Configure Microsoft Entra multifactor authenticationServer to work with AD FS 2.0
This article is for organizations that are federated with Microsoft Entra ID, and want to secure resources that are on-premises or in the cloud. Protect your resources by using the Microsoft Entra multifactor authentication Server and configuring it to work with AD FS so that two-step verification is triggered for high-value end points.
This documentation covers using the Microsoft Entra multifactor authentication Server with AD FS 2.0. For information about AD FS, see Securing cloud and on-premises resources using Microsoft Entra multifactor authentication Server with Windows Server.
Important
In September 2022, Microsoft announced deprecation of Azure Multi-Factor Authentication Server. Beginning September 30, 2024, Azure Multi-Factor Authentication Server deployments no longer service multifactor authentication requests, which could cause authentications to fail for your organization. To ensure uninterrupted authentication services and to remain in a supported state, organizations should migrate their users’ authentication data to the cloud-based Microsoft Entra multifactor authentication service by using the latest Migration Utility included in the most recent Microsoft Entra multifactor authentication Server update. For more information, see Microsoft Entra multifactor authentication Server Migration.
To get started with cloud-based MFA, see Tutorial: Secure user sign-in events with Azure multifactor authentication.
If you use cloud-based MFA, see Securing cloud resources with Azure multifactor authentication and AD FS.
Existing customers that activated MFA Server before July 1, 2019 can download the latest version, future updates, and generate activation credentials as usual.
Secure AD FS 2.0 with a proxy
To secure AD FS 2.0 with a proxy, install the Microsoft Entra multifactor authenticationServer on the AD FS proxy server.
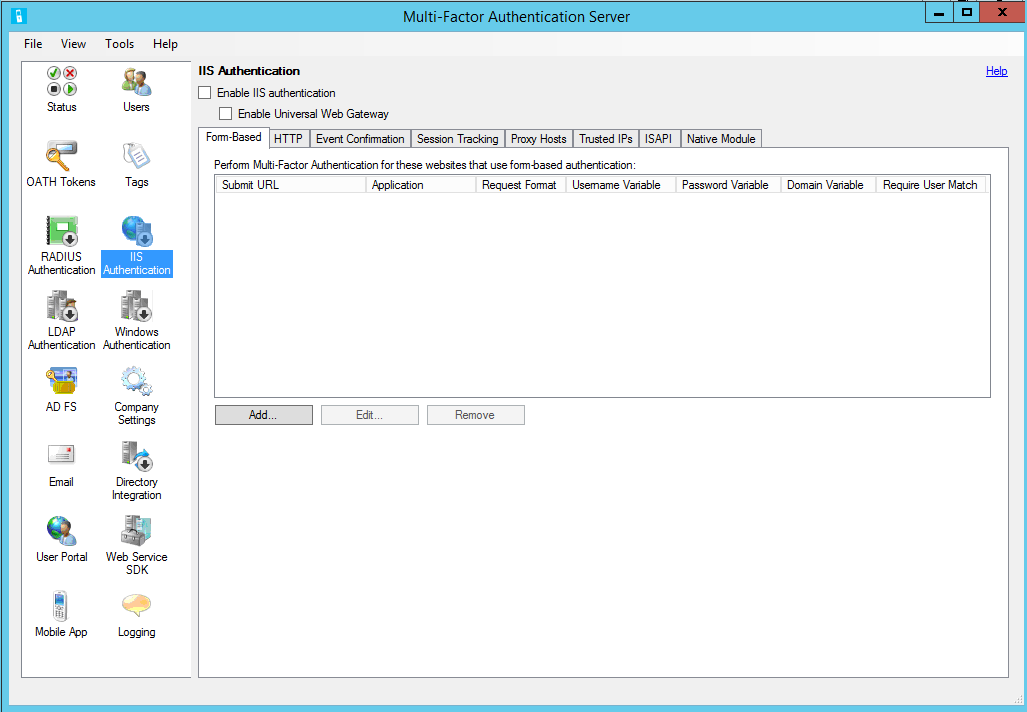
Configure IIS authentication
In the Microsoft Entra multifactor authenticationServer, select the IIS Authentication icon in the left menu.
Select the Form-Based tab.
Select Add.
To detect username, password, and domain variables automatically, enter the sign-in URL (like
https://sso.contoso.com/adfs/ls) within the Auto-Configure Form-Based Website dialog box and select OK.Check the Require Azure multifactor authentication user match box if all users are or will be imported into the Server and subject to two-step verification. If a significant number of users haven't yet been imported into the Server and/or will be exempt from two-step verification, leave the box unchecked.
If the page variables can't be detected automatically, select the Specify Manually… button in the Auto-Configure Form-Based Website dialog box.
In the Add Form-Based Website dialog box, enter the URL to the AD FS sign-in page in the Submit URL field (like
https://sso.contoso.com/adfs/ls) and enter an Application name (optional). The Application name appears in Azure multifactor authentication reports and may be displayed within SMS or Mobile App authentication messages.Set the Request format to POST or GET.
Enter the Username variable (ctl00$ContentPlaceHolder1$UsernameTextBox) and Password variable (ctl00$ContentPlaceHolder1$PasswordTextBox). If your form-based sign-in page displays a domain textbox, enter the Domain variable as well. To find the names of the input boxes on the sign-in page, go to the sign-in page in a web browser, right-select on the page, and select View Source.
Check the Require Azure multifactor authentication user match box if all users are or will be imported into the Server and subject to two-step verification. If a significant number of users haven't yet been imported into the Server and/or will be exempt from two-step verification, leave the box unchecked.
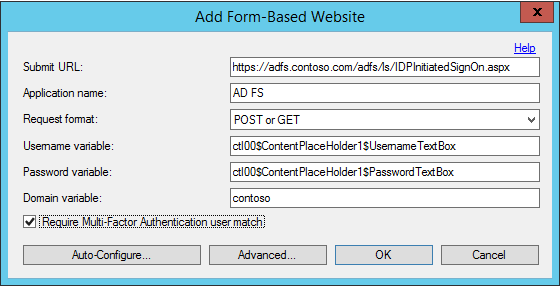
Select Advanced… to review advanced settings. Settings that you can configure include:
- Select a custom denial page file
- Cache successful authentications to the website using cookies
- Select how to authenticate the primary credentials
Since the AD FS proxy server isn't likely to be joined to the domain, you can use LDAP to connect to your domain controller for user import and pre-authentication. In the Advanced Form-Based Website dialog box, select the Primary Authentication tab and select LDAP Bind for the Pre-authentication Authentication type.
When complete, select OK to return to the Add Form-Based Website dialog box.
Select OK to close the dialog box.
Once the URL and page variables are detected or entered, the website data displays in the Form-Based panel.
Select the Native Module tab and select the server, the website that the AD FS proxy is running under (like "Default Web Site"), or the AD FS proxy application (like "ls" under "adfs") to enable the IIS plug-in at the desired level.
Select the Enable IIS authentication box at the top of the screen.
The IIS authentication is now enabled.
Configure directory integration
You enabled IIS authentication, but to perform the pre-authentication to your Active Directory (AD) via LDAP you must configure the LDAP connection to the domain controller.
Select the Directory Integration icon.
On the Settings tab, select the Use specific LDAP configuration radio button.
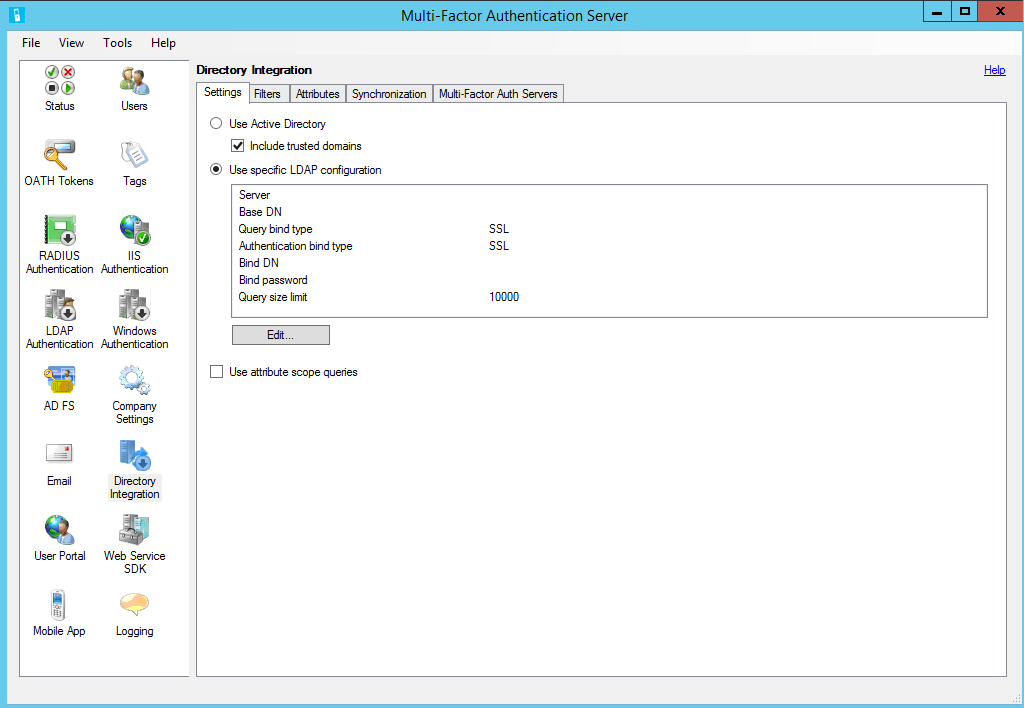
Select Edit.
In the Edit LDAP Configuration dialog box, populate the fields with the information required to connect to the AD domain controller.
Test the LDAP connection by selecting the Test button.
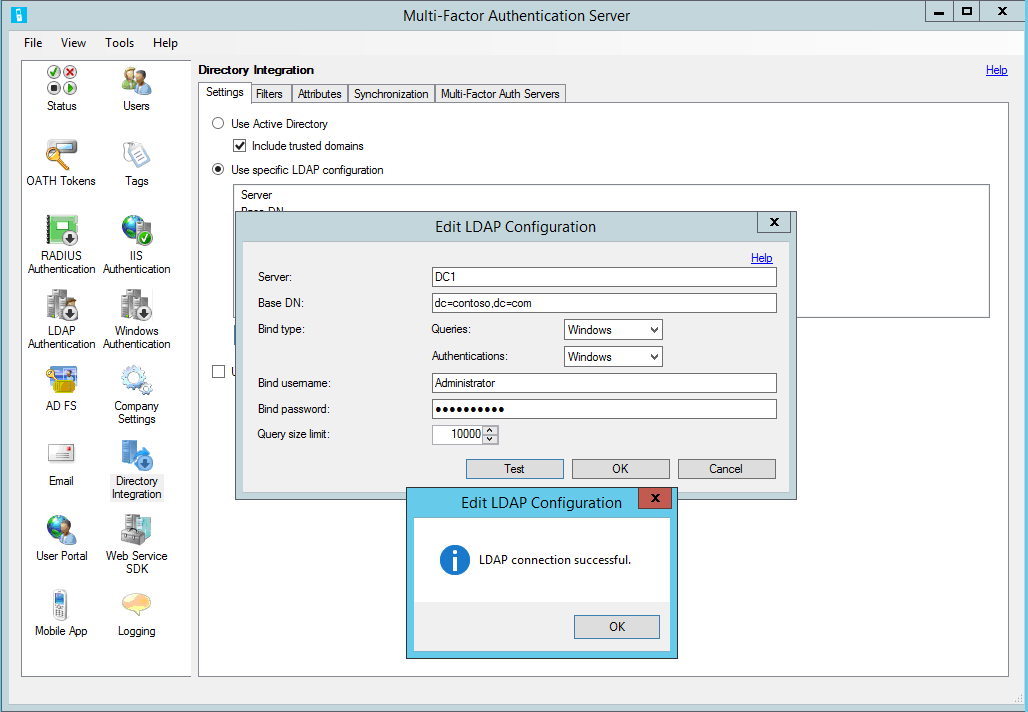
If the LDAP connection test was successful, select OK.
Configure company settings
- Next, select the Company Settings icon and select the Username Resolution tab.
- Select the Use LDAP unique identifier attribute for matching usernames radio button.
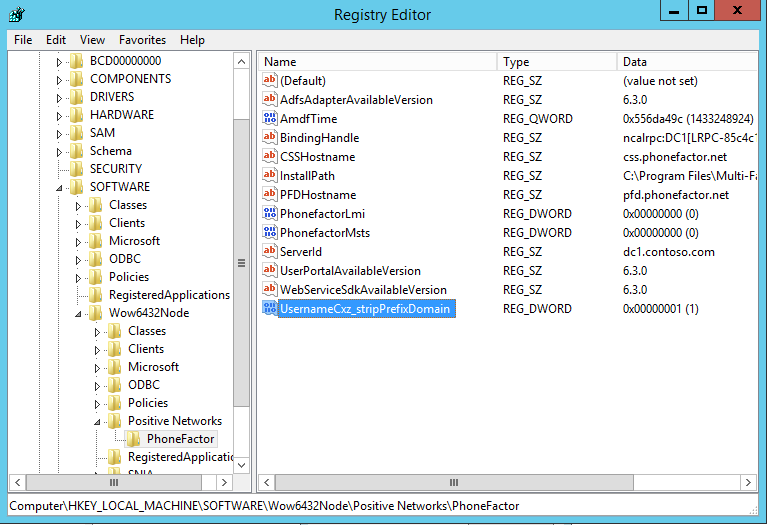
- If users enter their username in "domain\username" format, the Server needs to be able to strip the domain off the username when it creates the LDAP query, which can be done through a registry setting.
- Open the registry editor and go to HKEY_LOCAL_MACHINE/SOFTWARE/Wow6432Node/Positive Networks/PhoneFactor on a 64-bit server. If you use a 32-bit server, remove /Wow6432Node from the path. Create a DWORD registry key called "UsernameCxz_stripPrefixDomain" and set the value to 1. Azure multifactor authentication is now securing the AD FS proxy.
Make sure users are imported from Active Directory into the Server. To allow users to skip two-step verification from internal IP addresses, see the Trusted IPs.
AD FS 2.0 Direct without a proxy
You can secure AD FS when the AD FS proxy isn't used. Install the Microsoft Entra multifactor authenticationServer on the AD FS server and configure the Server per the following steps:
Within the Microsoft Entra multifactor authenticationServer, select the IIS Authentication icon in the left menu.
Select the HTTP tab.
Select Add.
In the Add Base URL dialogue box, enter the URL for the AD FS website where HTTP authentication is performed (like
https://sso.domain.com/adfs/ls/auth/integrated) into the Base URL field. Then, enter an Application name (optional). The Application name appears in Azure multifactor authentication reports and may be displayed within SMS or Mobile App authentication messages.If desired, adjust the Idle timeout and Maximum session times.
Check the Require Azure multifactor authentication user match box if all users are or will be imported into the Server and subject to two-step verification. If a significant number of users aren't yet imported into the Server and/or will be exempt from two-step verification, leave the box unchecked.
Check the cookie cache box if desired.
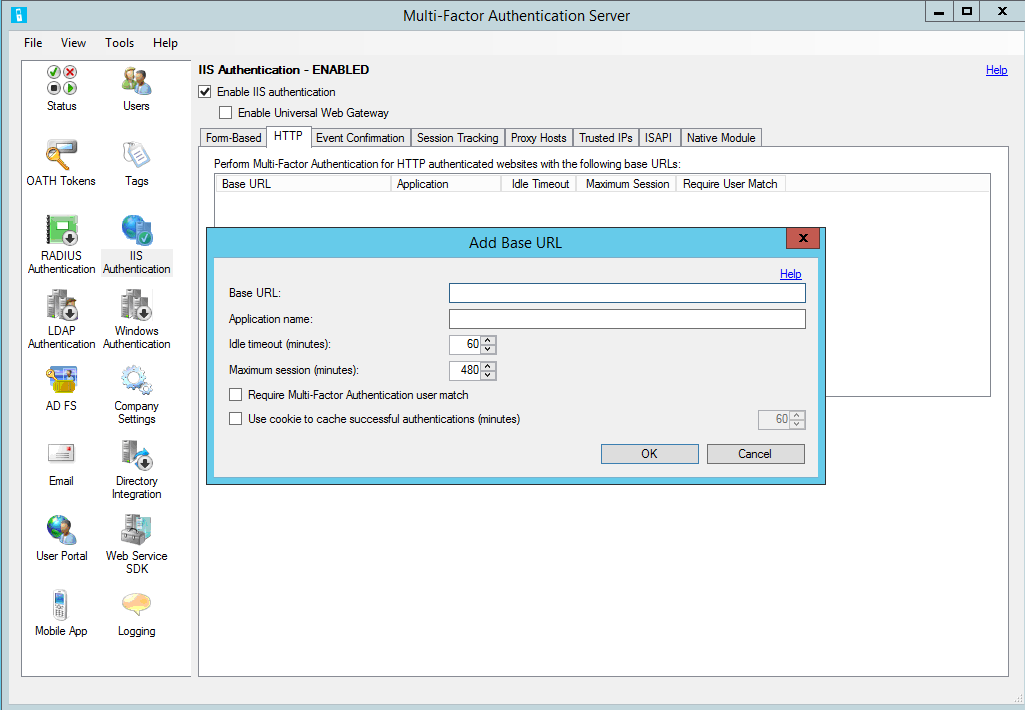
Select OK.
Select the Native Module tab and select the server, the website (like "Default Web Site"), or the AD FS application (like "ls" under "adfs") to enable the IIS plug-in at the desired level.
Select the Enable IIS authentication box at the top of the screen.
Azure multifactor authentication is now securing AD FS.
Ensure that users are imported from Active Directory into the Server. See the next section if you would like to allow internal IP addresses so that two-step verification isn't required when signing in to the website from those locations.
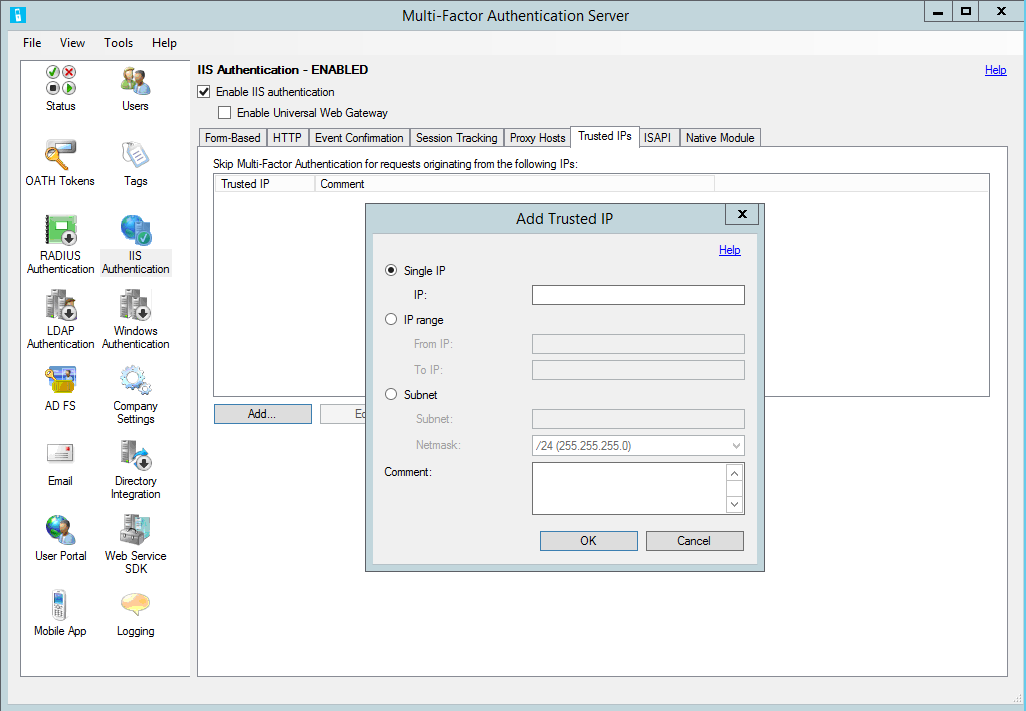
Trusted IPs
Trusted IPs allow users to bypass Azure multifactor authentication for website requests originating from specific IP addresses or subnets. For example, you may want to exempt users from two-step verification when they sign in from the office. For this, you would specify the office subnet as a Trusted IPs entry.
To configure trusted IPs
- In the IIS Authentication section, select the Trusted IPs tab.
- Select the Add… button.
- When the Add Trusted IPs dialog box appears, select one of the Single IP, IP range, or Subnet radio buttons.
- Enter the IP address, range of IP addresses, or subnet that should be allowed. If entering a subnet, select the appropriate Netmask and select the OK button.