Securing Azure resources with Privileged Identity Management
With Azure Active Directory Privileged Identity Management (PIM), you can now manage, control, and monitor access to Azure Resources within your organization. To learn more, see /en-us/azure/active-directory/privileged-identity-management/azure-pim-resource-rbac
It is important to have a Just In Time (JIT) capability to JIT into an Azure subscription for few hours to investigate any issues. However, once a bad guy has access to the subscription, he can get a lot of information out (like secrets, etc.) and do bad things even after the access is lost.
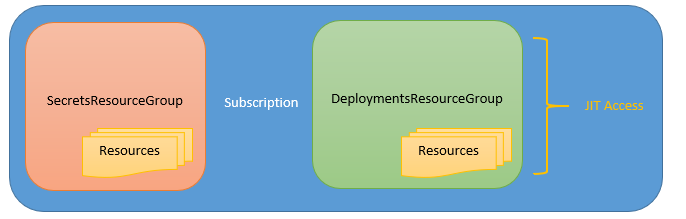
With PIM, you can assign JIT access not only at the subscription level but also at a specific Resource group or Resource level to prevent any information disclosure. Here is an example of how you can manage your subscription securely with PIM.
Create a Resource group for all your secrets. Let’s call it SecretsResourceGroup. This resource group can have the following resources:
- Azure Storage
- SQL Azure
- Cosmos DB
- Etc.
Create a Resource group for all your deployments. Let’s call it DeploymentsResourceGroup. This resource can have the following resources:
- Cloud Service
- Service Fabric
- App Service
- Virtual Machines
- Etc.
You will notice that almost anyone who needs access to the subscription actually needs access to a resource within DeploymentsResourceGroup. Typical scenarios include:
- Investigating live site issue with a specific deployment
- Restarting a VM
- Installing a software update
- Etc.
If they need access to multiple resources, you can assign them Eligible assignment on the Resource group. If they need access to a specific resource, you can assign them Eligible assignment on the specific resource. Now whenever, they need access, they can JIT into the specific resource at that time. You can also configure approval so that they can only JIT upon approval.
Thus, due to the granularity that PIM supports, you can now prevent people from accessing your secrets but still allow them to JIT into the specific resources where they need to investigate any issues.