Use communication compliance reports and audits
Important
Microsoft Purview Communication Compliance provides the tools to help organizations detect regulatory compliance (for example, SEC or FINRA) and business conduct violations such as sensitive or confidential information, harassing or threatening language, and sharing of adult content. Communication Compliance is built with privacy by design. Usernames are pseudonymized by default, role-based access controls are built in, investigators are opted in by an admin, and audit logs are in place to help ensure user-level privacy.
Reports
Note
At this time, if your role is scoped by one or more admin units, the admin units aren't applied to reports. You can see all reports in the organization.
The Reports dashboard is the central location for viewing all communication compliance reports. To view and manage reports, users must be assigned to the Communication Compliance Viewers role group.
Report widgets provide a quick view of insights most commonly needed for an overall assessment of the status of communication compliance activities. Information contained in the report widgets isn't exportable. Detailed reports provide in-depth information related to specific communication compliance areas and offer the ability to filter, group, sort, and export information while reviewing.
For the date range filter, the date and time for events are listed in Coordinated Universal Time (UTC). When filtering messages, all filters for the report are made applicable at the 00:00:00 UTC start date to the 23:59:59 UTC end date.
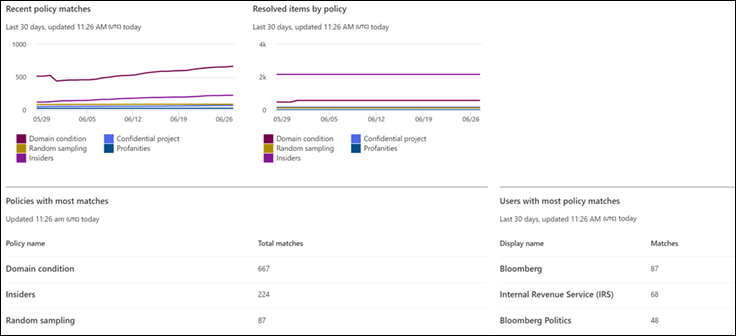
The Reports dashboard contains the following report widgets and detailed reports links:
Report widgets
- Recent policy matches: displays the number of matches by active policies over time.
- Resolved items by policy: displays the number of policy match alerts resolved by policies over time.
- Policy with most matches: displays the policies and the number of matches for a given period, ranked highest to lowest for matches.
- Users with most policy match: displays the users (or anonymized usernames) and number of policy matches for a given period.
- Escalations by policy: displays the number of escalations per policy over a given time.
Detailed reports
Use the Export report option to create a .CSV file containing the report details for any detailed report. The Export report option supports file size downloads up to 3 MB.
Policy settings and status: provides a detailed look at policy configuration and settings, as well as the general status for each of the policy (matches and actions) on messages. Includes policy information and how policies are associated with users and groups, locations, review percentages, reviewers, status, and when the policy was last modified. Use the Export option to create a .CSV file containing the report details.
Items and actions per policy: Review and export matching items and remediation actions per policy. Includes policy information and how policies are associated with:
- Items matched
- Escalated items
- Resolved items
- Tagged as compliant
- Tagged as noncompliant
- Tagged as questionable
- Items pending review
- User notified
- Case created
Item and actions per location: Review and export matching items and remediation actions per Microsoft 365 location. Includes information about how workload platforms are associated with:
- Items matched
- Escalated items
- Resolved items
- Tagged as compliant
- Tagged as noncompliant
- Tagged as questionable
- Items pending review
- User notified
- Case created
Activity by user: Review and export matching items and remediation actions per user. Includes information about how users are associated with:
- Items matched
- Escalated items
- Resolved items
- Tagged as compliant
- Tagged as noncompliant
- Tagged as questionable
- Items pending review
- User notified
- Case created
Note
The items and actions displayed are only for the items and actions matched during the date range included in the date range filter mentioned previously.
Sensitive information type per location (preview): Review and export information about the detection of sensitive information types and the associated sources in communication compliance policies. Includes the overall total and the specific breakdown of sensitive information type instances in the sources configured in your organization. The values for each third-party source are displayed in separate columns in the .CSV file. Examples are:
- Email: Sensitive information types detected in Exchange email messages.
- Teams: Sensitive information types detected in Microsoft Teams channels and chat messages.
- Microsoft 365 Copilot and Microsoft 365 Copilot Chat: Sensitive information types detected in Copilot interactions.
- Viva Engage: Sensitive information types detected in Viva Engage inboxes, posts, chats, and replies.
- Third-party sources: Sensitive information types detected for activities associated with third-party connectors configured in your organization. To view the breakdown of third-party sources for a specific sensitive information type in the report, hover your mouse over the value for the sensitive information type in the Third-party source column.
- Other: Sensitive information types used for internal system processing. Selecting or deselecting this source for the report won't affect any values.
Email blast senders: Review and export the list of senders of email blast messages that were filtered out from your communication compliance policies to reduce "noise." Filter email blasts is a communication compliance policy setting. The Email blast senders report includes the following fields:
- Policy name
- Policy last modified date
- Sender
- Number of mails filtered
Export a message details report
You can create custom reports and review details for messages brought into the scope of specific policies. These reports can be used for all-up reviews of messages and for creating a report snapshot for a customizable time period. You can create a one-time report, or if you often need to create the same report, you can schedule report creation on a daily, weekly, or monthly basis. You can create up to five schedules per policy.
When a report is created, reviewers for the policy receive an email notification with a link to the Exports tab, where they can download the report as a CSV file.
Create the report
Select the appropriate tab for the portal you're using. Depending on your Microsoft 365 plan, the Microsoft Purview compliance portal is retired or will be retired soon.
To learn more about the Microsoft Purview portal, see Microsoft Purview portal. To learn more about the Compliance portal, see Microsoft Purview compliance portal.
Sign in to the Microsoft Purview portal using credentials for an admin account in your Microsoft 365 organization.
Go to the Communication Compliance solution.
Select Policies in the left navigation.
Select a policy, then select Export report in the upper-right corner of the page.
On the Export options pane, under Include items from these users, select one of the following:
- All users. Select this option if you want to create a report with message information for all users in the policy.
- Select users. Select this option, and then select specific users from the list, to create a report with messages sent by those specific users. Only the users who have sent a message that has been flagged are available in the list.
In the Select frequency list, select how often you want to create the report.
If it's a one-time report, enter a start date and end date for the report. If it's a recurring report, enter a date to start sending reports and a date to stop sending reports.
Note
If you select Daily, Weekly, or Monthly for a recurring report, the report starts collecting messages from the previous day, week, or month, depending on which option you select. For example, if you choose Daily as the frequency and choose June 4, 2024 as the start date for the report, the report starts collecting messages on June 3.
In the Send report to these reviewers list, make any changes that you want by adding or deleting reviewers. By default, all reviewers for the policy (added during policy creation) are listed.
In the Report name field, accept the suggested name for the report or change it as needed.
Select Create report (for one-time reports) or Start scheduled export (for recurring reports).
The Preparing scheduled report dialog box appears.
To view the schedule of reports, select Manage scheduled exports.
Tip
You can also edit a report schedule by selecting Manage scheduled reports from the Exports tab.
To make changes to a scheduled report:
- Select the checkbox for the report, and then select Edit.
- In the Export options dialog box, make the changes that you want.
Note
If you want to change the frequency or start date of the report, delete the report in the previous screen, and then create the report again.
Note
You can create up to five scheduled reports per policy. If you already have five scheduled reports for a policy and you want to create a new one, you have to delete one of the existing report schedules before you can create a new one.
Download a report when it's ready
The time it takes to create a report depends on the number of scheduled reports and the size of the reports. Reviewers on the policy receive an email notification with a link to the Exports tab when a report is ready. To download a report from the Exports tab, select a report in the Ready to download state, and then select Download export(s) over the list.
Note
If your selected time period doesn't return any message results in the report, it means there were no messages for the selected time period. The report is blank.
What's included in a Message details report
Message details reports contain the following information for each message item in the policy:
- Match ID: Unique ID for a copy of the message in communication compliance.
- Internet Message ID: Unique ID for the message across platforms.
- Conversation Family ID: Thread ID for the message.
- Sender column: Sender of the message. If the policy match is a response from Microsoft 365 Copilot and Microsoft 365 Copilot Chat, the value is "Copilot".
- Recipient column: Recipients included in the message. If the policy match is a prompt to Copilot, the value is "Copilot".
- Date: The date when the message was sent.
- Location: Channel that the message was sent on. This can be Exchange Online, Teams, Viva Engage, or any third-party channel supported by communication compliance.
- Subject: Subject of the message. If it's a Copilot interaction, the subject of the message is "Copilot" and the name of the Microsoft 365 app. For example: "Copilot in Excel".
- Contains Attachments: Status of any attachments for the message. Values are either Yes or No.
- Policy Name: Name of the policy associated with the message. This value is the same for all messages in the report.
- Item Status: Status of the message item in the policy. Values are Pending or Resolved.
- Tags: Tags assigned to the message. Values are Questionable, Compliant, or Noncompliant.
- Keyword Matches: Keyword matches for the message.
- Trainable Classifier ID: ID of the trainable classifier that was matched.
- Trainable Classifier Name and Matched Keywords: The name of the trainable classifier and the keywords that triggered the classifier match.
- Reviewers: Reviewers assigned to message.
- Pending for (days): Number of days the message has been in a pending state. For resolved messages, the value is 0.
- Comment for Resolved: Comments for the message entered when resolved.
- Resolved Date: Date and Coordinated Universal Time (UTC) the message was resolved.
- Last Updated By: User name of the last updater.
- Last Updated On: Date and Coordinated Universal Time (UTC) the message was last updated.
- History of Comments: List of all comments for the message alert, including comment author and date and Coordinated Universal Time (UTC) of the comment.
Tip
You can also select and export specific message details as a downloadable file
Audit
In some instances, you must provide information to regulatory or compliance auditors to prove that user activities and communications are scoped. This information may be a summary of all activities associated with a defined organizational policy or anytime a communication compliance policy changes. Communication compliance policies have built-in audit trails for complete readiness for internal or external audits. Detailed audit histories of every create, edit, and delete action are captured by your communication policies to provide proof of scoped procedures.
Important
Auditing must be enabled for your organization before communication compliance events are recorded. To enable auditing, see Enable the audit log. When activities trigger events that are captured in the Microsoft 365 Audit log, it may take up to 48 hours before these events can be viewed in communication compliance policies.
To view communication compliance policy update activities, select the Export policy updates control on the main page for any policy. You must be assigned the Global Admin or Communication Compliance Admins roles to export update activities. This action generates an audit file in the .CSV format that contains the following information:
Important
Microsoft recommends that you use roles with the fewest permissions. Minimizing the number of users with the Global Administrator role helps improve security for your organization. Learn more about Microsoft Purview roles and permissions.
| Field | Details |
|---|---|
| CreationDate | Date the update activity was performed in a policy. |
| UserIds | User that performed the update activity in a policy. |
| Operations | Update operations performed on the policy. |
| AuditData | Main data source for all policy update activities. All update activities are recorded and separated by comma delimiters. |
To view communication compliance review activities for a policy, select the Export review activities control on the Overview page for a specific policy. You must be assigned the Global Admin or Communication Compliance Admins roles to export review activities. This action generates an audit file in the .CSV format that contains the following information:
Important
Microsoft recommends that you use roles with the fewest permissions. Minimizing the number of users with the Global Administrator role helps improve security for your organization. Learn more about Microsoft Purview roles and permissions.
| Field | Details |
|---|---|
| CreationDate | Date the review activity was performed in a policy. |
| UserIds | User that performed the review activity in a policy. |
| Operations | Review operations performed on the policy. |
| AuditData | Main data source for all policy review activities. All review activities are recorded and separated by comma delimiters. |
You can also view audit activities in the unified audit log or with the Search-UnifiedAuditLog PowerShell cmdlet. To learn more about audit log retention policies, see Manage audit log retention policies.
For example, the following example returns the activities for all the scoped review activities (policies and rules):
Search-UnifiedAuditLog -StartDate $startDate -EndDate $endDate -RecordType AeD -Operations SupervisoryReviewTag
This example returns the update activities for your communication compliance policies:
Search-UnifiedAuditLog -StartDate $startDate -EndDate $endDate -RecordType Discovery -Operations SupervisionPolicyCreated,SupervisionPolicyUpdated,SupervisionPolicyDeleted
This example returns activities that match your current communication compliance policies:
Search-UnifiedAuditLog -StartDate $startDate -EndDate $endDate -Operations SupervisionRuleMatch
Communication compliance policy matches are stored in a scoped mailbox for each policy. In some cases, you may need to check the size of your scoped mailbox for a policy to make sure you aren't approaching the current 100-GB storage size or 1 million message limit. If the mailbox limit is reached, policy matches aren't captured and you need to create a new policy (with the same settings) to continue to capture matches for the same activities.
To check the size of a scoped mailbox for a policy, complete the following steps:
Run the following command:
ForEach ($p in Get-SupervisoryReviewPolicyV2 | Sort-Object Name) { "<Name of your communication compliance policy>: " + $p.Name Get-MailboxStatistics $p.ReviewMailbox | ft ItemCount,TotalItemSize }