Manage the workflow with the insider risk management users dashboard
Important
Microsoft Purview Insider Risk Management correlates various signals to identify potential malicious or inadvertent insider risks, such as IP theft, data leakage, and security violations. Insider risk management enables customers to create policies to manage security and compliance. Built with privacy by design, users are pseudonymized by default, and role-based access controls and audit logs are in place to help ensure user-level privacy.
The Users dashboard is an important tool in the insider risk management workflow and helps investigators and analysts have a more complete understanding of risk activities. This dashboard offers views and management features to meet administrative needs between the creating insider risk management policies and managing insider risk management cases.
After users are added to insider risk management policies, background processes are automatically evaluating user activities for triggering indicators. After triggering indicators are present, user activities are assigned risk scores. Some of these activities might result in an insider risk alert, but some activities might not meet a minimum risk score level and an insider risk alert won't be created. The Users dashboard allows you to view users with these types of indicators and risk scores, as well users that have active insider risk alerts.
Learn more about how the Users dashboard displays users in the following scenarios:
- Users with active insider risk policy alerts
- Users with triggering events
- Users identified as potential high impact users or in priority user groups
- Users added temporarily to policies
Tip
Get started with Microsoft Security Copilot to explore new ways to work smarter and faster using the power of AI. Learn more about Microsoft Security Copilot in Microsoft Purview.
Users with active insider risk policy alerts
The Users dashboard automatically displays all users with active insider risk policy alerts. These users with alerts have both a triggering indicator and an activity risk score that meets the requirements for creating an insider risk alert. Activities for these users are viewed by selecting the user in the Users dashboard and navigating to the User activity tab.
Users with triggering events
The Users dashboard automatically displays all users with triggering events, but that don't have an activity risk score that would create an insider risk alert. For example, a user with a reported resignation date is displayed because this activity is a triggering event but isn't an activity that has a risk score. Activities for these users are viewed by selecting the user in the Users dashboard and navigating to the User activity tab.
Users added temporarily to policies
The Users dashboard includes users added to insider risk management policies after an unusual event outside of the insider risk management workflow. Temporarily adding users (from the Policies dashboard) is also a way to start scoring user activity for an insider risk management policy for testing the policy, even if a required connector isn't configured.
When a user is manually added to a policy, the user activities for the previous 90 days are scored and added to the User activity timeline. For example, you have a user not currently being assigned risk scores for an insider risk policy and the user has data leak activities reported to the legal department in your organization. The legal department recommends that you configure new short-term detection requirements for the user. You can temporarily assign the user to your Data leaks policy for a designated length of time (activation window). All users added temporarily are displayed in the Users dashboard because triggering event requirements are waived.
Note
It might take several hours for new manually-added users to appear in the Users dashboard. Activities for the previous 90 days for these users might take up to 24 hours to display. To view activities for manually added users, select the user on the Users dashboard and open the User activity tab on the details pane.
The user is automatically removed from the Users dashboard and scoring stops when the time defined in the Activation window expires if:
- the user doesn't have any additional triggering events or insider risk policy alerts, and
- if the manually defined Activation window duration is longer than the global policy Activation window duration.
The Activation window setting with the longest duration always overrides the Activation window setting with a shorter duration. For example, you've configured the Activation window on the global Policy timeframes tab in the insider risk management global settings for 15 days, which is automatically applied to all your insider risk policies.
You temporarily add a user to your Data leaks insider risk policy and define 30 days as the Activation window for this user. The global Activation window setting of 15 days is overridden by defining the Activation window setting of 30 days for the temporarily added user. The temporarily added user will remain in the Users dashboard and be in-scope for the policy for 30 days.
In the opposite scenario where the global Activation window setting is longer than the Activation window setting defined for a temporarily added user, the global Activation window setting would override the Activation window setting for the temporarily added user. The temporarily added user will remain in the Users dashboard and be in-scope for the policy for the number of days defined in the global Activation window settings.
View user information on the Users dashboard
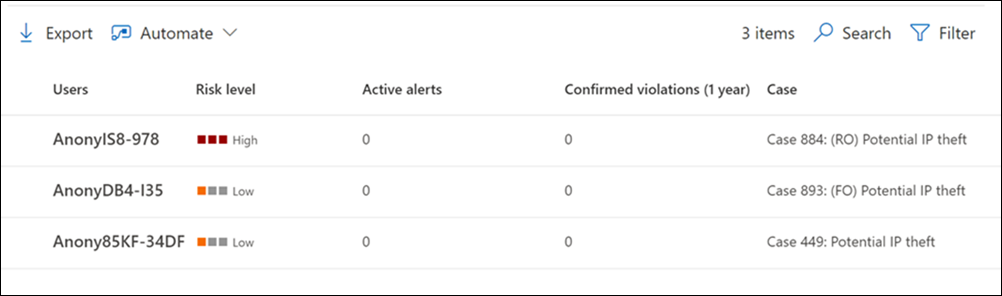
Each user displayed in the Users dashboard has the following information:
- Users: Username for a user. This field is anonymized if the global anonymization setting for insider risk management is enabled.
- Alert severity level: Current calculated risk level of the user. This score is calculated every 24 hours and uses the alert risk scores from all active alerts associated with the user. For users with only triggering indicators, the alert severity level is zero.
- Active alerts: Number of active alerts for all policies.
- Confirmed violations: Number of cases resolved as confirmed policy violation for the user.
- Case: Current active case for the user.
To quickly locate a specific user, use Search at the top right of the Users dashboard. When searching for users, you must use the user principal name (UPN). For example, when searching for a user named 'Tiara Hidayah' that has a UPN of 'thidayah' in your organization, you would enter 'thidayah' or some part of the UPN in Search.
Note
The number of users displayed on the Users dashboard might be limited in some instances, depending on the volume of active alerts and matching policies. Users with active alerts are displayed on the Users dashboard as the alerts are generated, and there might be rare cases when the maximum number of displayed users is reached. If this limit happens, users with active alerts who aren't displayed are added to the Users dashboard as existing user alerts are triaged.
View user details
To view more details about risk activity for a user, open the user details pane by double-clicking a user in the Users dashboard. On the details pane, you can view the following information:
User profile tab
- Name and title: Name and position title for the user from Microsoft Entra ID. These user fields are anonymized or empty if the global anonymization setting for insider risk management is enabled.
- User details: Lists whether the user has been identified as a potential high impact user or if the user is in priority user groups.
- Alert and activity summary: Lists active user alerts and open cases.
- User email: Email address for the user.
- Alias: Network alias for the user.
- Organization or department: Organization or department for the user.
- In scope: Lists in-scope assignment of the user to policies.
User activity tab
- History of recent user activity: Lists both triggering indicators and insider risk indicators for risk activities up to the last 90 days. All risk activities pertinent to insider risk indicators are also scored, though the activities might or might not have generated an insider risk alert. Triggering indicator examples might be a resignation date or the last scheduled date of work for the user. Insider risk indicators are activities determined to have an element of risk, which might potentially lead to a security incident, and are defined in policies that the user is included in. Event and risk activities are listed with the most recent item listed first.
Use Copilot to summarize user activities (preview)
You can select Summarize with Copilot on the user details pane to quickly summarize the activities for users that might need further investigation. When you summarize user risk activities with Microsoft Copilot in Microsoft Purview, a Copilot pane appears on the right side of the screen with a user summary.
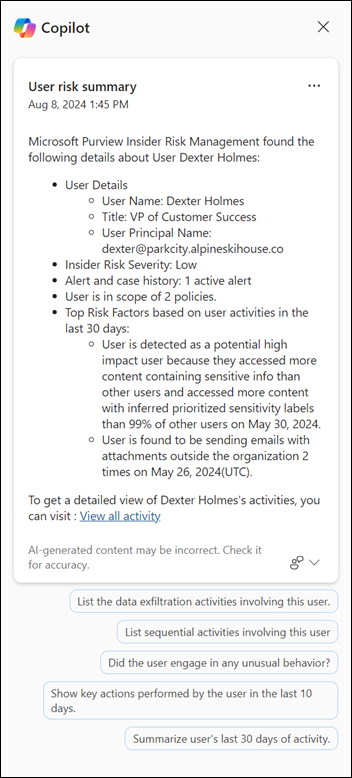
The user summary includes essential details such as the user’s name, title, user principal name, alert and case history, and top risk factors. The top risk factors provide crucial insights into the user roles, permissions, involvement in exfiltration activities, sequential patterns, or any unusual behavior. This view helps identify users who might pose the highest insider risk to your organization.
Suggested prompts are automatically listed to help further refine your summary and to help provide additional insights to the activities associated with the user. Choose from the following suggested prompts:
- List all the data exfiltration activities involving this user.
- List all the sequential activities involving this user.
- Did the user engage in any unusual behavior?
- Show key actions performed by the user in the last 10 days.
- Summarize user's last 30 days of activity.
Tip
You can also use the standalone version of Microsoft Security Copilot to investigate insider risk management, Microsoft Purview data loss prevention (DLP), and Microsoft Defender XDR alerts.
Remove users from in-scope assignment to policies
There might be scenarios where you need to stop assigning risk scores to a user in insider risk management policies. Use Stop scoring activity for users on the Users dashboard to stop assigning risk scores for a user from all insider risk management policies that they are currently in scope for. This action does not remove the user from the overall policy assignment (when you add users or groups to a policy configuration), but simply removes the user from active processing by policies after current triggering events. If the user has another triggering event in the future, risk scores from policies will automatically begin to be assigned to the user again. Any existing alerts or cases for this user will not be removed.
Remove a user from in-scope status in all insider risk management policies
Select the appropriate tab for the portal you're using. Depending on your Microsoft 365 plan, the Microsoft Purview compliance portal is retired or will be retired soon.
To learn more about the Microsoft Purview portal, see Microsoft Purview portal. To learn more about the Compliance portal, see Microsoft Purview compliance portal.
- Sign in to the Microsoft Purview portal using credentials for an admin account in your Microsoft 365 organization.
- Go to the Insider Risk Management solution.
- Select Users in the left navigation.
- On the Users dashboard, select the user(s) you want to stop scoring activity for.
- Select Stop scoring activity for users.
Note
Removing a user from in-scope status might take several minutes. Once complete, the user will not be listed on the Users dashboard. If the removed user has active alerts or cases, the user will remain on the Users dashboard and the user details will show that they are no longer in-scope for a policy.
Run automated tasks with Power Automate flows for a user
Using recommended Power Automate flows, risk investigators and analysts can quickly take action to notify users when they're added to an insider risk policy.
To run, manage, and create Power Automate flows for insider risk management users:
- Select Automate on the user action toolbar.
- Choose the Power Automate flow to run, then select Run flow.
- After the flow has completed, select Done.
To learn more about Power Automate flows for insider risk management, see Getting started with insider risk management settings.