XSS? - Do not Make Me Laugh, We Use WinForms
Reposted from XSS? - Do not Make Me Laugh, We Use WinForms
I find myself sometimes (actually too many times...) in situation explaining people of impact of Cross Site Scripting (attack) attacks as a result of importer encoding of user input (vulnerability) and how to counter this attack properly. Once all parties understand this everybody feels great relief since "our app is not web app - we use WinForms". Great!! The threat is mitigated by removing the feature of rendering HTML output...
"Hold it, you told me that your system presents to end user different types of documents, right?"
"Right, so?"
"Do you show HTML docs too?"
"Sure!"
"Great, and what do you use for it?"
"WebBrowser control, of course"
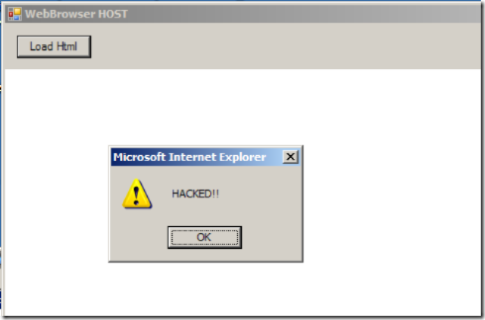
"I get it... So if you get HTML doc, it might include some script like this one:
<script>alert("HACKED!!")</script>
that can render as follows, right?"
"... right..."
How one prevents scripts running inside the WebBrowser control?
I did not find an easy way to control it other than using PINVOKE described here - https://msdn.microsoft.com/workshop/browser/hosting/wbcustomization.asp?frame=true Here is another post on that one - https://slingkid.blogsome.com/2006/05/26/ (that actually points back to the above link but has good interop example) and another discussion here - https://forums.microsoft.com/MSDN/ShowPost.aspx?PostID=66493&SiteID=1
Cheers
Comments
- Anonymous
October 24, 2007
XSSDetect public beta is now available for download on MSDN. Overview XSSDetect is a static code analysis - Anonymous
June 10, 2008
Using Windows Live Writer (WLW)? Writing posts takes you more time than you would like to invest? Looking