Scopes
Microsoft Fabric REST APIs require specific scopes to access various resources. These scopes are used to restrict access level of applications when they interact with Fabric REST APIs on behalf of users. This article describes how to use generic and specific types of scopes for Fabric REST APIs and create, read, update, and delete (CRUD) item APIs.
Note
Scopes only apply to delegated access on behalf of users. Direct access of Service Principals and Managed Identities to REST APIs is restricted by Fabric admin controls and Fabric permissions to artifacts. Generic and specific scopes are only relevant to item-level scopes.
The scopes required by Fabric REST APIs are listed in the Required Delegated Scopes section of each API reference page where scopes apply.
There are two types of scopes: Generic and specific. To decide between generic and specific scopes, you must weigh API permission security with API permission convenience. General scopes provide a simpler, easier to understand user consent experience. Specific scopes provide a more complex, higher security and more specific user consent prompt.
Generic scopes
Generic scopes are used with item create, read, update, and delete (CRUD) APIs and Fabric REST APIs.
Generic item CRUD scopes
Using generic CRUD scopes example: Item.ReadWrite.All creates a token that manages any item type.
Generic item CRUD user consent prompt API permission example:
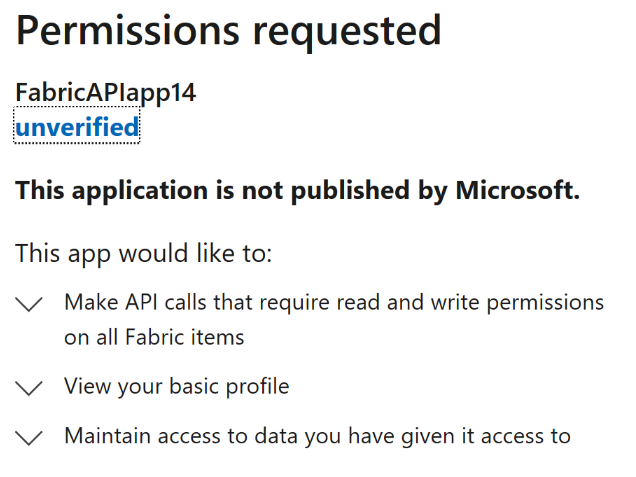
Generic Fabric REST APIs scopes
Here are four main types of generic Fabric REST APIs scopes:
Item.Read.All- Calling application is allowed to read all artifacts of type<itemType>that the user has access to.Item.ReadWrite.All- Calling application is allowed to read and write all Fabric items.Item.Execute.All- Calling application is allowed to execute on all Fabric items.Item.Reshare.All- Calling application is allowed to reshare all Fabric items.
Specific scopes
Specific scopes are used with item create, read, update, and delete (CRUD) APIs and Fabric REST APIs.
Specific item CRUD scopes
Using specific CRUD scopes creates a more granular token and allows users to grant specific consents.
Specific CRUD scopes are built in the following format: <itemType>.Read.All or <itemType>.ReadWrite.All, for example: Notebook.ReadWrite.All.
Specific CRUD scopes consent prompt example:
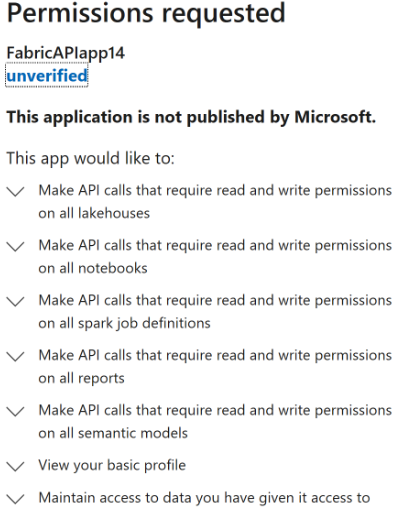
Specific Fabric REST APIs scopes
Using specific scopes creates a more secure token and allows specific consent to manage these specific item types.
Here are four main types of specific Fabric REST APIs scopes:
<itemType>.Read.All- Calling application is allowed to read all artifacts of type<itemType>that the user has access to.<itemType>.ReadWrite.All- Calling application is allowed to read and write all artifacts of type<itemType>that the user has access to.<itemType>.Execute.All- Calling application is allowed to execute all artifacts of<itemType>that the user has access to.<itemType>.Reshare.All- Calling application is allowed to reshare all artifacts of type<itemType>that the user has access to.
Other Fabric REST APIs scopes
There are other kinds of scopes in Fabric that follow similar patterns, for example: Workspace.ReadWrite.All.
For a full list of the Azure portal app scopes, open the Azure portal app and then navigate to: App registrations > YouAppRegistration > Add permissions > Power BI Service.
Related Content
- Microsoft Fabric access permissions: Introduction to permissions and consent.