Enable network isolation for Azure Monitor Agent by using Azure Private Link
By default, Azure Monitor Agent connects to a public endpoint to connect to your Azure Monitor environment. This article describes how to enable network isolation for your agents by using Azure Private Link.
Prerequisites
- A data collection rule (DCR), which defines the data Azure Monitor Agent collects and where the agent sends the data.
Create a data collection endpoint
Create a data collection endpoint (DCE) for each of your regions for agents to connect to instead of using the public endpoint. An agent can connect only to a DCE that's in the same region as the agent. If you have agents in multiple regions, create a DCE in each of the relevant regions.
Configure a private link
Configure your private link to connect your DCE to a set of Azure Monitor resources that define the boundaries of your monitoring network. This set is an instance of Azure Monitor Private Link Scope.
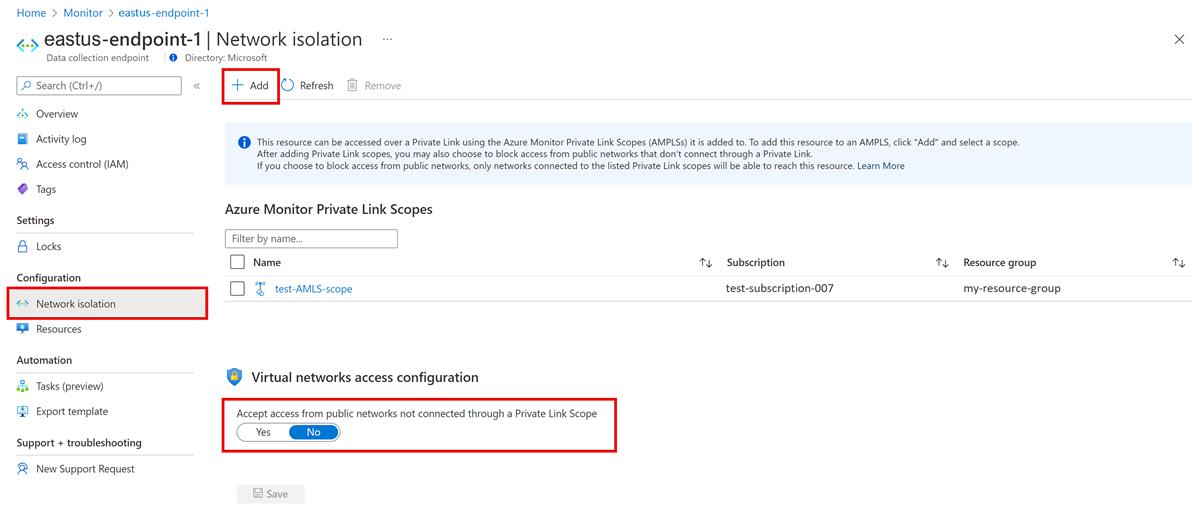
Add DCEs to Azure Monitor Private Link Scope
Add the DCEs to Azure Monitor Private Link Scope resource. This process adds the DCEs to your private Domain Name System (DNS) zone (see how to validate) and allows communication via private links. You can do this task from the Azure Monitor Private Link Scope resource or on an existing DCE resource's Network isolation tab.
Important
Other Azure Monitor resources like Log Analytics workspaces and DCEs in your DCRs that you send data to must be included in this Azure Monitor Private Link Scope resource.
Associate DCEs to target resources
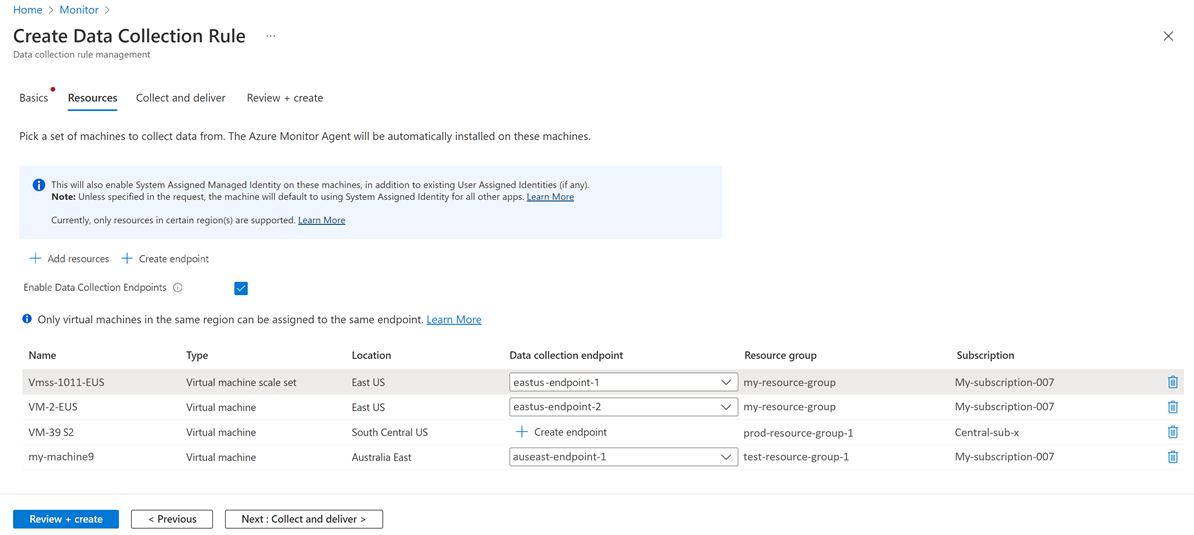
Associate the DCEs to the target resources by editing the DCR in the Azure portal. On the Resources tab, select Enable Data Collection Endpoints. Select a DCE for each virtual machine. For more information, see Configure data collection for the Azure Monitor Agent.
Related content
- Learn more about best practices for monitoring virtual machines in Azure Monitor.