Monitor Azure, AWS, and on-premises networks using OMS Network Performance Monitor (Preview)
Summary: Learn how to use OMS Network Performance Monitor to monitor performance across on-premises, cloud (IaaS), and hybrid networks
Hello, this is Abhave Sharma, and in this post I want to talk about how Network Performance Monitor can be used to monitor various network environments.
Modern organizations have heterogeneous network environments that have infrastructure both on premises and in a public cloud. These organizations also often use more than one cloud provider. This creates the need for a hybrid IT monitoring tool that can be used for monitoring the different network environments across clouds. OMS Network Performance Monitor works across on-premises, cloud (IaaS), and hybrid environments. It offers near real-time monitoring of network performance parameters, such as loss and latency, and localizes the source of the problem to a particular network segment or device even if the network is hosted across public cloud providers.
The solution notes the packet retransmissions and roundtrip time that is encountered for pings within or between the subnets in which the OMS agents are installed. Using synthetic transactions as a primary mechanism to detect and locate network performance bottlenecks, Network Performance Monitor can monitor the different types of networks as described in this post.
Note: Network Performance Monitor is a preview solution that’s available in the OMS solution gallery.
For more information about the capabilities of the solution, please visit this introductory blog post and the solution documentation webpage.
Monitor connectivity between different public clouds – AWS and Azure
Network Performance Monitor can monitor the performance of your IaaS resources within Azure, Amazon Web Services (AWS), and across Azure and AWS. One or more Network Performance Monitor agents need to be installed in each subnet that is to be monitored. The agents can be placed alongside an existing workload, on a new virtual machine (VM), or both. The virtual networks that you monitor can be in any region, subscription, or deployment model. The same VPN tunnel that is used to send network traffic between the virtual networks is utilized by the solution to send the synthetic transactions.
Note: Ensure that the applicable security groups in the virtual networks do not contain any Access Control List (ACL) rules that deny network traffic to the VM instances that you want to monitor in that virtual network.
The following illustration shows monitoring between an AWS Virtual Private Cloud (VPC) and an Azure Virtual Network. The 10.11.0.0/16 subnet on the AWS VPC is connected to the 12.13.0.0/16 subnet on the Azure Virtual Network through a VPN tunnel. One agent is placed in a VM in 10.11.0.0/16 and another agent is placed in a VM in 12.13.0.0/16. The agents detect the respective subnets that they are placed in and exchange pings through the VPN tunnel to monitor the connectivity between the two clouds.
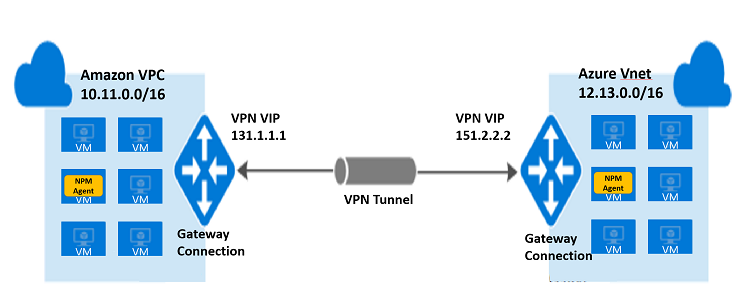
Monitor network performance across Azure/AWS and on-premises
Monitoring the network performance of AWS Virtual Private Cloud/Azure Virtual Network to an on-premises network is similar to monitoring the performance across virtual networks previously described. One or more Network Performance Monitor agents needs to be installed in all the subnets in the cloud and on-premises networks. The available network connection—VPN, ExpressRoute, or Direct Connect—is utilized for monitoring.
The following diagram shows monitoring across a virtual network in Azure and two on-premises networks in different locations. The 10.11.0.0/16 subnet in VNet1 is connected to the two subnets, 20.0.0.0/16 and 20.1.0.0/16, in on-premises location, LocalSite1, through a VPN tunnel. The 10.11.0.0/16 subnet is also connected to two other subnets, 20.2.0.0/16 and 20.3.0.0/16, in another on-premises location, LocalSite2, through another VPN tunnel. One agent each has been placed in 10.11.0.0/16, 20.0.0.0/16, 20.1.0.0/16, 20.2.0.0/16, and 20.3.0.0/16. The agent in 10.11.0.0/16 exchanges pings with the agent in 20.0.0.0/16 and the agent in 20.1.0.0/16, through the VPN tunnel between VIP 131.1.1.1 and 128.8.8.8, to monitor the connectivity between VNet1 and LocalSite1. In a similar manner, the agent in 10.11.0.0/16 also exchanges pings with the agent in 20.2.0.0/16 and the agent in 20.3.0.0/16, through the VPN tunnel between VIP 131.1.1.1 and 139.9.9.9, to monitor the connectivity between VNet1 and LocalSite2.
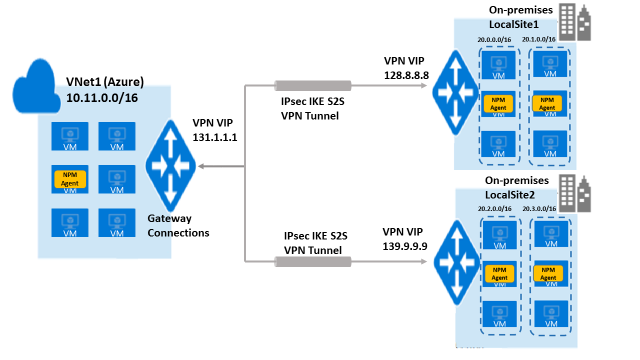
Make sure that the monitoring rules that you set when you configure Network Performance Monitor are logically correct. For example, in the previous illustration, the monitoring rules should be set for monitoring performance between VNet1-and-LocalSite1 and VNet1-and-LocalSite2, but not between LocalSite1-and-LocalSite2 because the latter will show 100% loss if there’s no connectivity between them.
Monitor connectivity between multiple datacenters or sites
A company that has a distributed infrastructure can monitor the connectivity of the branch offices in different sites. This requires installation of one OMS agent in each subnet of each branch office. If the sites or datacenters are behind a firewall, you need to make sure that the firewall allows transactions generated by Network Performance Monitor. The company’s available network connections are used for the connection between the branch offices and the headquarters, for example, this could be an existing VPN connection.
Note: In cases where connection is established through the internet, the individual hops on the internet may not be detected by the solution in any of the previous scenarios.
Monitor network connection between critical workloads
Monitor the network performance between your critical workloads by installing one or more Network Performance Monitor agents on servers that have critical workloads where you want to monitor the network performance. For example, if you intend to keep track of a network connection between a web server and a server running SQL Server, install an agent on both servers as shown in the following diagram.
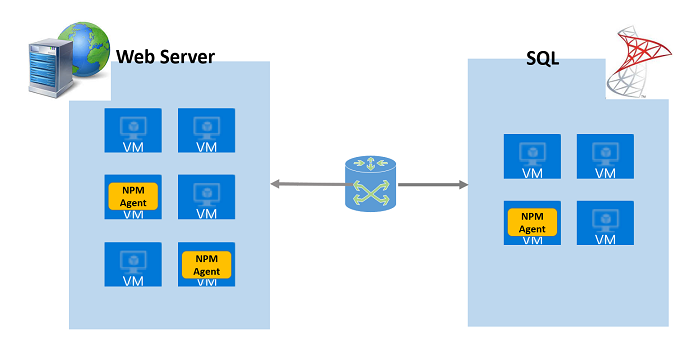
As you can see from the previously mentioned scenarios, Network Performance Monitor can be used to monitor network links in all types of environments: on-premises, Azure, AWS, private clouds, hybrid networks, and multiple sites or datacenters.
The following image shows a network-links page of Network Performance Monitor where different types of network links are being monitored by the solution in a single OMS workspace.
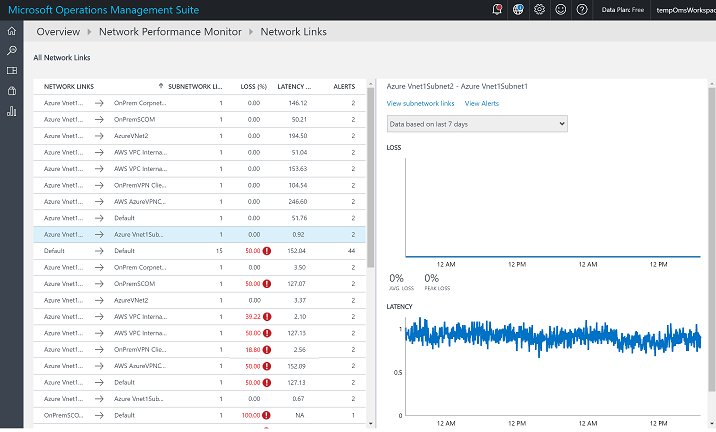
That is all I have for you in this post. Join me next time when I talk about what’s coming next with the Network Performance Monitor in OMS.
For more information about this new solution, please visit the Operations Management Suite documentation webpage or sign up for a free trial. Follow us on Twitter @MSCloudMgmt.
Abhave SharmaProgram Manager, Microsoft Operations Management Team
Comments
- Anonymous
September 04, 2016
Awesome, and also, I want to monitor Network Performance between Azure Virtual Machine and Azure SQL Database.- Anonymous
September 09, 2016
@Yoshihiro,Currently NPM can be used to monitor network performance across IaaS resources in public cloud. We will be adding the capability of monitoring PaaS resources very soon, post which you would be able to monitor network performance between Azure Virtual Machine and Azure SQL Database. We will inform you once we are there.
- Anonymous
- Anonymous
September 07, 2016
would love to monitor network between AWS, Azure and onprem without the need of a VPN