Step 4. Respond to an incident using Microsoft Sentinel and Microsoft Defender XDR
This article provides a general set of steps and procedures to resolve an incident using Microsoft Sentinel and Microsoft Defender XDR, which includes triage, investigation, and resolution. Microsoft Sentinel and Microsoft Defender XDR share:
- Updates on lifecycle (status, owner, classification) are shared between the products.
- Evidence gathered during an investigation is shown in the Microsoft Sentinel incident.
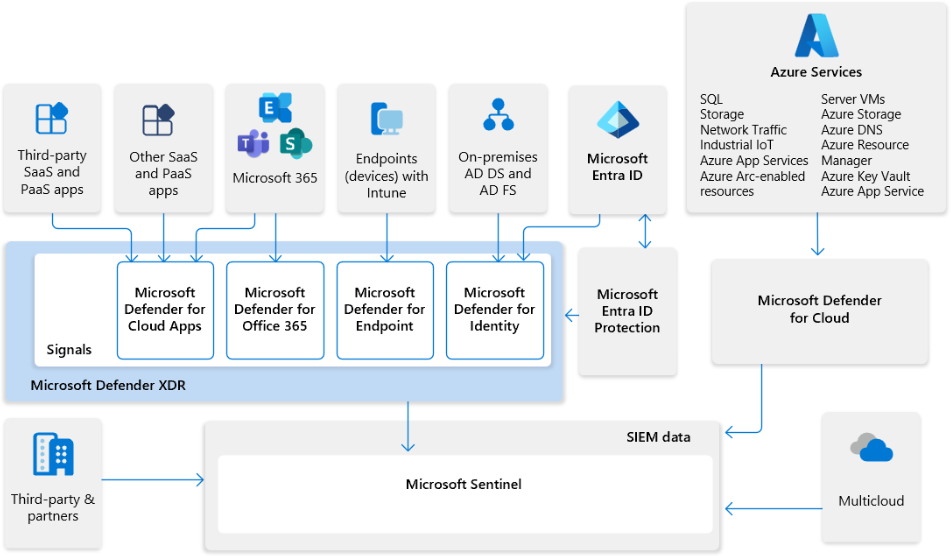
The following illustrations show how Microsoft’s extended detection and response (XDR) solution seamlessly integrates with Microsoft Sentinel, depending on whether you onboarded your Microsoft Sentinel workspace to the unified security operations platform in the Microsoft Defender portal.
The following illustration shows how Microsoft's XDR solution seamlessly integrates with Microsoft Sentinel with the unified security operations platform.
In this diagram:
- Insights from signals across your entire organization feed into Microsoft Defender XDR and Microsoft Defender for Cloud.
- Microsoft Sentinel provides support for multicloud environments and integrates with third-party apps and partners.
- Microsoft Sentinel data is ingested together with your organization's data into the Microsoft Defender portal.
- SecOps teams can then analyze and respond to threats identified by Microsoft Sentinel and Microsoft Defender XDR in the Microsoft Defender portal.
Incident response process
The process of incident response to resolve an incident using Microsoft Sentinel and Microsoft Defender XDR differs, depending on whether you onboarded your workspace to the unified security operations platform, and can access Microsoft Sentinel in the Defender portal.
Use the Defender portal to triage the potential incident, which includes understanding the details of the incident and taking immediate actions.
Continue the investigation in the Defender portal, including:
- Understanding the incident and its scope and reviewing asset timelines.
- Reviewing self-healing pending actions, manually remediating entities, performing live response.
- Adding prevention measures.
Use the Microsoft Sentinel area of the Defender portal deepen your investigation, including:
- Understanding the scope of the incident by correlating it with your security processes, policies, and procedures (3P).
- Performing 3P automated investigation and remediation actions and creating custom security orchestration, automation, and response (SOAR) playbooks.
- Recording evidence for incident management.
- Adding custom measures.
Resolve the incident and perform appropriate follow-up within your security team.
For more information, see:
Regardless of which portal you use, make sure to take advantage of Microsoft Sentinel's playbook and automation rule functionality:
A playbook is a collection of investigation and remediation actions that can be run from the Microsoft Sentinel portal as a routine. Playbooks can help automate and orchestrate your threat response. They can be run manually on-demand on incidents, entities, and alerts, or set to run automatically in response to specific alerts or incidents, when triggered by an automation rule. For more information, see Automate threat response with playbooks.
Automation rules are a way to centrally manage automation in Microsoft Sentinel, by allowing you to define and coordinate a small set of rules that can apply across different scenarios. For more information, see Automate threat response in Microsoft Sentinel with automation rules.
After onboarding your Microsoft Sentinel workspace to the unified security operations platform, note that there are differences in how automation functions in your workspace. For more information, see Automation with the unified security operations platform.
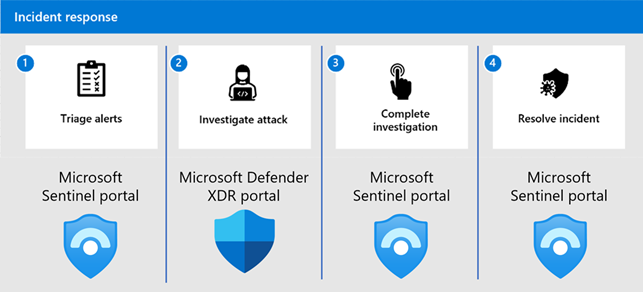
Step 1: Triage the incident
Use these steps as a general method to triage the incident with Microsoft Sentinel and Microsoft Defender XDR. If you've onboarded your workspace to the unified security operations platform, use the Defender portal. Otherwise, use the Azure portal.
To investigate Microsoft Sentinel incidents in the Defender portal:
In the Defender portal, select Investigation & response > Incidents & alerts > Incidents and locate the suspected incident. Filter your Service/detection sources to Microsoft Sentinel to help you narrow down the list of incidents to those coming from Microsoft Sentinel.
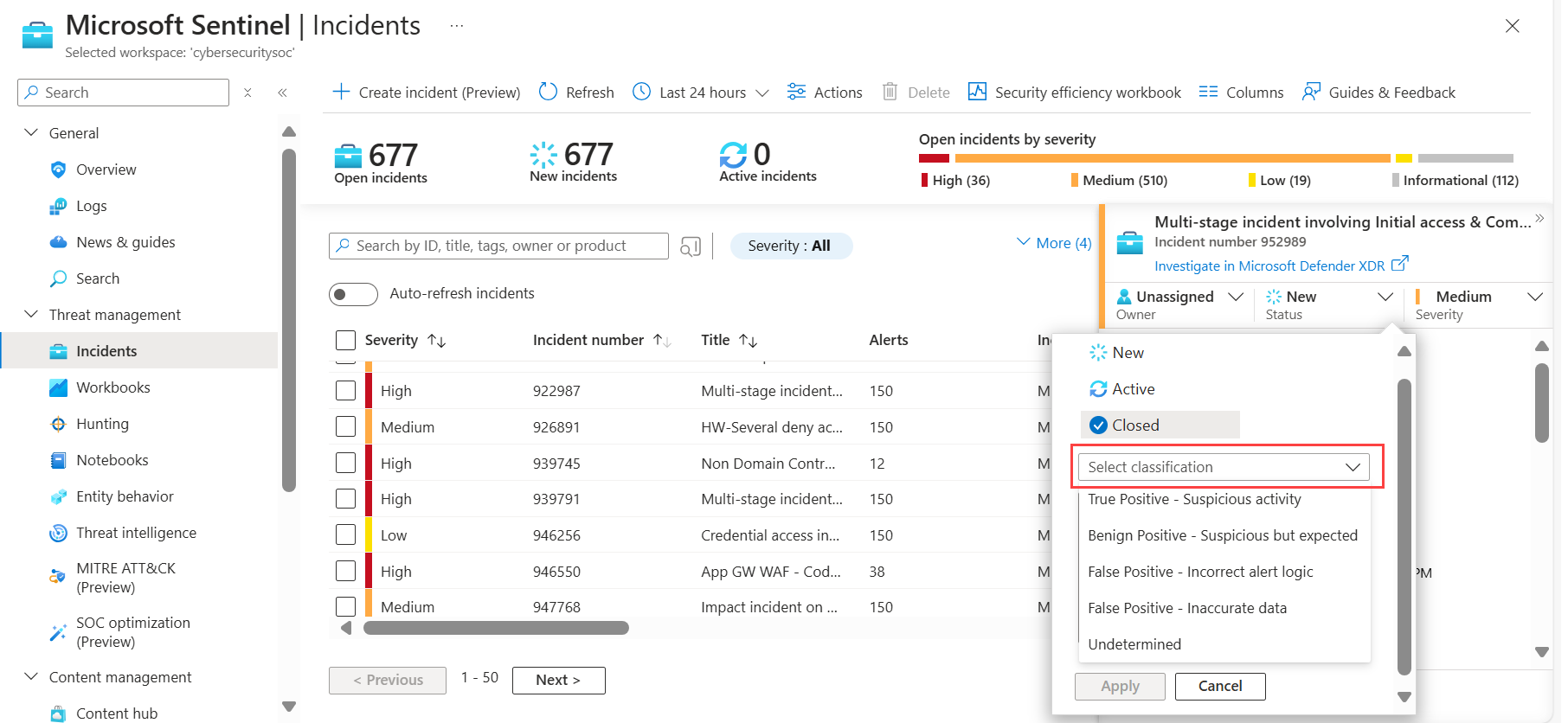
Select the incident row to view basic information in the incident summary pane.
Select Manage incident to update details like name, severity, status, classification, or to add comments. Select Save to save your changes.
Select Open incident page to continue the investigation.
Step 2: Investigate the incident
If your workspace is onboarded to the unified security operations platform, you stay in the Defender portal for this entire step. Otherwise, start in the Azure portal. You jump over to the Defender portal for some investigation, and then return to the Azure portal.
In the Defender portal, on the incident details page's Attack story tab, consider the following steps for your own incident response workflow:
View the attack story of the incident to understand its scope, severity, detection source, and what entities are affected.
Analyze the incident's alerts to understand their origin, scope, and severity with the alert story within the incident.
As needed, gather information on impacted devices, users, and mailboxes with the graph. Select on any entity to open a flyout with all the details.
See how Microsoft Defender XDR has automatically resolved some alerts with the Investigations tab.
As needed, use information in the data set for the incident from the Evidence and Response tab.
On the Assets tab, view the entities involved in the incident. Select a user account, a hostname, an IP address, or an Azure resource to continue investigating further on the entity details page. For example, if you selected a user, in the user details pane, select Go to user page to open the user's entity details page.
On the entity details page, select Sentinel events to view detailed timeline information about the selected entity, and entity insights.
Step 3: Resolve the incident
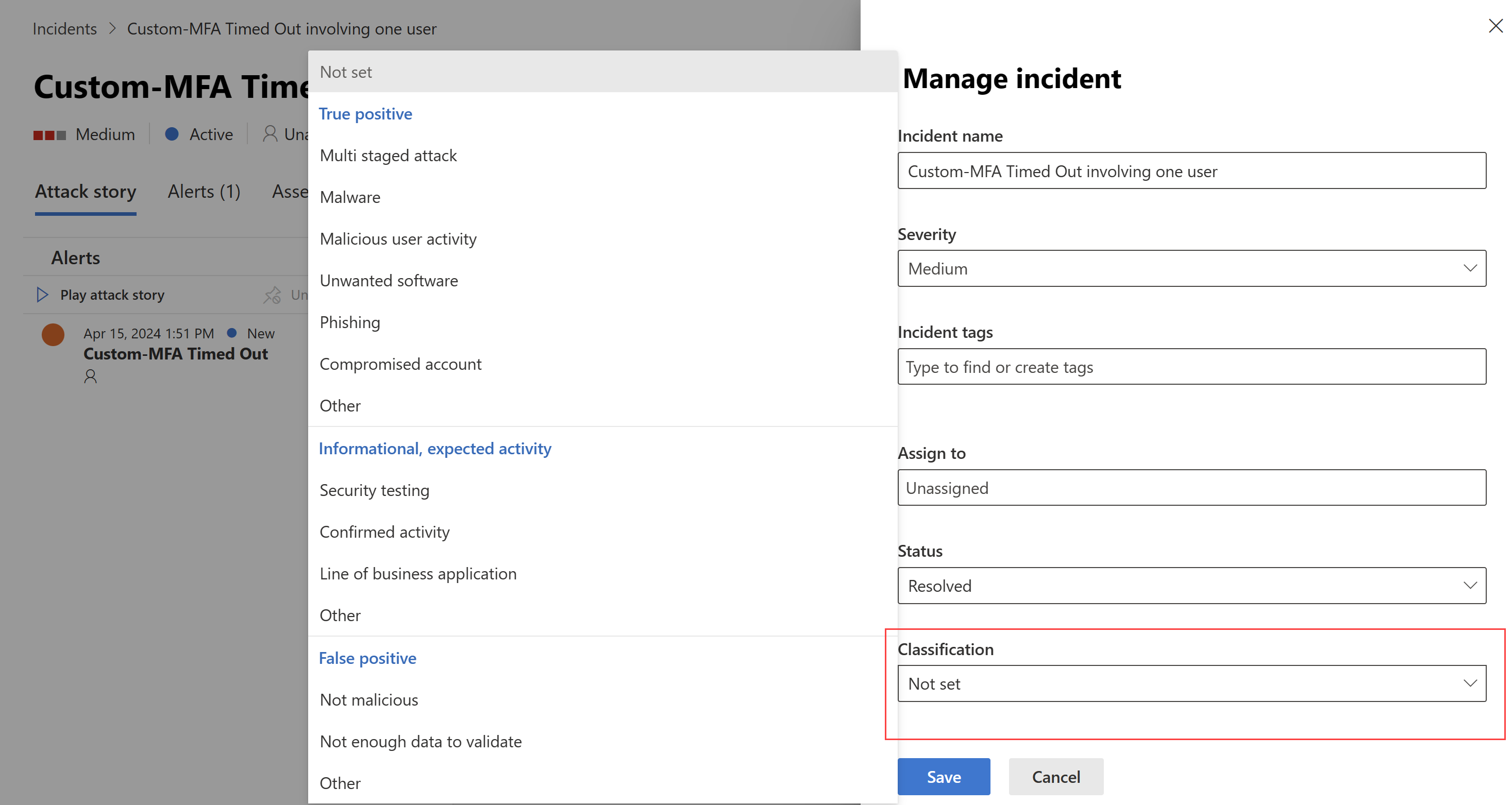
When your investigation has reached its conclusion and you have remediated the incident within the portals, resolve the incident by setting the incident’s status to Closed.
When marking an incident's status as Closed, make sure to select a classification, including true, benign, or false positive options.
For example:
For more information, see Resolve an incident in the Defender portal.
As needed, report the incident to your incident response lead for possible follow-up to determine more actions. For example:
- Inform your Tier 1 security analysts to better detect the attack early.
- Research the attack in Microsoft Defender XDR Threat Analytics and the security community for a security attack trend.
- As needed, record the workflow you used to resolve the incident and update your standard workflows, processes, policies, and playbooks.
- Determine whether changes in your security configuration are needed and implement them.
- Create an orchestration playbook to automate and orchestrate your threat response for a similar risk in the future. For more information, see Automate threat response with playbooks in Microsoft Sentinel.
Recommended training
The following are the recommended training modules for this step. Training content focuses on general availability features, and therefore doesn't include content for the unified security operations platform, which is in Preview.
Security incident management in Microsoft Sentinel
| Training | Security incident management in Microsoft Sentinel |
|---|---|
| In this module, you investigate Microsoft Sentinel incident management, learn about Microsoft Sentinel events and entities, and discover ways to resolve incidents. |
Improve your reliability with modern operations practices: Incident response
| Training | Training Improve your reliability with modern operations practices: Incident response |
|---|---|
| Learn the fundamentals of efficient incident response and the Azure tools that make them possible. |
Understand Microsoft 365 security incident management
| Training | Understand Microsoft 365 security incident management |
|---|---|
| Learn how Microsoft 365 investigates, manages, and responds to security concerns to protect customers and the Microsoft 365 cloud environment. |
Next steps
- See Navigate and investigate incidents in Microsoft Sentinel and Incident response with Microsoft Defender XDR for more details about incident response processes within the Microsoft Sentinel and Microsoft Defender portals.
- See Incident response overview for Microsoft security best practices.
- See Incident response playbooks for workflows and checklists to respond to common cyberattacks.
References
Use these resources to learn about the various services and technologies mentioned in this article:
- Microsoft Defender XDR integration with Microsoft Sentinel
- Unified SIEM and XDR capabilities interactive guide
- Automate threat response with playbooks in Microsoft Sentinel
- Automate threat response with playbooks
- Automate threat response in Microsoft Sentinel with automation rules
- Microsoft Defender XDR Threat Analytics
Use these resources to learn more about incident response: