Remote Desktop Gateway and Microsoft Entra Multifactor Authentication Server using RADIUS
Often, Remote Desktop (RD) Gateway uses the local Network Policy Services (NPS) to authenticate users. This article describes how to route RADIUS requests out from the Remote Desktop Gateway (through the local NPS) to the Multifactor Authentication Server. The combination of Microsoft Entra Multifactor Authentication and RD Gateway means that your users can access their work environments from anywhere while performing strong authentication.
Since Windows Authentication for terminal services isn't supported for Server 2012 R2, use RD Gateway and RADIUS to integrate with MFA Server.
Install the Microsoft Entra Multifactor Authentication Server on a separate server, which proxies the RADIUS request back to the NPS on the Remote Desktop Gateway Server. After NPS validates the username and password, it returns a response to the Multifactor Authentication Server. Then, the MFA Server performs the second factor of authentication and returns a result to the gateway.
Important
In September 2022, Microsoft announced deprecation of Microsoft Entra Multifactor Authentication Server. Beginning September 30, 2024, Microsoft Entra Multifactor Authentication Server deployments no longer service multifactor authentication (MFA) requests, which could cause authentications to fail for your organization. To ensure uninterrupted authentication services and to remain in a supported state, organizations should migrate their users’ authentication data to the cloud-based Microsoft Entra Multifactor Authentication service by using the latest Migration Utility included in the most recent Microsoft Entra Multifactor Authentication Server update. For more information, see Microsoft Entra Multifactor Authentication Server Migration.
To get started with cloud-based MFA, see Tutorial: Secure user sign-in events with Microsoft Entra Multifactor Authentication.
If you use cloud-based MFA, see how to integrate with RADIUS authentication for Microsoft Entra Multifactor Authentication.
Prerequisites
- A domain-joined Microsoft Entra Multifactor Authentication Server. If you don't have one installed already, follow the steps in Getting started with the Microsoft Entra Multifactor Authentication Server.
- An existing configured NPS Server.
- A Remote Desktop Gateway that authenticates with Network Policy Services.
Note
This article should be used with MFA Server deployments only, not Microsoft Entra Multifactor Authentication (Cloud-based).
Configure the Remote Desktop Gateway
Configure the RD Gateway to send RADIUS authentication to an Microsoft Entra Multifactor Authentication Server.
- In RD Gateway Manager, right-click the server name and select Properties.
- Go to the RD CAP Store tab and select Central server running NPS.
- Add one or more Microsoft Entra Multifactor Authentication Servers as RADIUS servers by entering the name or IP address of each server.
- Create a shared secret for each server.
Configure NPS
The RD Gateway uses NPS to send the RADIUS request to Microsoft Entra Multifactor Authentication. To configure NPS, first you change the timeout settings to prevent the RD Gateway from timing out before completing the two-step verification. Then, you update NPS to receive RADIUS authentications from your MFA Server. Use the following procedure to configure NPS:
Modify the timeout policy
- In NPS, open the RADIUS Clients and Server menu in the left column and select Remote RADIUS Server Groups.
- Select the TS GATEWAY SERVER GROUP.
- Go to the Load Balancing tab.
- Change both the Number of seconds without response before request is considered dropped and the Number of seconds between requests when server is identified as unavailable to between 30 and 60 seconds. (If you find that the server still times out during authentication, you can come back here and increase the number of seconds.)
- Go to the Authentication/Account tab and check that the RADIUS ports specified match the ports that the Multifactor Authentication Server is listening on.
Prepare NPS to receive authentications from the MFA Server
- Right-click RADIUS Clients under RADIUS Clients and Servers in the left column and select New.
- Add the Microsoft Entra Multifactor Authentication Server as a RADIUS client. Choose a Friendly name and specify a shared secret.
- Open the Policies menu in the left column and select Connection Request Policies. You should see a policy called TS GATEWAY AUTHORIZATION POLICY that was created when RD Gateway was configured. This policy forwards RADIUS requests to the Multifactor Authentication Server.
- Right-click TS GATEWAY AUTHORIZATION POLICY and select Duplicate Policy.
- Open the new policy and go to the Conditions tab.
- Add a condition that matches the Client Friendly Name with the Friendly name set in step 2 for the Microsoft Entra Multifactor Authentication Server RADIUS client.
- Go to the Settings tab and select Authentication.
- Change the Authentication Provider to Authenticate requests on this server. This policy ensures that when NPS receives a RADIUS request from the Microsoft Entra Multifactor Authentication Server, the authentication occurs locally. This prevents sending a RADIUS request back to the Microsoft Entra Multifactor Authentication Server, which would result in a loop condition.
- To prevent a loop condition, make sure that the new policy is ordered ABOVE the original policy in the Connection Request Policies pane.
Configure Microsoft Entra Multifactor Authentication
The Microsoft Entra Multifactor Authentication Server is configured as a RADIUS proxy between RD Gateway and NPS. It should be installed on a domain-joined server that is separate from the RD Gateway server. Use the following procedure to configure the Microsoft Entra Multifactor Authentication Server.
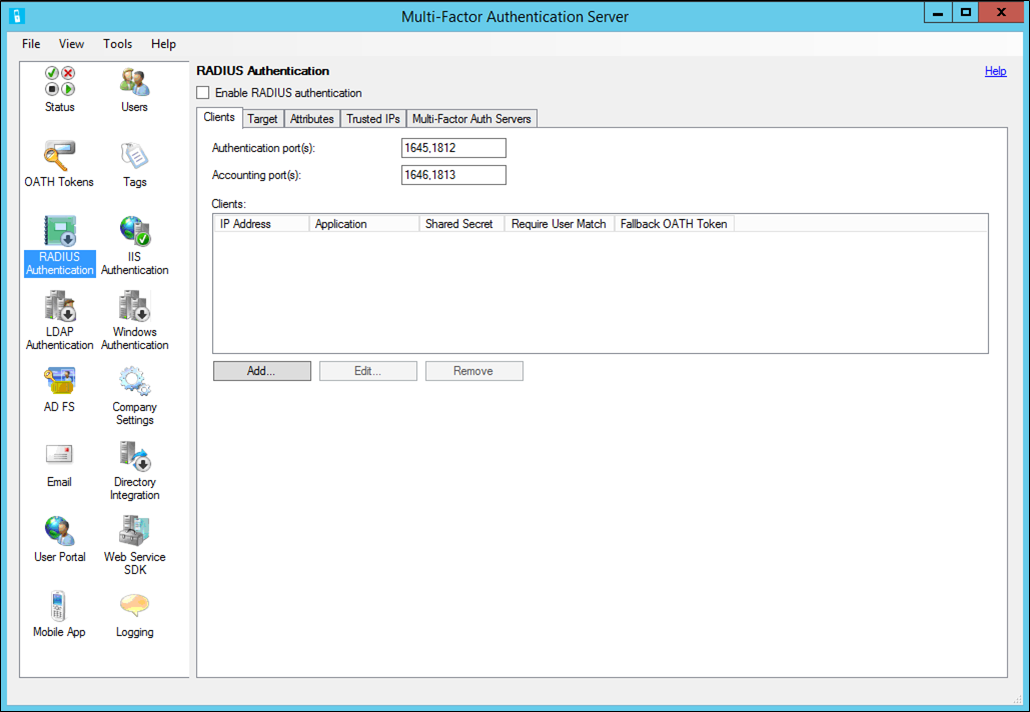
- Open the Microsoft Entra Multifactor Authentication Server and select the RADIUS Authentication icon.
- Check the Enable RADIUS authentication checkbox.
- On the Clients tab, ensure the ports match what is configured in NPS then select Add.
- Add the RD Gateway server IP address, application name (optional), and a shared secret. The shared secret needs to be the same on both the Microsoft Entra Multifactor Authentication Server and RD Gateway.
- Go to the Target tab and select the RADIUS server(s) radio button.
- Select Add and enter the IP address, shared secret, and ports of the NPS server. Unless using a central NPS, the RADIUS client and RADIUS target are the same. The shared secret must match the one setup in the RADIUS client section of the NPS server.
Next steps
Integrate Microsoft Entra Multifactor Authentication and IIS web apps
Get answers in the Microsoft Entra Multifactor Authentication FAQ