Omezení Office 365 služeb na cloudové počítače
Správci můžou odepřít přístup ke službám Office 365 na jakémkoli jiném zařízení než na cloudovém počítači. Uděláte to tak, že nakonfigurujete Microsoft Entra zásady podmíněného přístupu a filtry zařízení, jak je popsáno v tomto článku. Pomocí těchto kroků můžete zajistit, aby uživatelé používali cloudové počítače jako své primární zařízení. Tímto způsobem můžete zlepšit zabezpečení podnikových prostředků a služeb.
Tento článek popisuje, jak omezit přístup ke službám Office 365. Stejnou strategii můžete použít s libovolnou cloudovou službou, která jako zdroj ověřování používá Microsoft Entra ID.
Vytvořte skupinu zabezpečení Microsoft Entra pro správu uživatelů, kteří budou řídit nové zásady. Do této skupiny přidejte všechny uživatele cloudových počítačů, kteří budou podléhat novým zásadám. Pouze uživatelé v této skupině budou při přístupu ke službám Office 365 omezeni na používání cloudových počítačů. Pokud chcete změnit přístup uživatele, stačí ho z této skupiny odebrat.
Přihlaste se k centru pro správu Microsoft Intune a vyberte Zabezpečení koncových bodů>Podmíněný přístup>Vytvořit novou zásadu.
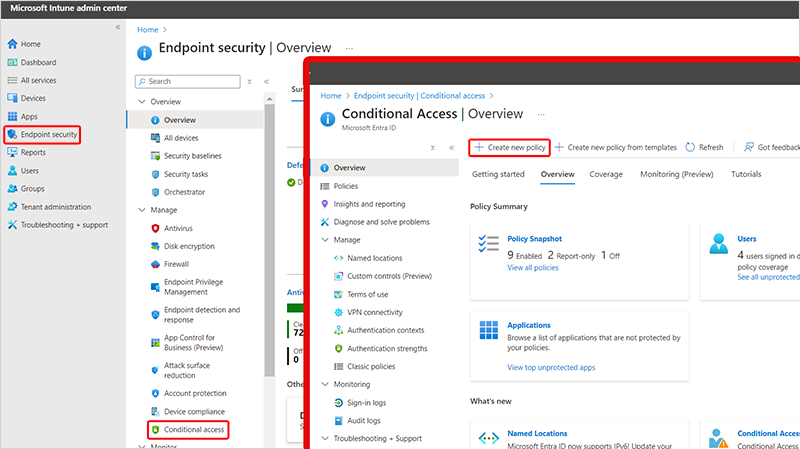
Zadejte Název nové zásady podmíněného přístupu. Například "Omezit Office 365 přístup k CPC".
Vyberte 0 uživatelů a skupin a vyberte>Zahrnout>Vybrat uživatele a skupiny>Uživatelé a skupiny> vyberte Microsoft Entra skupinu zabezpečení, kterou jste vytvořili >Vybrat.
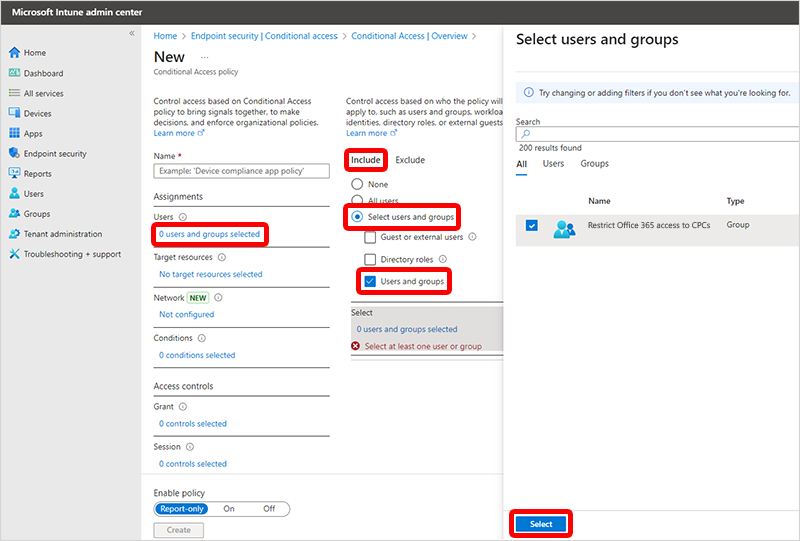
Vyberte Žádné cílové prostředky a vyberte>Zahrnout>: Vyberte aplikace>Žádné (v části Vybrat) > vyhledejte a vyberte Office 365>Vybrat.
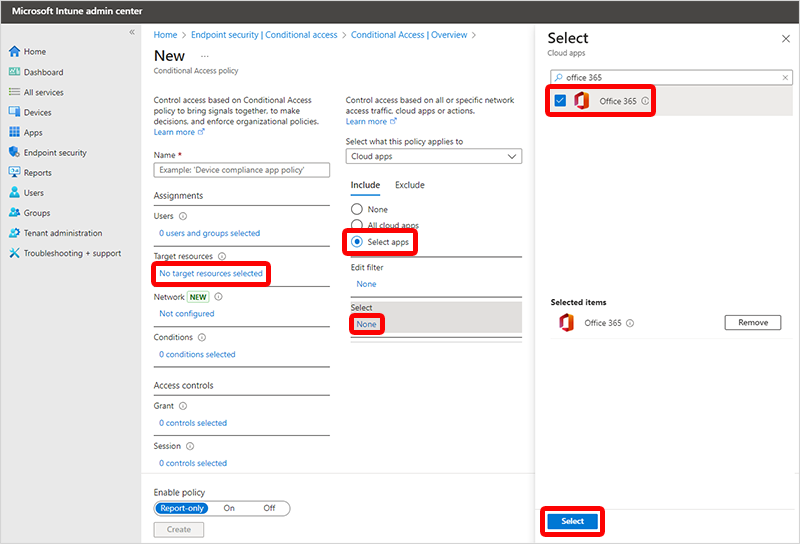
Vyberte Vyloučit>žádné (v části Vybrat vyloučené cloudové aplikace) > vyhledejte a vyberte Azure Virtual Desktop a Windows 365 aplikace >Vybrat.
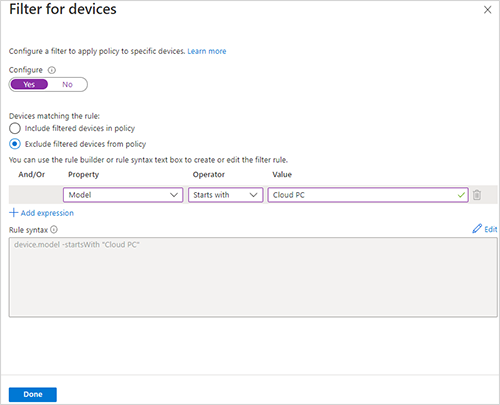
Vyberte 0 vybraných podmínek (v části Podmínky) >Nenakonfigurováno (v části Filtr pro zařízení).
V podokně Filtr pro zařízení :
- Nastavte Konfigurovat na Ano.
- Vyberte Vyloučit filtrovaná zařízení ze zásad.
- Vyberte možnost rozevíracího seznamu v části Model vlastností>.
- Vyberte možnost rozevíracího seznamu v části Operátor>začíná na.
- Do textového pole v části Hodnota zadejte hodnotu Cloud PC. Pokud se zásady vytváření názvů v Cloud PC změní, změňte hodnotu filtru tak, aby odpovídala názvům zařízení.
- Vyberte Hotovo a nastavte filtr.
Podle potřeby můžete v této zásadě nastavit více možností, ale takové doplňky jsou mimo rozsah tohoto článku.
Vyberte 0 vybraných ovládacích prvků (v části Udělit) >Blokovat výběr přístupu>.
Vyberte Zapnuto (v části Povolit zásadu). Tato zásada zakáže uživatelům přístup ke službám Office 365 na jiných než cloudových zařízeních PC. Pokud chcete zásadu monitorovat a před vynucováním ji vynutit, můžete vybrat možnost Pouze sestava.
Vyberte Vytvořit a dokončete vytváření zásad.
Poznámka
Pokud jste nakonfigurovali zásady zřizování tak, aby používaly jednotné přihlašování Microsoft Entra, možná budete muset také přidat Vzdálenou plochu Microsoftu do seznamu vyloučení v kroku 6, aby připojení jednotného přihlašování fungovala podle očekávání.
Další zařízení
Tuto ukázkovou zásadu je možné rozšířit tak, aby splňovaly další případy použití, jako je povolení přístupu k Office 365 službám z mobilních a tabletových zařízení uživatelů. Uděláte to tak, že provedete následující změny zásad:
- Na stránce zásad vyberte text v části Podmínky>nejsou nakonfigurované (v části Platformy zařízení).
- Výběrem možnosti Ano zapněte možnost konfigurace.
- Vyberte Zahrnout>jakékoli zařízení.
- Vyberte Vyloučit>Android a iOS.
- Vyberte Hotovo a nastavte filtr.
- Vyberte Uložit.