How To Hack WCF - New Technology, Old Hacking Tricks
First of I'd like to thank Guy for his excellent screencast - very convenient, so thanks.
Specifically I liked introductory screencast for WCF which can be found here: https://blogs.microsoft.co.il/blogs/bursteg/pages/WCF-Introduction-Demo-_2800_ScreenCast_2900_.aspx
It is dubbed in Hebrew, but the screens are flipping in so logical way so that one who does not understand Hebrew will be fine - go for it - recommended a lot for WCF newbies like me.
My interest was to understand the pipeline that the WCF Message goes through before it is put on the transport. The idea was to inject some custom modules (Inspectors) in the pipeline. Why? Is not it clear? To mess around with the message - tamper it in it raw format before it goes down to the transport signed and protected. Why? To show that it DOES NOT matter what communication technology you use - HTTP, Remoting, MSMQ, WCF, RMI, CORBA, DCOM, MQ, <<fill in your own here>> - the basic principle of VALIDATING INPUT ON THE SERVER SIDE is immutable.
Here I showed it for Web Services App Architecture with Security in mind - Video, Part I (that was easy - Fiddler is of much help here)
Then remoting came along - same result, here App Architecture with Security in mind - Video, Part II
Now it is mighty WCF.
I used excellent demo from Madhu here https://blogs.msdn.com/madhuponduru/archive/2006/07/19/671922.aspx that explained how to build IClientMessageInspector (NOTE - demo that works!)
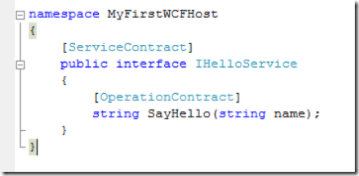
So here is the service contract:
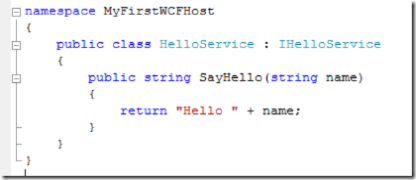
and the implementation:
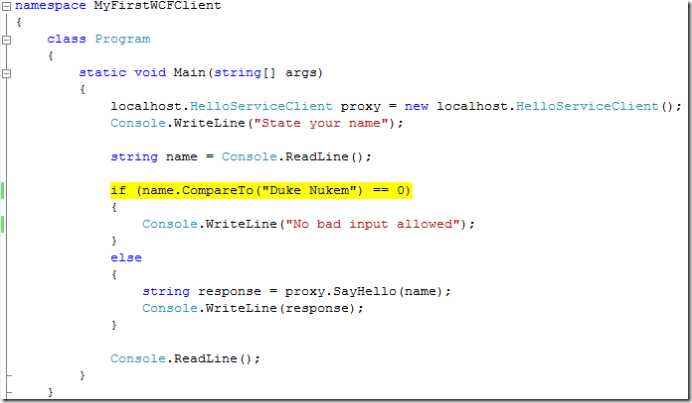
and the client side validation:
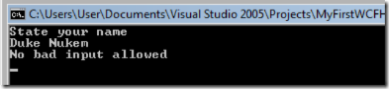
here is the client rejects the input:
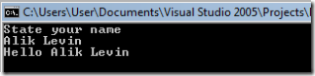
and here is the result of server processing for good input:
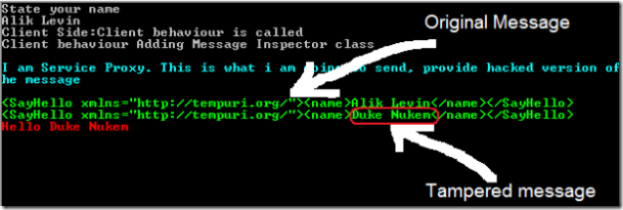
after adding the custom message inspector, I am offered to tamper the massage before it is sent to the service and the resulting reply from the service is in red at the bottom:
Conclusion
Does that mean that the communication technologies are bad? - NO, it is the way WE use it.
Here is an basic example for input validation in Web Services Web Service Input Validation - it has link to regex usage that you can use on the server side for input validation.
Enjoy
Comments
- Anonymous
March 04, 2007
PingBack from http://will.hughesfamily.net.au/20070305/livewriter-needs-fixing/ - Anonymous
April 18, 2007
Imagine if security was cool like Silverlight .... But security is not that cool, so the biggest challenge - Anonymous
April 26, 2007
I've been playing around a little with WCF, and will play it a lot next month (for my thesis). I've - Anonymous
May 17, 2007
My favorite design patterns is Provider design pattern (abstract factory – GoF definition) . I like it - Anonymous
May 31, 2007
I just finished building another security workshop that covers authentication and identity technologies - Anonymous
September 02, 2007
This session discusses common coding anti-patterns which usually lead to security vulnerabilities. Come - Anonymous
September 02, 2007
This session discusses common coding anti-patterns which usually lead to security vulnerabilities. Come - Anonymous
October 03, 2007
“As to methods there may be a million and then some, but principles are few. The man who grasps principles - Anonymous
December 26, 2007
This post to describe basic steps to write HttpModule and how it rescued mission critical application - Anonymous
January 14, 2008
The pattern is also called Intercepting Filter, Pipeline, AOP, and may be few more… I am confused - Anonymous
April 19, 2008
This is a digest of WCF Security resources I was collecting for some time. Drop me a comment in case - Anonymous
May 24, 2008
Input and Data Validation is one of the core security principles . WCF is no exception . To get most