private sectors. International Standard, ISO/IEC 17799:2005, outlines the accepted best practice for security management and offers guidelines on how these security measures should be implemented. In combination, these Standards provide a framework for the management of information and computer system security within an organisation.
Recent revision of ISO 17799:2005
ISO 17799 was revised in June 2005 to address over 4,000 comments that had been received since the 2001 issue and present a more logical structure for implementation. The most significant changes were: the introduction of a new control objective for managing security incidents; the reorganisation of human resources security into before, during and on termination of employment and additional controls for handling relationships with third parties. A number of existing controls were consolidated and new controls added to address issues such as acceptable usage and on-line transactions. A revision of AS 7799 is expected in 2006 to reflect the revised structure.
This diagram illustrates the revisions to the ISO 17799:2005 control objectives
What is an Information Security Management System?
An Information Security Management System or ISMS is the key set of processes that are required to support effective information security throughout an organisation. Key components of the ISMS include; a high level Security Policy that states the organisation’s objectives for information security, a Risk Assessment of the critical information assets and a ‘Statement of Applicability’, which documents how compliance is achieved against the Standard’s controls. The implementation of the ISMS follows the concept of the Plan, Do, Check Act cycle, common in other management systems, such as ISO 9001 and ISO 14001.
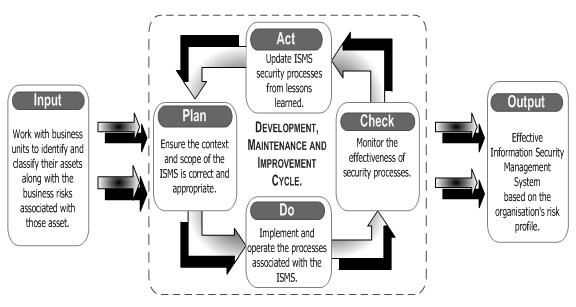
This diagram demonstrates the Plan, Do, Check, and Act lifecycle of an ISMS
How can AS 7799 and ISO 17799 help me?
These Standards define a framework and provide a suggested code of practice. They help ensure that individual security measures are integrated into a security architecture that focuses on securing key assets and the best allocation of the security budget. The Standards also promote a continual review and improvement process to assess effectiveness of implemented measures as well as addressing new risks faced by the organisation.
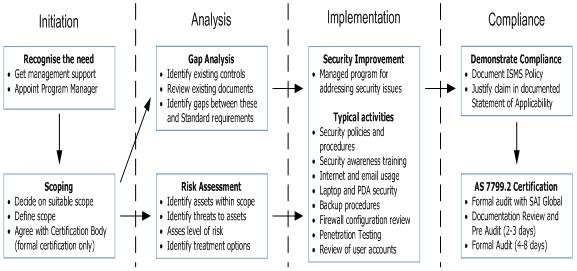
This diagram illustrates the process to achieve AS 7799 and ISO 17799 compliance.
Compliance and Certification?
Any organisation can use the guidance and requirements in the Standards to improve aspects of their internal security management. To achieve compliance, however, the organisation will need to implement measures to address all control objectives. Formal certification to AS 7799 can also be achieved though a formal audit by a certified independent auditor. This is the only way the organisation can demonstrate it has truly achieved compliance.
AS 7799 certification offers not only internal confidence in the organisations security management, but enables external demonstration through the use of the certification logo. This instils confidence in suppliers, customers and other business partners, as well as enhancing the organisation’s image and potentially offering a competitive advantage. Effective security is a key requirement for good governance and certification provides evidence of meeting due diligence requirements for information security aspects of some legislation.
AS 7799 is being actively promoted by some state governments and certification has been a mandatory requirement in contracts with particular security sensitivity.
What are the Control Objectives and their associated Controls?
A ‘control objective’ is a security issue that needs to be considered and addressed by the organisation as part of the ISMS. There are 11 main control objectives in ISO 17799 which are then broken down into 133 individual controls. The 11 Control Objectives are:
- Security Policy – Documented security objectives for the organisation, agreed by management
- Organisational of Information Security – Responsibilities and management forum for setting security objectives and management of external parties
- Asset Management – The management and usage of hardware and software assets and classification and handling of information
- Human Resources Security – The recruitment of staff, terms of employment, security awareness training and process for termination.
- Physical and Environmental Security – Securing the human and system environment, including entry controls, power and cabling security.
- Communications and Operations Management – Key security aspects of managing systems securely, such as backups, antivirus, media and laptop security
- Access Control – Effective password, privilege and user management on operating systems, applications and within networks.
- Information System Acquisition, Development and Maintenance – Secure development of software and maintenance of systems to maintain ongoing security
- Information Security Incident Management – The reporting, recording, management and review of security incidents.
- Business Continuity Management – Planning and defining the response in the event of a disaster.
- Compliance – Ensuring compliance with legal requirements, including IPR, computer misuse and privacy legislation
How can Microsoft help me address the individual controls?
Microsoft has long recognised the need for effective security in business and has developed products and expertise to help you address your security needs. Microsoft’s Trustworthy Computing initiative is one of the most fundamental and all-encompassing initiatives ever undertaken at Microsoft. Microsoft’s commitment includes considerable investments to increase the security of our products, as well as providing implementation guides and training based on industry best practices, such as ISO 17799 and AS 7799, for security.
AS 7799/ISO 17799 Control Objective |
Supporting Microsoft Products And Solutions |
|---|---|
Security Policy and Organisational Security Information security policy document (A.3.1.1/5.1.1)* Contact with special interest groups (A.4.1.5/6.1.7) Independent review of information security (A.4.1.7/6.1.8) |
Microsoft TechNet provides comprehensive guidance including whitepapers, guidelines and checklists to assist in developing and documenting an effective security policy. This includes ‘The Security Risk Management Guide’ that guides customers in the implementation of organisational security using a risk management approach core to the ISMS.. Microsoft Consulting Services and Microsoft Partners can provide Specialist Information Security Advice. The Microsoft Security Specialist Partner programme is designed to ensure Microsoft customers have access to a range of different security external experts. |
Asset Classification and Control · Inventory of assets (A.5.1.1/7.1.1) · Acceptable use of assets (A.12.1.2/7.1.3) |
Microsoft Solutions for Management (MSM) help organisations achieve operational excellence through delivering higher service quality, reliability, availability, security, and lower total cost of ownership for Windows® environments. MSM’s distinct set of technologies, best practices, and services helps organisations efficiently manage complex, enterprise IT environments. As the change and configuration management component of System Center 2005, System Management Server (SMS) 2003 provides enterprise application deployment, asset management, and security update capabilities for multiple systems, including desktops, devices and servers. Identifying and tracking hardware and software assets can also be simplified using automated tools such as System Management Server (SMS). |
Personnel Security · Management Responsibilities (8.2.1) · Information security education and training (A.6.2.1/8.2.2) |
A key requirement of AS7799 is that personnel are trained appropriately in the secure implementation and operation of systems. Microsoft’s range of training courses, certification programs, security-specific seminars and on-line educational ensures staff can achieve the appropriate level of qualification. Additionally, Microsoft Press have released numerous books on all aspects of security as well as specific technologies and solutions. |
Physical and Environmental Security · Protecting against external and environmental threats (9.1.4) · Supporting utilities (A.7.2.2/9.2.2) |
Ensuring that physical and environmental issues do not impact the availability of information is a key control issue with AS7799. Microsoft Operating Systems provide several technologies to assist in meeting the physical security requirements of AS7799. |
Communications and Operations Management · Change management (A.8.1.2/10.1.2) · Capacity management (A.8.2.1/10.3.1) · Controls against malicious code (A.8.3.1/10.4.1) · Information back-up (A.8.4.1/10.5.1) · Audit logging (A.9.7.1/10.10.1) · Monitoring system use (A.9.7.2/10.10.2) · Administrator and operator logs (A.8.4.2/10.10.4) · Fault logging (A.8.4.3/10.10.5) |
To assist in planning for effective operational support, Microsoft has published the Microsoft Operations Framework (MOF) that provides guidance on key operational procedures referred to in AS7799 – including change control, incident management and capacity planning. MOF also allows for the introduction of a risk management discipline for operations; something that is fundamental to AS 7799. Adoption of MOF provides organisations with guidance, knowledge and practical implementation details applicable to many of the Communications and Operations Management control objectives. Microsoft also provides tools such as the Windows AntiSpyware and Malicious Software Tools that protect PCs from spyware and other forms of malicious code. |
Access Control · Privilege management (A.9.2.2/11.2.2) · User password management (A.9.2.311.2.3) · Review of User Access Rights (A.9.2.4/11.2.4) · Password use (A.9.3.1/11.3.1) · User identification and authentication (A.9.5.3/11.5.2) · Password management system (A.9.5.4/11.5.3) · Information access restriction (A.9.6.1/11.6.1) |
Microsoft solutions have always included the ability to allocate different access levels to meet different organisational access security requirements, which is a key concept incorporated in AS7799. Microsoft solutions such as Microsoft Identity Integration Server (MIIS) provide organisations with a unified view of all known identity information about users, applications and network resources, simplifying their identity management problems. Active Directory Federation Services enables the sharing of identities across traditional security boundaries using ‘TrustBridge’ technologies that embrace Web Services Security (WS-Security) and other WS standards. |
Access Control · Network controls (A.8.5.1/10.6.1) · Policy on use of network services (A.9.4.1/11.4.4) · User authentication for external connections (A.9.4.3/11.4.2) |
Secure remote access is becoming a key business requirement and AS 7799 mandates consideration of appropriate security for all external connections to IT systems. Microsoft Remote Access solutions provide for strong authentication mechanisms to support secure external connections using Virtual Private Networks (VPN) technologies. |
System Development · Security requirements analysis and specification (A.10.1.1/12.1.1) · Input data validation (A.10.2.1/12.2.1) · Access control to program source code (A.10.4.3/12.4.3): |
Microsoft Developer Network (MSDN) provides whitepapers, guidelines and checklists to assist in developing applications which implement good security practices – including techniques such as input validation. These are supplemented with Prescriptive Architecture Guides which provide best practice for enterprise implementations. MS Press books, such as ‘Writing Secure Code’ are a key source of secure programming best practices. They include examples of code defects and discuss the vulnerabilities of applications to malicious attacks. |
System Maintenance · Change control procedures (A.10.5.1/12.5.1) · Restrictions on changes to software packages (A.10.5.3/12.5.3) · Information leakage (A.10.5.4/12.5.4) |
The Microsoft Operations Framework (MOF) provides operational guidance to enable organisations to achieve mission-critical system reliability, availability, supportability and manageability of Microsoft products and technologies. Microsoft is committed to helping organizations keep up by releasing patches in a controlled and manageable fashion. Technologies such as System Management Server (SMS), Windows Server Update Services (WSUS) and Software Update Services (SUS) provide for streamlined updating and deployment. |
Information Security Incident Management · Reporting information security events (A.6.3.1/13.1.1) · Learning from information security incidents (A.6.3.4/13.2.2) |
The Microsoft Security Response Centre (MSRC) provides global management of security vulnerabilities and security incidents to develop security updates and guidance to minimise the threat to customers. The Microsoft Trustworthy Computing initiative provides structured guidance on implementing processes that include aspects such as intrusion detection and responding to incidents to provide organisations with more effective security. This covers the full lifecycle process of managing a secure environment. |
Business Continuity Management · Including information security in the business continuity management process (A.11.1.1/14.1.1) · Business continuity planning framework (A.11.1.4/14.1.4) |
Microsoft is committed to helping organisations plan for disasters before they occur. Comprehensive guidance in the form of whitepapers, prescriptive architecture guidelines, reference architecture guidelines and checklists is included in the Microsoft Operations Framework to assist with effective Business Continuity Planning. Microsoft Consulting Services and Microsoft Partners can also provide specialist advice on planning disaster recovery solutions. |
Compliance · Compliance with security policies and standards (A.12.2.1/15.2.1) · Technical compliance checking (A.12.2.2/15.2.2) · Control of technical vulnerabilities (12.6.1) |
Technologies such as Group Policy, Windows Rights Management and System Management Server (SMS) provide effective management and enforcement of policy, copyright and licensing requirements.
Microsoft Baseline Security Analyser (MBSA) 2.0 scans business networks for missing security updates and common security misconfigurations and provides remedial advice..
|
Comments
- Anonymous
March 12, 2008
PingBack from http://bordercrossingstatsblog.info/a-pint-of-software-microsoft-and-the-as-7799iso-17799-standards-for/