Automating Code Review for Common ASP.NET Performance & Security Anti-Patterns
In this post I will share with you how to automate code review when searching MSIL for common performance and security anti-patterns.
Scenario
You are an application performance/security consultant who’s been asked to review a large application for common security and performance anti-patterns. You are given no time and no source code. What you are given is 250 dll’s. What do you do?
Reverse Engineer .Net Compiled Binaries
It is easy to reverse engineer compiled .Net binaries. .Net SDK ships with ILDASM – disassembler that dumps intermediate language (MSIL) out of the assemblies into text file. The resulting file is not really human readable (although there are few individuals out there who can actually really read it and understand), but it is good enough to perform text searches for several patterns. To perform text searches one would use findstr command. Here are few examples:
Find strings in resulted MSIL text file:
Ildasm.exe yourcomponent.dll /text | findstr ldstr
Find string constants in resulted MSIL text file:
Ildasm.exe yourcomponent.dll /text | findstr /C:"literal string"
Find boxing/unboxing in resulted MSIL text file::
Ildasm.exe yourcomponent.dll /text | findstr box
Ildasm.exe yourcomponent.dll /text | findstr unbox
The searches above can help identifying either security or performance issues.
The question here is how to automate the process for 250 dll’s.
Automating MSIL Search
The following are the steps we take to automate the search:
- Step 1 – Create list of dll’s using DIR command. First lets create an input file that includes the list of the dll’s we need to inspect. For that purpose we use DIR command with few attributes:
/A:-D means no directories, files only.
/S means search subfolders. It is useful if you have dll’s in subfolders.
/B means bare format, no headers, only file names.
DIR /A:-D /S /B *.dll >C:\DllsList.txt
Ok, now we have the text file – DllsList.txt – with the list of dll’s we want to inspect.
- Step 2 – Create vbs file the builds batch file with the actual commands
Now we create a vbs file that contains a script to build batch file. This batch includes search commands for each dll in the list we just created. In the sample below we create a batch file that will look for strings – ldstr . Substitute this search criteria to your needs.
=====VBS FILE START====
'ILDAMS FILE PATH
ildasmFilePath = """C:\Ildasm.exe"""
'ASSEMBLIES LIST TEXT FILE
assembliesFileList = "DllsList.txt"
'FINDSTR FILE PATH
findStrPath = "C:\Windows\System32\findstr.exe"
Set fso = CreateObject("Scripting.FileSystemObject")
'OPEN ASSEMBLIES LIST FILE FOR READ
Set assembliesList = fso.OpenTextFile(assembliesFileList, 1, False)
'OPEN TARGET BATCH FILE FOR WRITE
Set batchFile = fso.OpenTextFile(assembliesFileList & ".bat", 2, True)
'LOOP THROUGH ASSEMBLIES LIST AND ADD LINES TO BATCH FILE
Do While assembliesList.AtEndOfStream <> True
assemblyPath = assembliesList.ReadLine
stringToWrite = ildasmFilePath & " """ & assemblyPath & " "" /text | findstr ldstr >""" & assemblyPath & ".Strings.txt"""
batchFile.WriteLine stringToWrite
' msdbox stringToWrite
Loop
assembliesList.Close
batchFile.Close
Set assembliesList = Nothing
msgbox "DONE"
=====VBS FILE END====
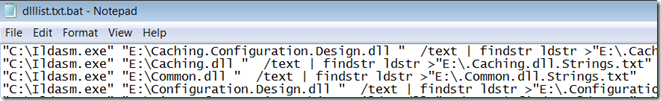
The result is a vbs file ready to be used. Double clicking on the vbs file creates a batch file with a similar name. Open the batch file and review the contents. It should look similar to this:
- Step 3 – Run the batch file to dump search results into text files
Now that we created the batch file – let’s run it. The result would be a bunch of text files with search criteria results in it. All that is left is inspect the files. For example, in case of security we’d look for a patterns outlined here:
- Code Inspection - First Look For What To Look For
- Security Code Review – String Search Patterns For Finding Input Validation Vulnerabilities
- Security Code Review – String Search Patterns For Finding Vulnerabilities In ASP.NET Web Application
In case of performance review we’d just go straight to the source code of the identified dll’s to look for massive boxing/unboxing which usually happens when we use general purpose collections.
To make the process of inspection easier and faster use instant search available in Outlook 2007 as it is outlined here: