An unattended desktop flow run fails with the MSEntraMachineAlwaysPromptingForPassword error
This article provides a resolution for an error that occurs when you run an unattended desktop flow in Microsoft Power Automate for desktop.
Symptoms
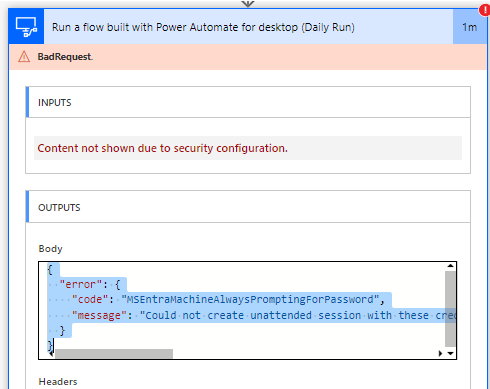
Your unattended desktop flow run fails with the "MSEntraMachineAlwaysPromptingForPassword" error code (formerly "AADMachineAlwaysPromptingForPassword").
{
"error":{
"code": "MSEntraMachineAlwaysPromptingForPassword",
"message": "Could not create unattended session with these credentials."
}
}
Cause
Power Automate for desktop can't validate your Microsoft Entra ID (formerly Azure Active Directory) credentials on the machine. This issue is typically caused by a group policy setting on your machine.
Resolution 1: Use Microsoft Entra authentication for Remote Desktop with a user certificate
This resolution requires Power Automate for desktop version 2.50 or later and must be used when no multifactor authentication (MFA) exception can be granted to the desktop flow connection account.
For steps on how to set up Microsoft Entra certificate based authentication for Power Automate, see Configure certificate-based authentication (preview).
Resolution 2: Use Microsoft Entra authentication for Remote Desktop with a username and password
This resolution requires Power Automate for desktop version 2.49 or later. If you don't have MFA enabled for the account used by the desktop flows connection, you can set up Microsoft Entra authentication using a username and password instead.
Open the Registry Editor (regedit) with administrative privileges. Navigate to the following registry path, create a new DWORD-32 value with the name
UseRdsAadAuthentication, and then set the value ofUseRdsAadAuthenticationto 1.Registry path Registry key DWORD-32 value Computer\HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Power Automate Desktop\Service UseRdsAadAuthentication1 Restart the Power Automate service.
Use a Microsoft Entra ID connection with username and password credentials. Note that an MFA exception is required for this account.
Resolution 3: Disable fPromptForPassword
To solve this issue, check the group policy setting on your machine.
Press the Windows key+R to open the Run dialog.
Type gpedit.msc and press Enter to open the Local Group Policy Editor.
Navigate to Computer Configuration > Administrative Templates > Windows Components > Remote Desktop Services > Remote Desktop Session Host > Security.
Look for the Always prompt for password upon connection setting.
If the setting is enabled, work with your IT department to disable the policy for that machine.
Note
This value is also reflected in the registry at Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows NT\Terminal Services. If the fPromptForPassword DWORD value for the Terminal Services key is set to 1, the setting is enabled, and you need to work with your IT department to disable it (simply changing the registry value is generally not sufficient, as it might be reverted.)
If the Always prompt for password upon connection setting isn't enabled but you receive the error code, type regedit in the Run dialog to open the Registry Editor. In the Registry Editor, navigate to the Computer\HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp registry key. Then, look for the fPromptForPassword DWORD and set it to 0. If the DWORD doesn't exist, create it and set its value to 0.