Use case: Triage incidents based on enrichment from threat intelligence
Roles mentioned: SOC analyst and identity admin for incident triage (main), CISO and other stakeholders for incident report summary (recipient)
Scenario
As a security operations center (SOC) analyst, you review alerts and incidents assigned to you. Your duty is to identify if real action needs to be taken. You leverage information within the alerts associated with the incident to guide your process. You often collect contextual information to further understand the next steps you should take. With the enrichment of involved entities and full understanding of the underlying alerts, you determine whether to escalate or remediate the incident.
In this detailed example, an analyst uses Security Copilot to quickly triage an incident. If the incident is a real threat, the goal is to either gather new indicators of compromise or link entities to finished intelligence. In this case, the threat intelligence is summarized by Security Copilot to show the connection to a known threat actor and inform the severity assessment.
Steps
Start your day with Security Copilot. Retrieve the latest Microsoft Defender XDR incident that's assigned to you and summarize the alerts associated with it.
Prompt used:
What is the latest active Defender incident assigned to me,
angus.macgregor@contoso.com? Summarize it, including the alerts associated with it.Response:
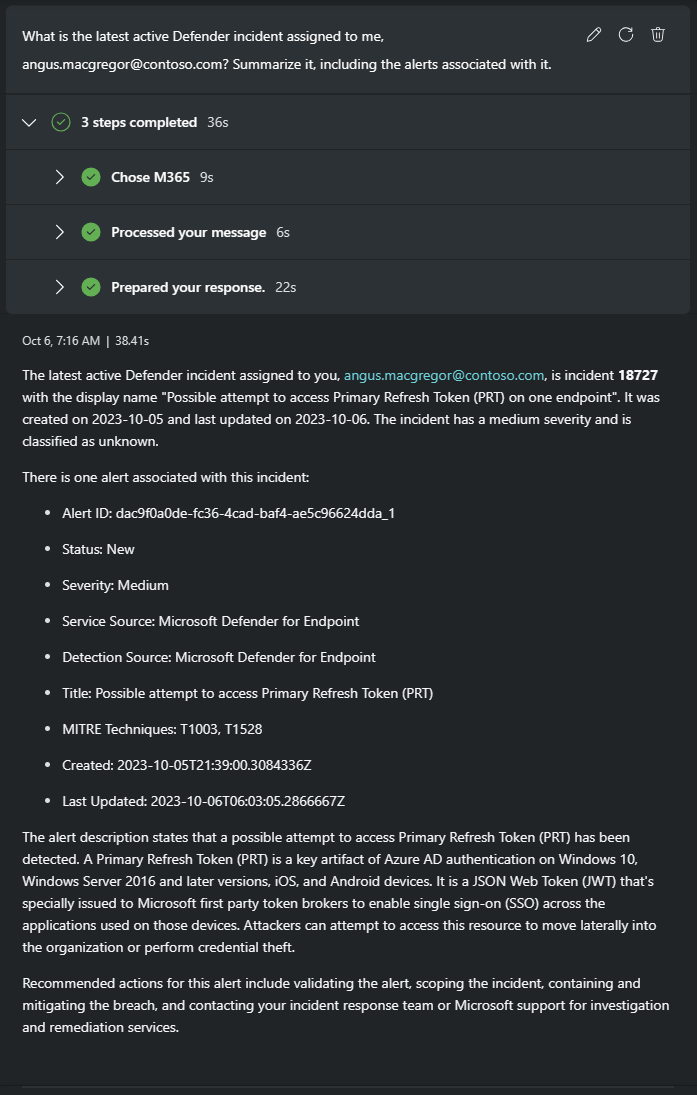
Looks like possible credential theft. You follow the recommended actions and begin to scope the incident and validate the alert.
Focus in on specific entities to get more information about them.
Prompt used:
Elaborate on the details of this alert including the entities involved.
Response:
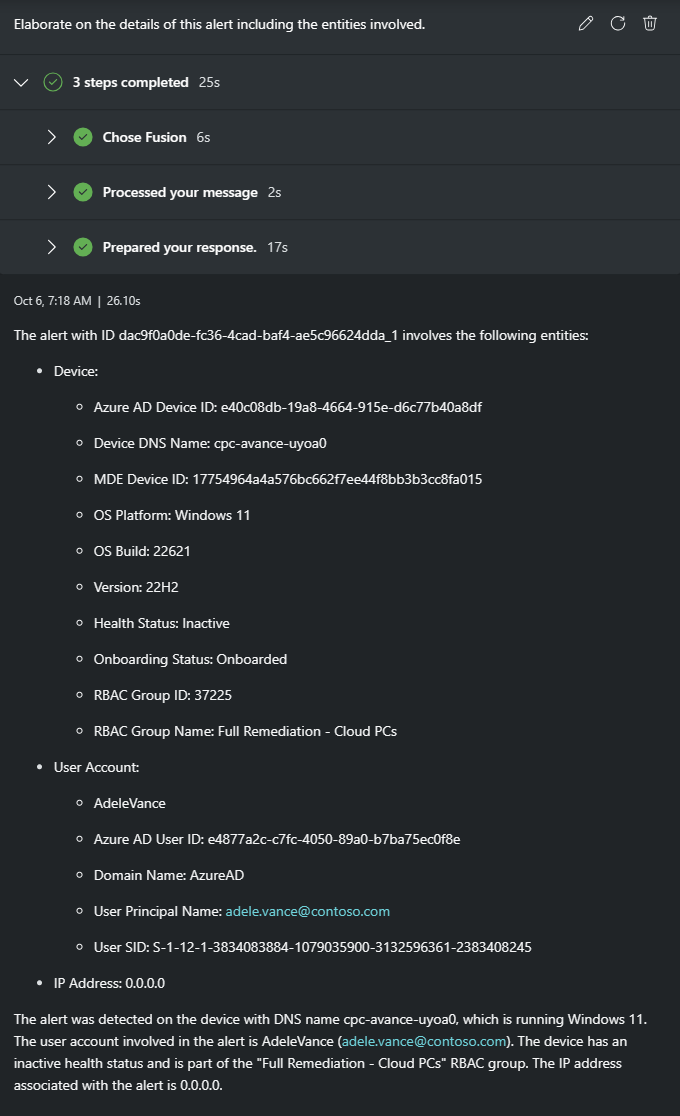
Now you have a user account and device to further investigate. In this case, you choose to understand more about the affected user before digging into the details of the attack on the device.
Get more information about this user to guide next steps. What type of actions might be next for someone with her credentials?
Prompt used:
Tell me more about the user entity.
Response:
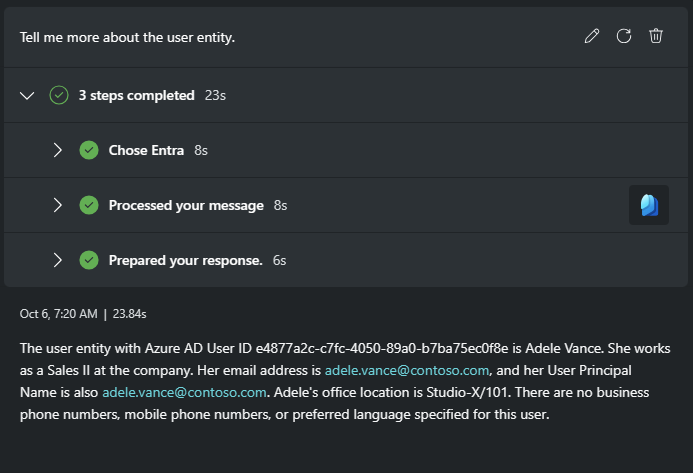
You find out this user is works in Sales. If her credential was stolen, this could affect sales data. You remember that your Sentinel workspace has an SAP solution to help detect threats there. Is this Defender alert linked to a Microsoft Sentinel incident? Your first priority is to determine if there has been any suspicious activity by this user in SAP.
Use a saved hunting query to correlate entities with Sentinel incidents.
You manually activate the suggested prompt for the Natural language to Sentinel KQL plugin to run your query.
Tip
If the query needs to be adjusted slightly, edit the prompt and re-run it. For instance, your query projected
IncidentNames, but those are simply GUIDs. You remember it's theTitlefield you really want. Simply edit the prompt and select the Re-run prompt option.
Adjusted prompt used:
Run the following KQL SecurityAlert | where Entities has "
adele.vance@contoso.com" and TimeGenerated >= datetime(10/06/2023) | join kind=inner (SecurityIncident | mv-expand SystemAlertId = AlertIds | extend SystemAlertId = tostring(SystemAlertId)) on SystemAlertId | summarize by IncidentNumber, TitleResponse:
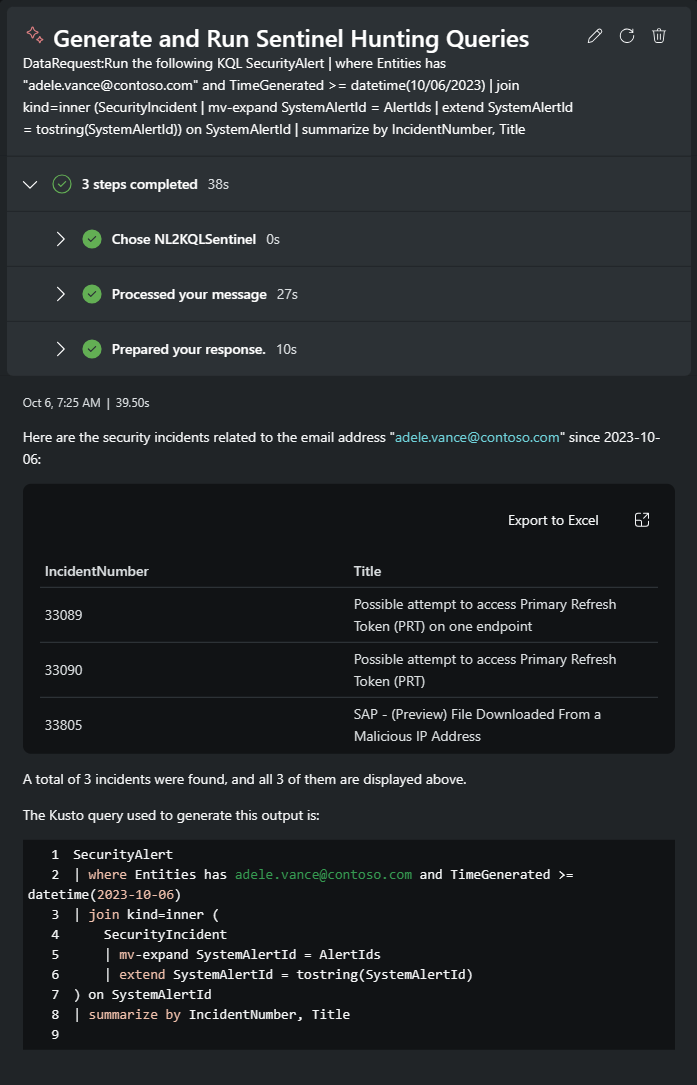
The SAP related incident is now your first priority.
Pivot your investigation to the SAP incident associated with the user from the original alert.
Prompt used:
Elaborate on Sentinel incident 33805 and give me details about the entities.
Response:
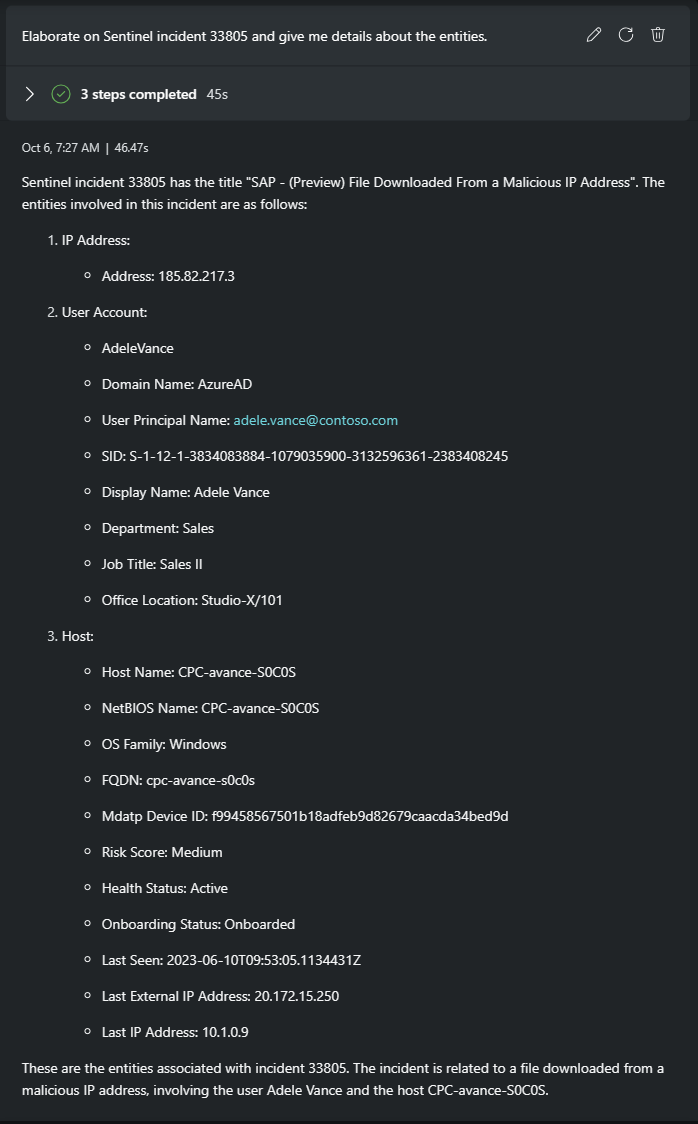
A lot of information is returned from this prompt. The malicious IP and possible exfiltration of financial data stand out as important items to investigate further.
Find out more about the IP address entity and examine how it was determined to be malicious.
Prompt used:
Give me more details about the IP address and why is it malicious?
Response:
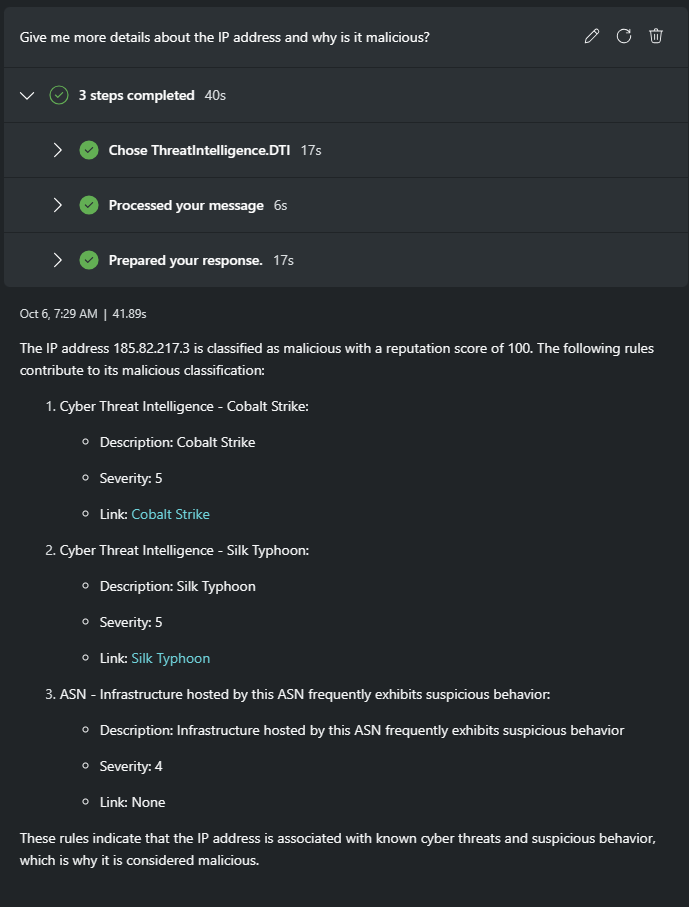
Create a summary report
Save time in the escalation process with a summary for leadership and incident response teams.
Prompt used:
Write a report based on this investigation. Lead with your assessment of the original Defender incident and whether the threat of credential theft is real. Conclude your assessment on how that threat relates to the Sentinel incident regarding the file downloaded to a malicious IP.
Response:
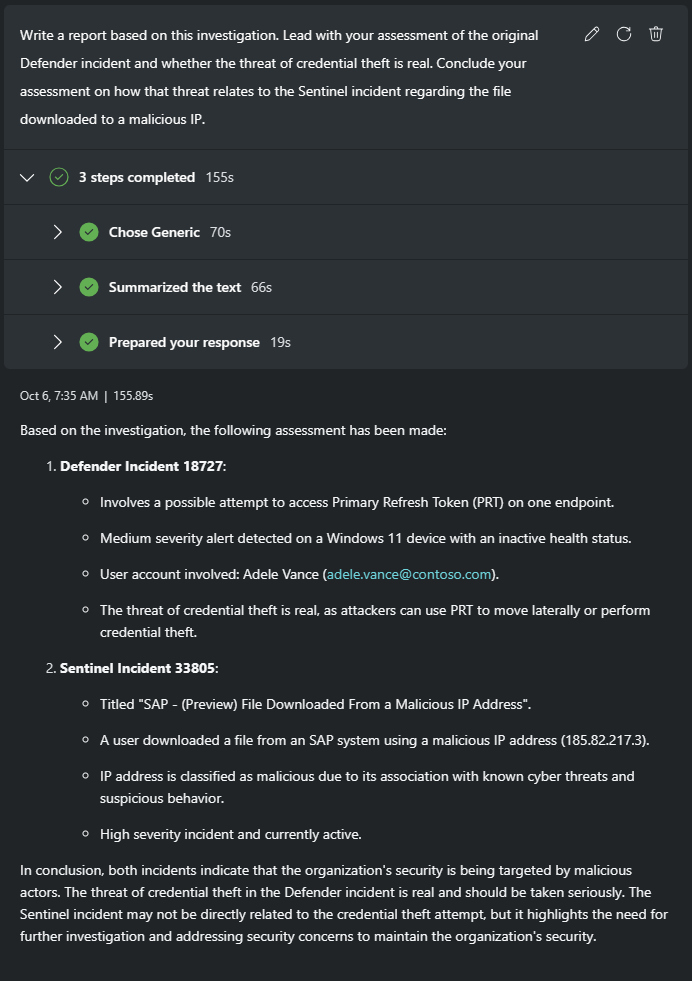
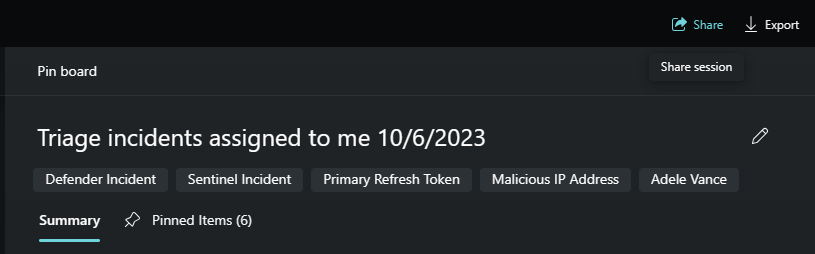
Pin the most useful prompts responses and edit the session name.
You've reached your goal and determined the assigned Microsoft Defender XDR incident is a real threat. By linking it to a Microsoft Sentinel incident involving an exfiltrated SAP file, you prepare to collaborate with your escalation team.
Conclusion
In this use case, Security Copilot helped triage an assigned incident quickly. You confirmed the alert required real action by investigating related incidents. The hunt resulted in finding an incident with an IP entity linked to finished intelligence about the threat actor and C2 tool used. With a succinct pin board, you shared the session and a summary report giving the escalation team the information they need to respond effectively.