A Domain Controller is not a Domain Computer
Today I spent half a day troubleshooting an issue with Authentication Silos that I finally tracked down to an unexpected issue with a Group Policy.
To give you a little background information: Authentication Silos are used to limit to which computers a user can log on. This is especially useful in Tier-0 configurations. To enable Authentication Policies you must enable Kerberos Armouring on both clients and KDCs, which is needed to support Silo claims. These switches are set through Group Policy.
So what happened was that a random team member decided to do some Group Policy hardening using security filtering. He wanted to make sure that users would not apply the policy set for Authentication Silos, so he removed the permission Authenticated Users:Apply and replaced it by domain computers:Apply.
The next morning the Silo was broken. Nobody could get in. Because there are quite a number of moving parts to Authentication Silos it took us a while to get down to the problem: no claims were generated, because the Group Policy was not applying to Domain Controllers. Which is pretty weird, because surely a Domain Controller is member of Domain Computers? Guess again:
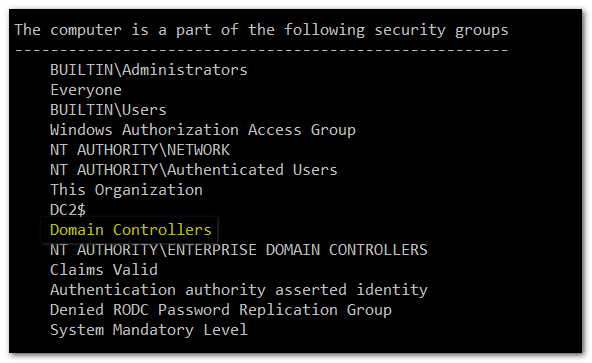
A DC is member of group Domain Controllers but not of Domain Computers! A little digging revealed the reason for this. These groups are designed as primary groups, and user or computer can only be member of one primary group. A normal computer has Domain Computers as its primary group. Once it gets promoted to a DC, the primary group changes to Domain Controllers, meaning that it leaves membership of Domain Computers...
Most (all?) of the guidance on Group Policy filtering gets this wrong, including the well-read blog Deploying Group Policy Security Update MS16-072 \ KB3163622 om remediating MS16-072:
If adding "Authenticated Users" with just "Read" permissions is not an option in your environment, then you will need to add the Domain Computers group with "Read" Permissions
So, the bottom line: if you use the group Domain Computers for any form of security filtering, be aware that you need to add DCs explicitly to the ACL using group Domain Controllers.